Crypto Scam App Disguised as WalletConnect Drains $70K
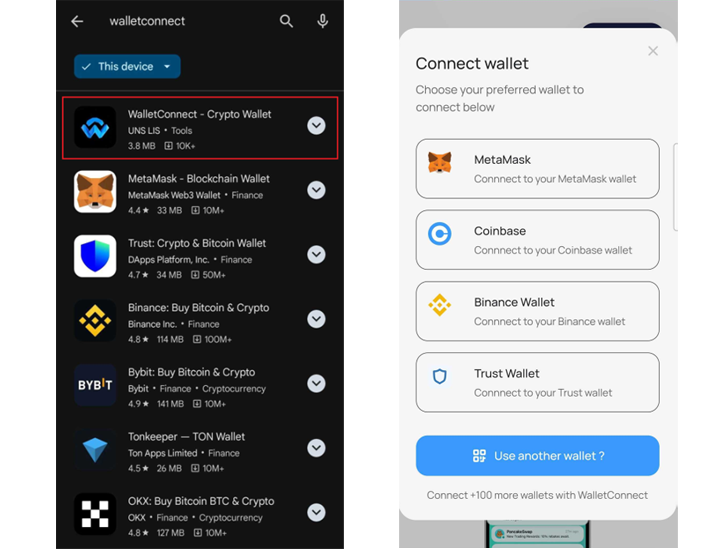
- An app mimicking the legitimate WalletConnect went undetected on the Play Store.
- Over 150 victims were lured via fake reviews and high-rank search results.
- The cybercriminals managed to steal around $70,000 in a five-month campaign.
A malicious Android app masqueraded as the legitimate WalletConnect open-source protocol on the Google Play Store, enabling its creators to siphon approximately $70,000 in cryptocurrency from victims over nearly five months, according to Check Point cybersecurity researchers.
Using names like "Mestox Calculator" and "WalletConnect - DeFi & NFTs," it tricked over 150 victims into downloading it by leveraging fake reviews and consistent branding to rank high in search results.
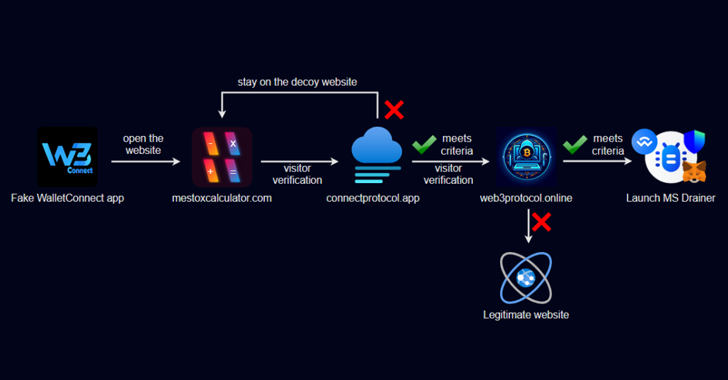
Upon installation, the app redirected users to a fake website designed to mimic Web3Inbox based on their IP address and User-Agent string. Users visiting from desktops were directed to legitimate sites to evade detection.
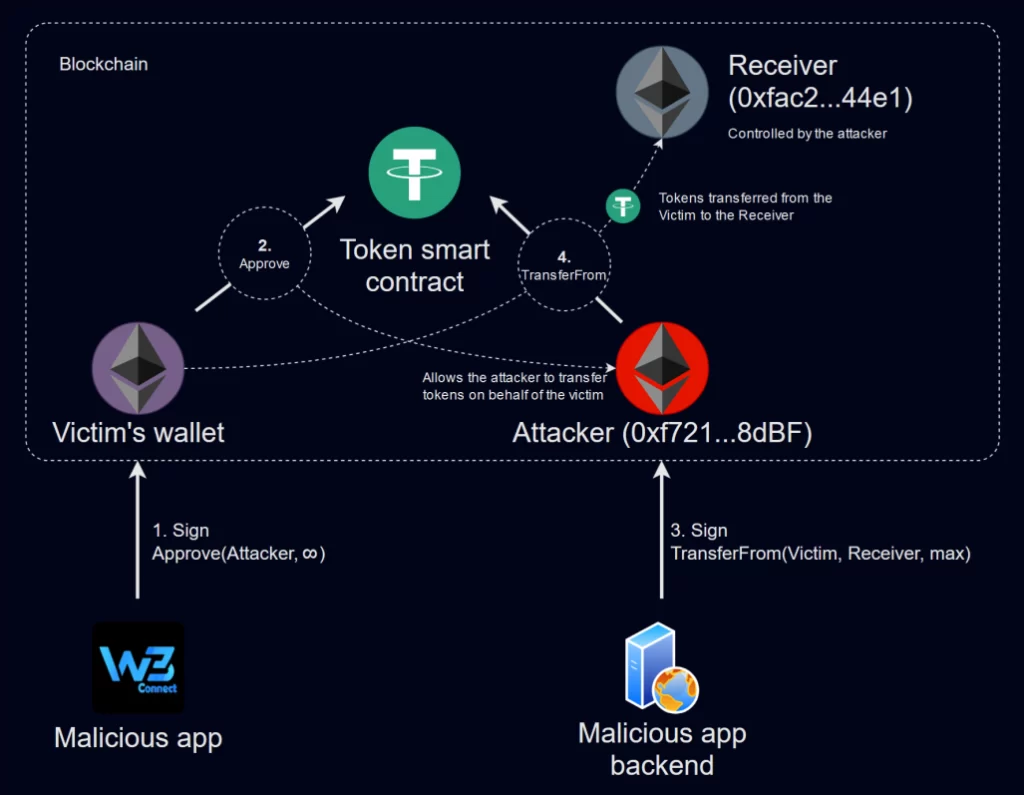
The core malware component, MS Drainer, deceptively prompted users to connect their wallets and sign transactions, subsequently transmitting data to a command-and-control server. This enabled attackers to execute malicious transactions and transfer funds to their addresses.
Victim tokens were transferred to a wallet controlled by the attackers. Continued asset drainage is possible unless victims revoke withdrawal permissions from their wallets.
The malicious app was linked to a developer named UNS LIS, who is also associated with another app, "Uniswap DeFI.” The deceptive app showed popularity in Nigeria, Portugal, and Ukraine, marking the first instance of a cryptocurrency drainer exclusively targeting mobile users.
By exploiting smart contracts and deep links rather than traditional methods like keylogging, attackers managed to stealthily drain assets from unsuspecting users.
The incident highlights the critical need for vigilance when downloading apps, emphasizing the risks associated with third-party APKs and the deceptive allure of fraudulent app reviews.
The FBI issued a warning regarding aggressive North Korean cryptocurrency hackers using social engineering, mainly targeting decentralized finance (DeFi), crypto companies, and connected entities.
In the latest news, threat actors affiliated with North Korea have been seen deploying the COVERTCATCH malware through deceptive job recruitment schemes via LinkedIn, targeting developers in DeFi and the wider Web3 sector.