Chrome 76 Still Not Able to Keep Users Private in Incognito
- Chrome 76 plugged the FileSystem API loophole, but it’s still possible to tell who’s using incognito.
- A developer published a timing attack proof of concept code that determines the browsing mode.
- Paywall websites remain capable of blocking freeloaders out of their platforms for now.
Last month, we analyzed the findings of three university researchers who showed that the incognito browsing mode means nothing as far as staying anonymous or avoiding Facebook’s and Google’s trackers is concerned. Google promised that Chrome version 76 that arrived last week would close the FileSystem API loophole, so users should treat incognito as a “private” mode again. However, a young developer has already bypassed Google’s plugging as he found a way to figure out if a person is using the mode or not. This means that the problem has not been really resolved, so we’ll have to wait at least until version 77 now.
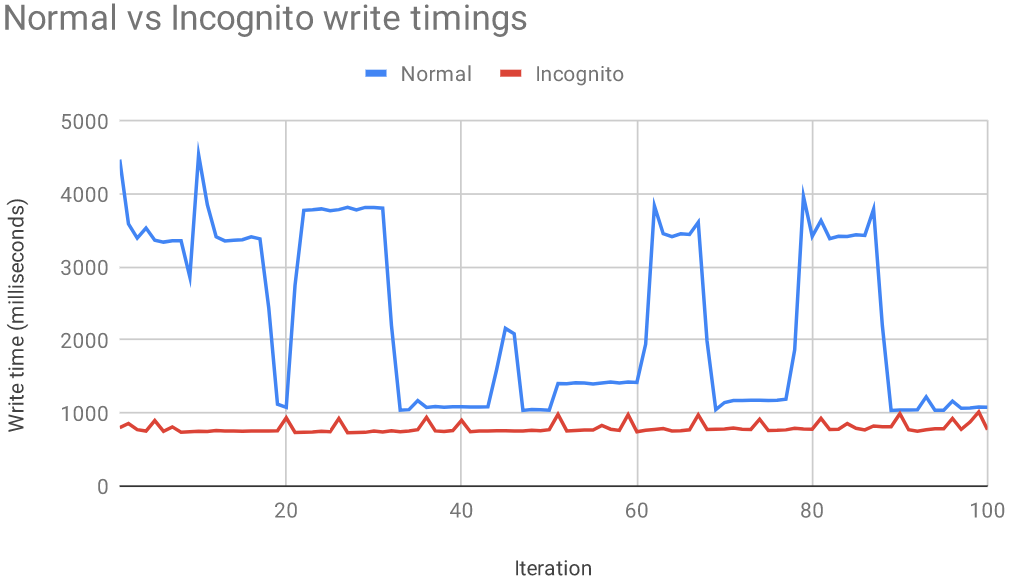
Developer Jesse Li figured that the FileSystem API writes files to the disk much faster when the user is in incognito mode. By benchmarking the write speed, websites could detect visitors who are in incognito, and they can block them if they want. Remember, there are many "paywall" websites out there that use trackers to count how many articles you’ve read on their platform, etc. These websites want to know if you’re using your browser’s incognito mode, as this undermines their business model. The write speed benchmarking offers a way to do it, so they’re safe for now.
image source: blog.jse.li
In addition to the time taken for the writing of data, the developer has also found that writes in incognito are organized more tightly, while standard mode counts more writes over a broader range. As the developer points out, one would need a couple of seconds or even a few minutes to acquire sufficient data to determine the browsing mode, depending on the amount and size of the benchmark data packets. Moreover, the benchmarking process may be interrupted or even give out false positives depending on the user’s hardware, the number of simultaneously running processes, internet bandwidth, etc.
Li has also published his proof-of-concept code on GitHub and has proposed several mitigation methods including the storing of metadata in memory and the encryption of the files on the disk. However, the remnant metadata of this process would still indicate the use of incognito mode, so the best way to deal with the problem is to remove the FileSystem API altogether. Google’s engineers were already aware of the possibility of timing attacks, and they know that the problematic API is only used for the detection of incognito mode right now. That said, wholly removing it makes perfect sense at this point.
Do you use Chrome’s incognito mode, or do you not even bother? Let us know in the comments down below, or on our socials, on Facebook and Twitter.