“eCh0raix” Is Back and They Are Targeting QNAP Storage Devices
- The “eCh0raix” group has returned with a ransomware strain that is no longer possible to decode.
- The group is asking victims to pay about $500 to get their encrypted QNAP files back.
- People are advised to update the QTS, enable the Snapshot service, and use a strong admin password.
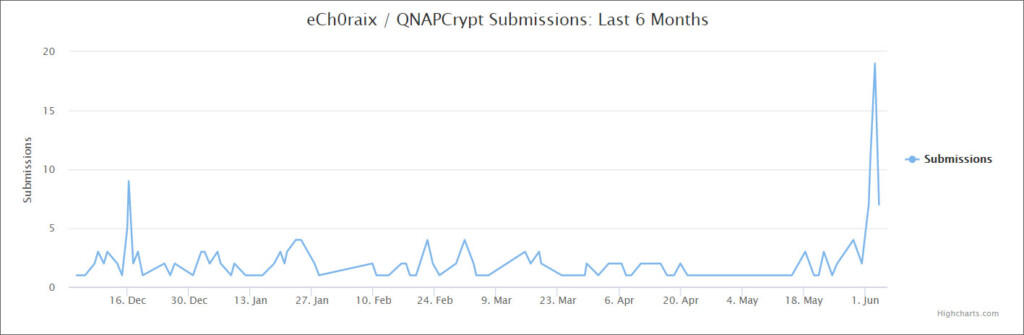
It looks like the recent warning about QNAP vulnerabilities and the sheer number of instances that remain open to exploitation have sparked the interest of actors who have remained dormant for quite some time now. One example comes from the “eCh0raix” group, which was wreaking havoc by using ransomware tools back in June 2019. While the particular actors haven’t been completely inactive since then, there’s a spike in their activity starting this month - and this is reflected in stats provided by the ID-Ransomware platform.
Source: Bleeping Computer
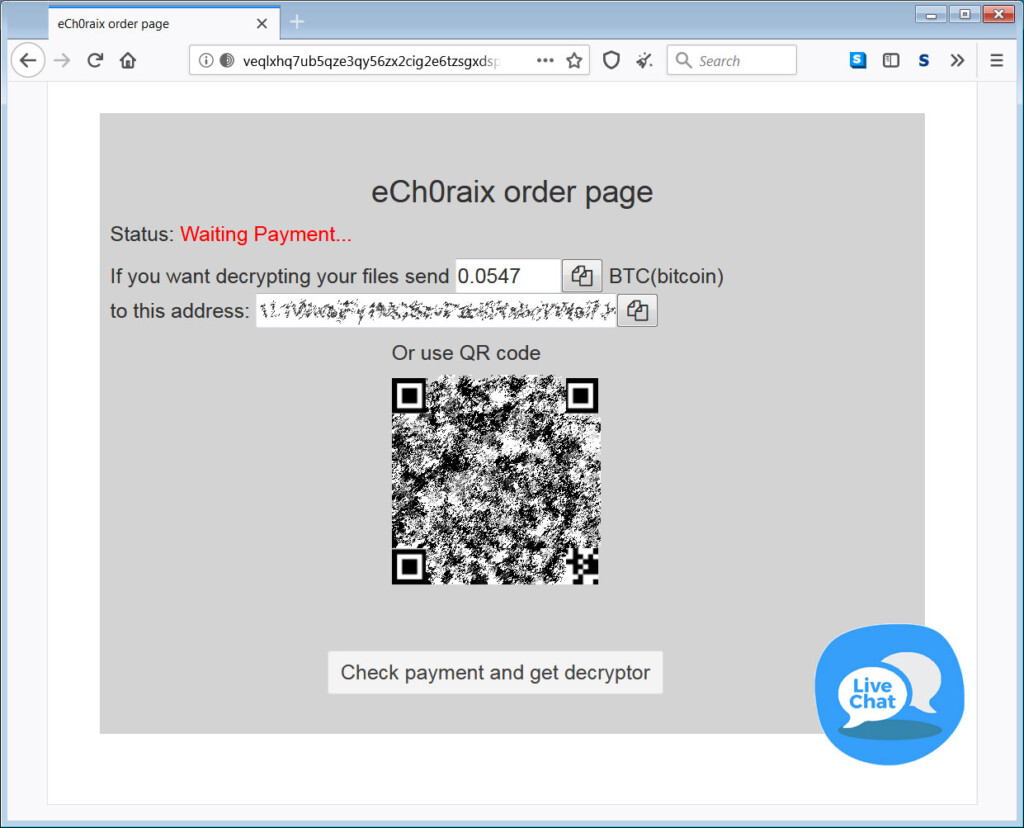
The actors are gaining access to the target QNAP device through one of the well-documented ways that were again described in detail by researcher Henry Huang last month. They then install the eCh0raix ransomware, encrypt all files, and stump the “.encrypted” extension on the locked files, leaving no margin for doubts or questions on what happened. The ransom note that is left is named “README_FOR_DECRYPT” and contains a link to a Tor payment page where the victim is urged to pay about $500 for the acquisition of a decryptor.
Source: Bleeping Computer
The sad part of the story is that the new eCh0raix strain is using an encryption algorithm that renders the files unlockable by the “white-hat” decryptor that helped victims last summer. The actors figured out their mistakes, corrected the points of weakness, and the encrypted files are no longer retrievable for free. The only way to reliably get your data back is to restore from QNAP’s Snapshot service, but of course, you’ll have to have enabled this beforehand; otherwise, there will be nothing saved to restore.
There are several things you can do to prevent eCh0raix from compromising your QNAS device. First, update the QTS to the latest available version, which will automatically plug the known vulnerabilities. Secondly, you may reset your admin password and use something powerful like a long passphrase. Thirdly, revert from using ports 443 and 8080. Finally, disable SSH and Telnet if you don’t need them, as these services allow remote actors to access your device. And, as always, connecting your NAS device only when you’re actively using it should be a standard practice to follow in general. Whatever device stays connected on the internet is running the risk of getting hacked, so limiting the connection times to the minimum required is a solid security method.