Fresh ‘APT31’ Activity Surfaces, Including Russian Targets for the First Time Ever
- APT31 has apparently expanded its targeting scope and now includes Russian entities.
- The actors are using a powerful malware and dropper duo as well as spoofed websites.
- The droppers feature a valid digital signature that’s most likely stolen from somewhere.
The Chinese hacking group tracked as ‘APT31’ (aka “Zirconium” or “Hurricane Panda”) last made headlines in February when researchers at Check Point figured that the actors were using malware tools that were based on leaked NSA code. Now, it is the security research team at Positive Technologies who has an update on the most recent activity of the Chinese hackers, having tracked several emails sent by the actors in the last couple of months, targeting government entities in the United States, Canada, Russia, Belarus, and Mongolia.
According to the report, this is the first time that APT31 is confirmed to be targeting Russian entities in the five years that it has been active. In 2020, the group focused on Europe-based companies and also public agencies in Finland, France, Germany, and Norway, but its interest has shifted again as it seems.
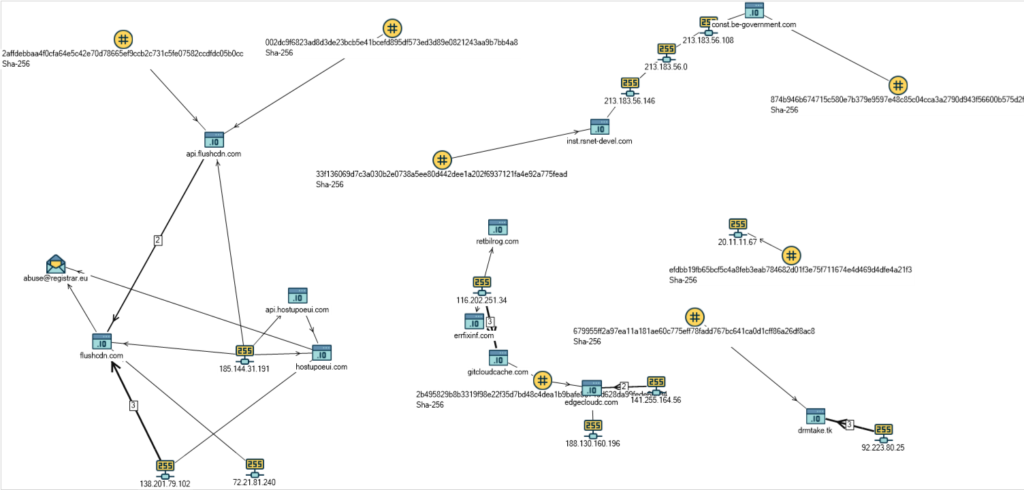
For Russia specifically, the sophisticated actors have set up a spoofing site on “inst.rsnet-devel[.]com”, which imitates the domain of Russia’s National Computer Incident Response & Coordination Center. This is a portal meant to collect reports about cyber-incidents from companies, provide aid and advice, and coordinate response operations. The servers infrastructure that Positive Technologies was able to map is given below.
The malware that’s dropped onto the targets' systems is dropped through DLL sideloading in a newly created directory at “C:\ProgramData\Apacha”. It is noteworthy that the droppers are often signed with a valid digital signature that is most probably stolen.
The malware itself is similar to what was used by the group in last year’s operations and supports the following commands:
- Get information on mapped drives
- Perform file search
- Create a process, communication through the pipe
- Create a process via ShellExecute
- Create a new stream with a file download from the server
- Search for a file or perform the necessary operation via SHFileOperationW (copy, move, rename, or delete file)
- Create a directory
- Create a new stream, sending the file to the server
- Self-delete using a bat-file
Daniil Koloskov, a Senior Threat Analysis Specialist at Positive Technologies, states: