February’s ‘Patch Tuesday’ Fixes 12 Critical Vulnerabilities on Windows
- This month’s patches for Windows and Adobe software have landed, so it’s time to apply them.
- Microsoft has fixed 12 critical Windows flaws and another 87 important, while Adobe has pushed hundreds of fixes too.
- Users are advised to apply the patches as soon as possible, as these are important security updates.
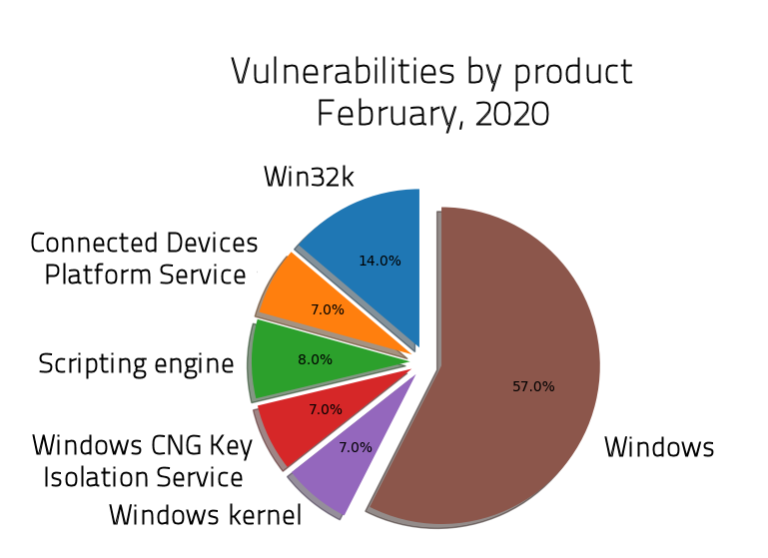
Microsoft has released this month’s patch which fixes 12 critical vulnerabilities, another 87 that are flagged as important, and two which were left unclassified. As shown in the following diagram, more than half of the fixes concern Windows, a notable 14% fixes problems in Win32k, 8% concern the scripting engine, while the kernel, the connected devices platform service, and the Windows CNG Key isolation service have also received attention this time. As for the types of vulnerabilities, 54% concern elevation of privilege problems, 18% enable hackers to conduct remote code execution attacks, and 17% have to do with information disclosure issues.
Source: Sophos News
Here are the 12 vulnerabilities that have been classified as “critical”:
- CVE-2020-0673, CVE-2020-0674, CVE-2020-0710, CVE-2020-0711, CVE-2020-0712, CVE-2020-0713, and CVE-2020-0767 – Memory corruption vulnerabilities in the Microsoft scripting engine. These flaws introduce the possibility of memory corruption, leading to arbitrary code execution.
- CVE-2020-0681 and CVE-2020-0734 – Remote code execution (RCE) vulnerabilities in Remote Desktop Protocol.
- CVE-2020-0662 – Remote code execution vulnerability in Windows 10 and some versions of Windows Server. It allows attackers to execute code with elevated permissions on the target system.
- CVE-2020-0729 – Remote code execution vulnerability in Windows that requires the use of a specially crafted. LNK file which the user must be convinced to open.
- CVE-2020-0738 – A memory corruption vulnerability in Windows Media Foundation that is based on convincing the user to open a malicious file or web page, eventually leading to memory corruption.
Monthly security updates for Windows aren’t optional, and shouldn’t be postponed for later. These vulnerabilities are now disclosed to the public, which means that malicious actors could start working on ways to take advantage of them now that they know of their existence. That said, you should immediately apply the patches and update your security software as well since it will receive the new rules for the detection of malicious activity in your system.
Together with Microsoft, Adobe has also released its patches, fixing a total of 17 CVEs just for Acrobat Reader. The 12 of these vulnerabilities are rated as critical, so applying the available patches on the software is crucially important. Besides the Reader, Adobe also released fixes for virtually their entire product range, and most notably the ColdFusion (12 fixes), Connect (9 fixes), Contribute Publishing Services, Creative Cloud Desktop (9 fixes), Dreamweaver (4 fixes), Experience Manager (11 fixes), Flash Media Server (5 fixes), Flash Player (21 fixes), Illustrator (5 fixes), InDesign (5 fixes), and Photoshop (15 fixes). For a full list of everything fixes, check out Adobe’s security bulletin.