China-Linked Hacking Group Targets European Diplomatic Entities in Espionage Campaign
- Targeted espionage: A cyber-espionage campaign attributed to the China-affiliated threat actor UNC6384 has targeted diplomatic entities in Hungary and Belgium.
- Attack vector: The campaign used spear-phishing emails targeting European Commission and NATO-related events to deliver malicious files.
- Malware deployed: They deployed PlugX, a sophisticated tool used by many Chinese nation-state groups for long-term espionage and data exfiltration.
A recent cyber-espionage campaign targeting diplomatic entities in Belgium and Hungary in September and October has been identified, with incident responders attributing the activity to a China-linked threat actor tracked as UNC6384.
The attacks represent a tactical evolution for the group, leveraging refined social engineering techniques and a disclosed Windows vulnerability.
The UNC6384 Hacking Group's Modus Operandi
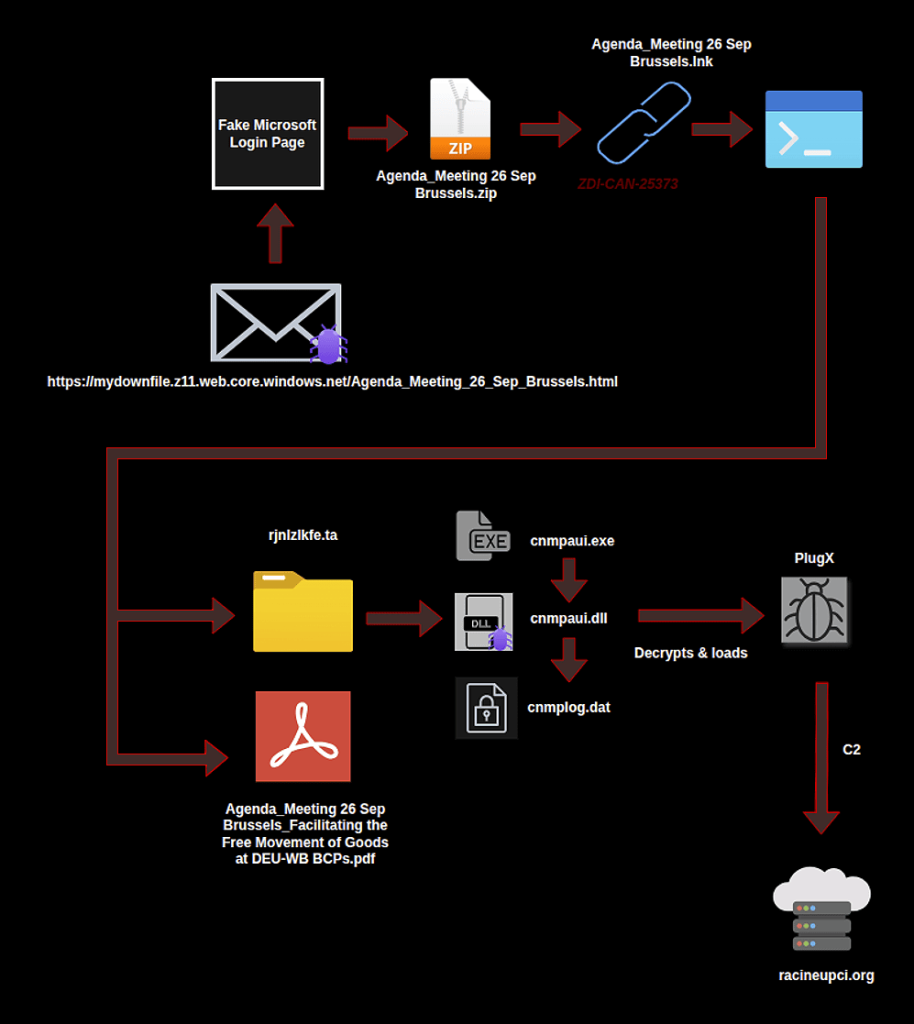
The threat actor initiated the attacks with highly targeted spearphishing emails. These emails were themed around legitimate diplomatic activities, such as European Commission meetings and NATO workshops, to entice victims into clicking embedded URLs, the latest Arctic Wolf security report said.
This action triggered a chain of events that exploited a Windows vulnerability (ZDI-CAN-25373), which is also exploited as a zero-day by multiple advanced persistent threat (APT) groups from North Korea, China, Russia, and Iran, for espionage and data theft.
This led to the deployment of the well-known PlugX remote access trojan (RAT), which has been used by multiple Chinese state-sponsored groups since 2008.
The choice of targets, which also included government departments in Serbia and other diplomatic bodies in Italy and the Netherlands, indicates a strategic interest in NATO, EU defense initiatives, and European trade policy.
The China-linked UNC6384 hacking group has demonstrated an ability to quickly weaponize publicly disclosed vulnerabilities, adopting this one into its operations just six months after its disclosure.
Implications of the PlugX Malware Deployment
PlugX is a well-known and powerful RAT that grants attackers persistent access to compromised systems. Its deployment in this campaign allowed the threat actor to establish long-term footholds within victim networks.
This level of access enables comprehensive cyberespionage activities, including the exfiltration of classified documents, real-time monitoring of policy discussions, and credential harvesting for lateral movement across diplomatic networks.
The campaign highlights ongoing diplomatic cybersecurity threats as nation-state actors continue to pursue sensitive geopolitical intelligence.
In August, GTIG attributed a recent PRC-nexus espionage campaign targeting diplomats with web traffic hijacking to deliver malware to the same UNC6384 group, a threat actor associated with TEMP.Hex (Mustang Panda).
Around the same time, CISA warned of a global Chinese state-sponsored cyber espionage campaign targeting the U.S., the U.K., Australia, Canada, New Zealand, and other nations.
PlugX was also used in 2024 by suspected Chinese DragonRank hackers in an operation that manipulated SEO rankings to direct users to malicious websites, as well as threat actor Velvet Ant while exploiting F5 load balancers for persistence in target systems.
European diplomats were also targeted in 2024 in a renewed APT29 phishing campaign, a Russian-linked cyber-espionage group also known as Cozy Bear or Midnight Blizzard.