“FinSpy” Is Back to Targeting Egyptian Organizations and Activists
- German spyware “FinSpy” is actively used in Egypt against organizations and activists.
- The newer samples analyzed demonstrate high-level obfuscation and modular action.
- The systems that are targeted by FinSpy now include Windows, macOS, Linux, and Android.
It’s been a while since we last reported about surveillance operations in Egypt, but this doesn’t mean the local regime has given up trying to dip its nose into the communications of activists and organizations. An Amnesty International report comes to confirm this by exposing the details of a recent campaign involving the deployment of “FinSpy” spyware, targeting Linux and macOS computers.
FinSpy, also known as “FinFisher,” is a German-made piece of spyware whose use by oppressive regimes in Egypt has been well-documented. It exploits highly-targeted vulnerabilities like the “CVE-2017-8759” on the Microsoft.NET Framework. In this case, however, the target OSes are Linux and macOS, so FinSpy has to come with new tricks to address this, and it does.
The new malware samples captured by Amnesty International are heavily obfuscated to evade detection, use the aplib compression library, store the AES keys in the binary, hide the MD5 hash in the configuration files, and eventually attempt to gain root execution privileges. As for the communication, this takes place through HTTP Post requests, and are base64 encoded in order to avoid raising any network traffic security flags.
Source: Amnesty
Source: Amnesty
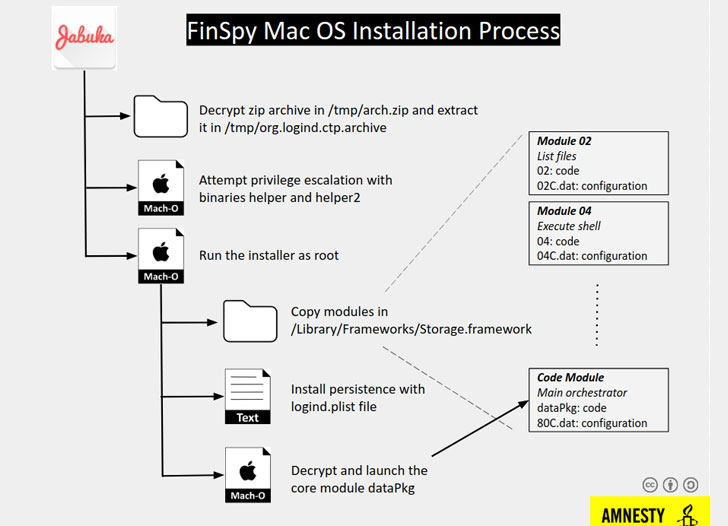
The files used for the initial infection are “Jabuka.app” for macOS and a PDF document for Linux. On Windows, the actors are using the “wrar571.exe”, and on Android, they try to plant “WIFI.apk.” Of course, these are just from the samples captured between April and November last year, so the hackers may now use different filenames.
The modules used in the Linux and the macOS samples are almost identical, with the only difference being that there’s one more module responsible for the extraction of data and the recording of Skype conversations in Mac.
Other module functions include the following:
- File listing
- Shell command execution
- Task scheduling
- Audio recording
- Keylogging
- Recording of modified files
- Recording of accessed files
- Recording of deleted files
- Virtual keyboard keylogging
- Camera recording
- Screen recording
- Email stealing (works on Apple Mail and Thunderbird)
- WiFi network information collection
- Remote device file listing
- C&C communications cryptography
Source: Amnesty
As for the Android payload, this one comes with four layers of obfuscation that haven’t been observed in previously analyzed versions. These would be a Java-based naming method, string encoding, control flow graph breakage, and littering of the code with numerous dummy calls.