How The “Florentine Banker” Group Managed to Divert £530,000 to Its Bank Account
- The Florentine Banker group has made a little over half a million GBP recently by tricking a company through a BEC scam.
- The actors actually managed to steal double the amount, but the emergency response of researchers saved some of the funds.
- Florentine targets English communications, and it is very diligent, methodical, and punctual.
Check Point researchers are diving deeper into a case involving the “Florentine Banker” group and their attempt to transfer £1,100,000 to their bank accounts. The incident response team caught the signs of fraud, intervened to alert the banks about the four suspicious transaction attempts, and enabled them to recover £570,000 (roughly $701,000). The remaining £530,000 (roughly $652,000) were marked as “lost funds,” even though they are not stuck in transit somewhere in the gears of the banking system since this amount ended up in the hackers' pockets. So here is how they did it.
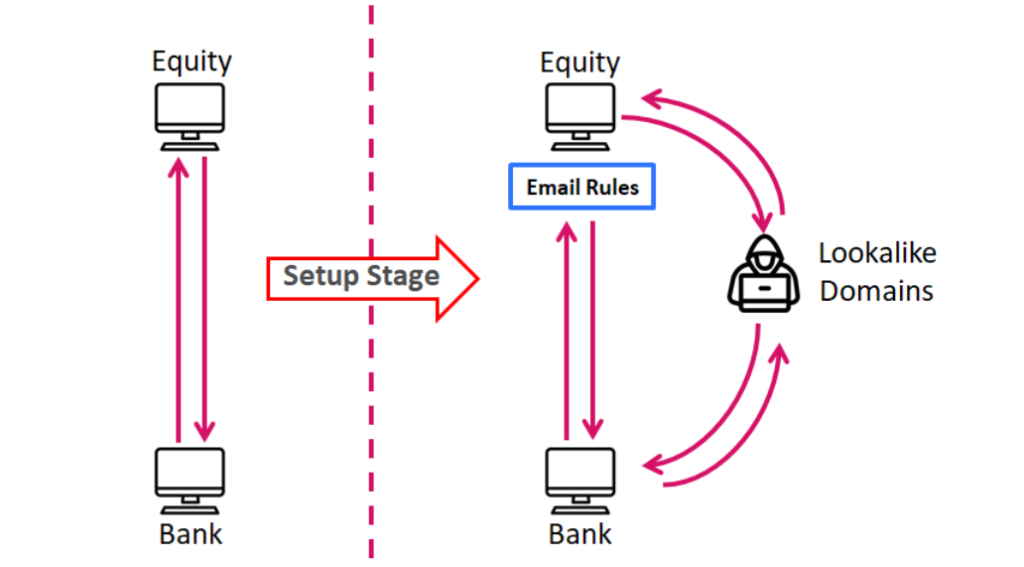
First, the group carries out a highly targeted phishing campaign against individuals who are working for the target company. Common examples would include the CEO, CFO, or other high standing employees. The main goal is to phish persons who have the authorization to execute money transactions. In this case, the group targeted two individuals and persisted for weeks, until it got a complete view of the financial aspect of the target organization. Once the attackers got their hands onto the email credentials of one of the targets, they were able to access the key representative's communications with lawyers, accountants, banks, and other fundamental employees in the company.
Source: Check Point
Next, the attackers isolated the victim by creating malicious mailbox rules, starting the “man in the middle” attack phase. They set up lookalike domains to trick the victim into believing he/she is visiting the banking services or the accounting firm portal, etc. They used these spoofed domains to send their emails from, either creating new conversations or infiltrating into existing ones. Having done all that, they were ready to ask for money, so they generated wire transfer requests, or intercepted legitimate ones. In the case of the Florentine Banker, they used Hong Kong and UK-based bank accounts to funnel the funds.
Source: Check Point
The attackers were ready to fix things if the bank rejected the transaction due to currency or beneficiary name mismatching. Florentine moved quickly when such problems appeared and managed to work their way through the approval of the four transactions. As for the background of the actors, they only target English correspondence and mainly companies from the United States. They ignored Hebrew email threads, although these contained valuable information. It is noteworthy that the Florentine Banker group was serious about this latest heist, working Monday through Friday for two months. If you want to ensure that BEC scammers are not tricking you, call the person who is to receive the payment and verify the details before you proceed.