Chinese Hackers of the ‘APT31’ Had Reportedly Stolen NSA Spyware Code
- Check Point has dived deeper into old malware samples and found evidence that links APT31 and NSA code.
- The deployment of 0-day based malware was spotted in the wild years before the “Shadow Brokers” leaks.
- This research confirms previous findings and gives more details about previously undocumented exploits.
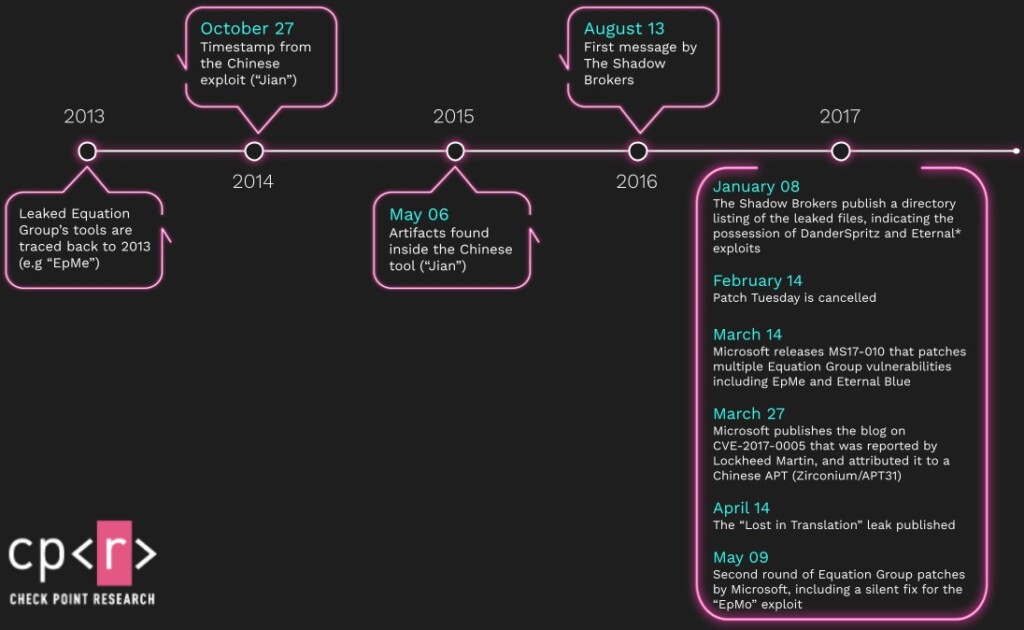
Israeli cybersecurity intelligence company Check Point has published a report explaining how Chinese state-supported hackers of the ‘APT31’ group (aka “Zirconium”) have developed a very sophisticated spyware using code they stole from NSA's Tailored Access Operations’ unit, also known as the Equation Group. The malware is dubbed as “Jian,” and it has many similarities to what was leaked in 2017, in a series of national cyberweapon exposures that irreversibly stained NSA’s public image (“Shadow Brokers” leak).
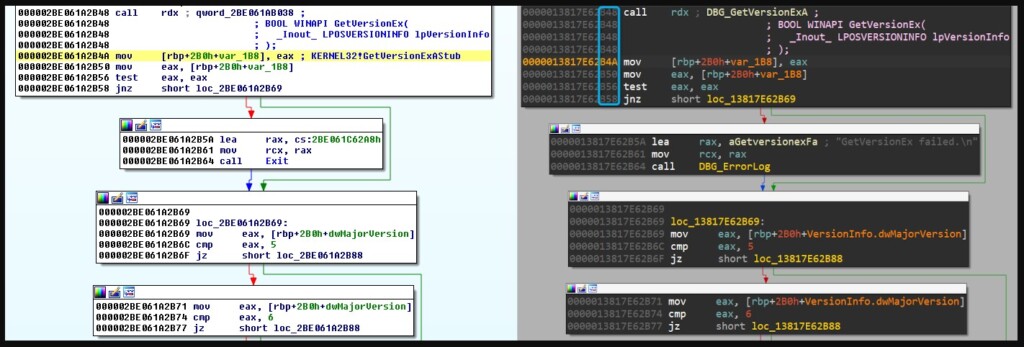
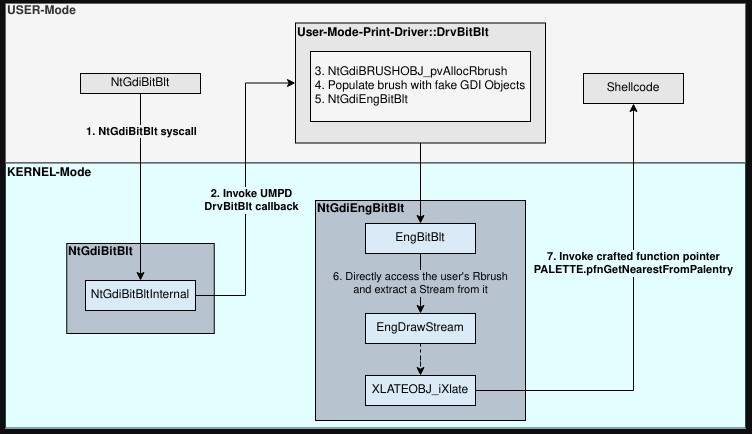
More specifically, the common ground appears to be the CVE-2017-0005, a zero-day which has been linked with “in-the-wild” APT31 attacks and was also present in the Equation Group’s “EpMe” exploit. According to the evidence presented now, the “Zirconium” hackers had access to EpMe’s specifics more than two years before the NSA leaks came to light and were used multiple times in 2014 and also in 2015. At that time, the flaw was chained with another three privilege escalation exploits on Windows, two of which were 0-days at that time.
The CVE-2017-0005 was fixed by Microsoft “silently,” as the software giant received a private tip about it from Lockheed Martin’s Computer Incident Response Team in 2017. Thus, a CVE-ID wasn’t assigned at the time of patching the flaw.
This also goes to show that if the Equation Group had shared the 0-day info with Microsoft earlier, the Chinese hackers wouldn’t have the chance to launch attacks against critical American targets. We can say that in this case, NSA’s practice placed surveillance higher than national security - without realizing it, of course.
There have been multiple reports in the past claiming that NSA lost control of its malware years before its cyber-weapons arsenal was publicly exposed in the “Shadow Brokers” leak, like this one from Symantec, which came out as far back as May 7, 2019. Thus, Check Point’s research isn’t giving us anything unheard of, but it’s detailing more exploits that haven’t been discussed before, makes connections between cloned exploits, and assigns confident attributions.
Kaspersky’s researcher Costin Raiu has commented that the latest research by Check Point looks legit, so the presented findings are generally accepted by the infosec community as valid. Of course, for the average Windows user, all this has little significance.
What it tells us is that NSA’s practices were a liability, and any palliative moves that followed aren’t enough to reverse the damage that was done in the years before 2017. That said, Check Point’s research serves as a good reminder of an old lesson.