Suspected Chinese ‘DragonRank’ Manipulates SEO Rankings to Direct Users to Malicious Websites
- Security researchers observed a threat activity cluster manipulating SEO rankings, which they named DragonRank.
- This operation aims to redirect victims in Asia and Europe to malicious websites.
- Ultimately, the cybercriminals harvest system information and deploy malicious payloads.
A new activity cluster dubbed "DragonRank" that deals in search engine optimization (SEO) poisoning was attributed to actors believed to be of Chinese origin. This operation has been observed targeting countries throughout Asia and parts of Europe by Cisco Tallos Intelligence security researchers.
Its primary objective is to compromise Windows Internet Information Services (IIS) servers hosting legitimate corporate websites and manipulate their SEO rankings.
DragonRank's tactics, techniques, and procedures (TTPs) share significant similarities with known hacking groups that employ Simplified Chinese, suggesting a potential linkage or commonality in operational methods.
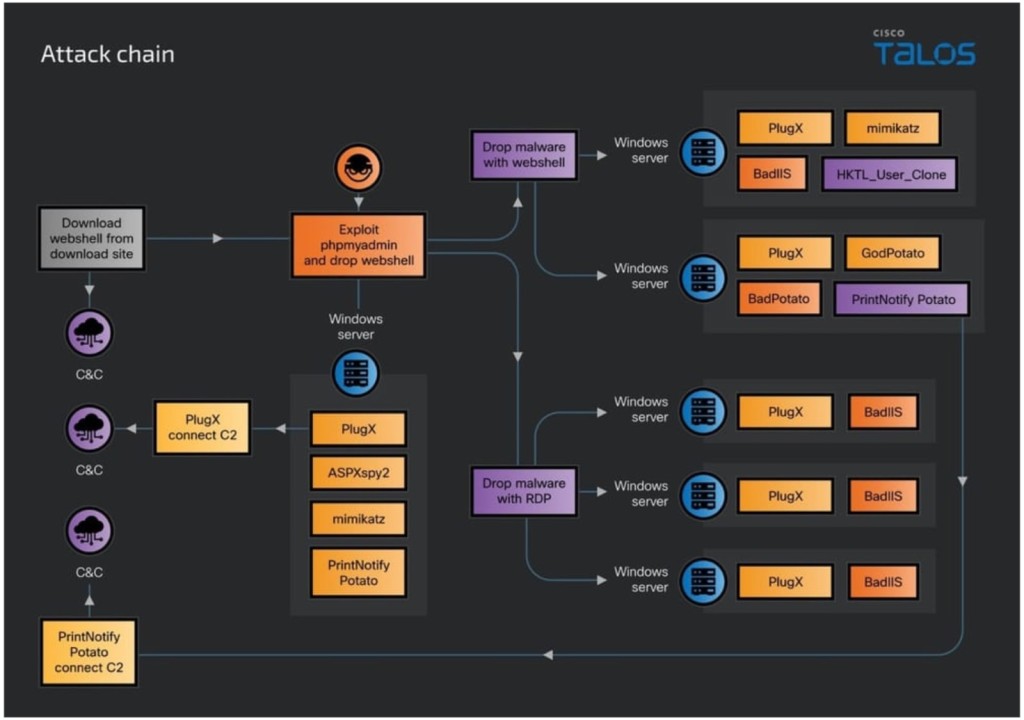
DragonRank employs web shells to execute its operations, collecting system information and deploying malicious payloads. These actions aim to infiltrate IIS servers across various sectors, including jewelry, media, research services, and healthcare.
The group's core focus is deploying BadIIS malware, which targets search engine crawlers and disrupts the SEO of affected websites. To achieve this, DragonRank exploits vulnerabilities within web application services such as phpMyAdmin and WordPress, among others.
Upon gaining access, the perpetrators deploy a web shell to collect system data, execute malware, and utilize credential-harvesting utilities. They also use PlugX as their primary backdoor malware, a well-known Remote Access Trojan (RAT) used by multiple Chinese state-sponsored groups since 2008.
The deployment utilizes DLL sideloading, exploiting vulnerable binaries to initiate the PlugX loader.
A notable tactic includes using a user-cloning utility tool. This enables the actors to maintain a low profile, persist within compromised networks, and clone an administrator's permissions to a guest account on infected systems.
Additionally, DragonRank breaches further Windows IIS servers within targeted networks through additional web shells or exploits via remote desktop logins using stolen credentials.
Distinctively, DragonRank operates a commercial website that provides white-hat and black-hat SEO services. These include cross-site ranking, single-site ranking, parasite ranking, extrapolation ranking, and search result dominance.
They boast about supporting large-scale industry advertising across more than 200 countries and regions globally and offer Telegram and the QQ instant message application contact information.
In other news, a threat actor identified as Tidrone, linked to Chinese espionage activities, has been targeting military and satellite industries in Taiwan.