Domino’s Pizza Had 13 TB of Its Order Data Stolen and Leaked by a Hacker in India
- Millions of order details from Domino’s India have been added to a searchable database on a Tor site.
- The hacker responsible for this is the same who compromised the firm in February 2021.
- The currently accessible data includes order name, email, address, payment details, and geographic coordinates.
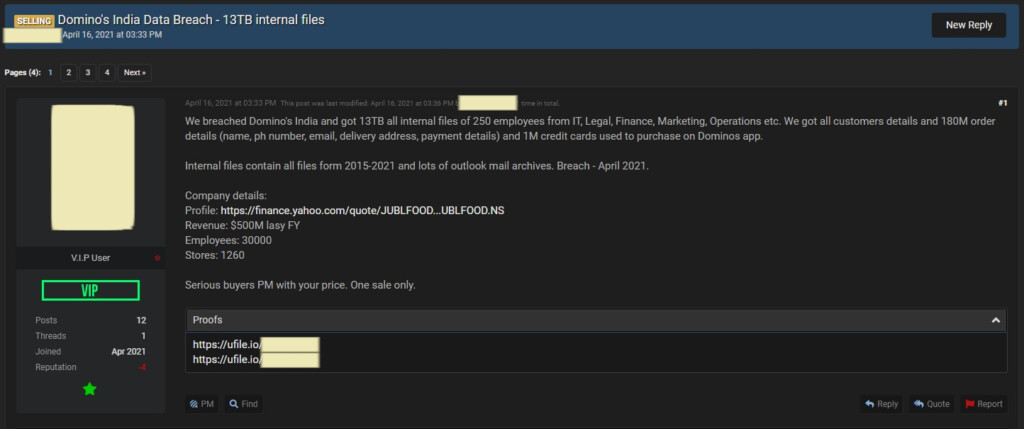
A data broker has set up a tor site where people can freely search 18 crore (180 million) orders of Domino’s India just by entering someone’s phone number or email address. The actual breach incident, which resulted in 13 TB of exfiltrated data, was announced back in April when a hacker offered the pack to a single buyer on a popular hacking forum. The compromise, though, happened in February - so in the meantime, the hackers attempted to negotiate a ransom payment with Domino’s.
According to that listing, the data stolen from Domino’s India include details about 250 employees of the company and hundreds of millions of order details, including peoples’ names, phone numbers, email addresses, delivery addresses, and payment details. In one million orders where credit cards were used to purchase products using the Domino’s app, this data is included too.
We have tested the Tor site using our own phone number, and we were able to find our order history, full delivery address details for each order specifically, order cost/price, and even the latitude and longitude of the delivery point accompanied by time stamps.
We have discussed this with researcher Rajshekhar Rajaharia who has been following the particular breach from the first moment it happened, and he has shared the following comment with us:
From what we were able to confirm in our chat with Rajaharia, this seems to be the same hacker who breached MobiKwik in February, while both data sets were given to the same reseller. Domino’s appears to have been hacked in February, denied paying a ransom. Then a reseller took the data online for a single sale and also to raise the blackmailing heat, and after another month of no deal, the Tor leak site went up.
When the hacker employed this technique against MobiKwik, the matter took huge proportions, and the victimized firm was forced to respond. The hacker retracted the data soon after the matter exploded in the media while making some ambiguous claims of regret for the damage done to MobiKwik. This raised our suspicion about the hacker having finally reached a secret agreement with the company, but this was obviously never confirmed by either party.
What we see now is the hacker hoping for a repeat of the same outcome, putting the privacy of millions of Indians a few clicks away in order to achieve it. Hopefully, we won't see any statements that underestimate people's intelligence this time.
We received a comment from Mr. Prakash Bell, Head of Customer Success and SE Lead, India & SAARC, Check Point Software Technologies: