Chaos Ransomware Variant Targets Japanese Minecraft Gamers
- A Chaos ransomware variant is targeting Minecraft players in Japan, barring their access to the infected devices.
- This malware encrypts some files while but it destroys others, so they cannot be recovered.
- Victims are urged to pay via Bitcoin or pre-paid cards to get their files back, but even paying does not ensure data retrieval.
A Chaos ransomware variant was discovered targeting Japanese Minecraft gamers, encrypting some files and deleting others that become irrecoverable and are lost forever. So, even victims who end up paying the ransom to recover their files risk not getting back all their data. This malware specifically targets Windows users in Japan and does not actually steal data from infiltrated devices, but it does destroy shadow copies from the device to remove any chance of recovering the files.
Some Minecraft users like to have alternate ("alt") accounts aside from their main account for various purposes, and this is why they are often openly available on Minecraft online forums. A variant of Chaos ransomware hidden in such a file pretending to contain a list of “Minecraft Alt” accounts was found by researchers on Japanese Minecraft forums. This component, combined with the fact that the malware doesn't identify the language setting of the compromised device and the ransom note is in Japanese, led the cybersec researchers to believe this their effort is to target Minecraft gamers in Japan.
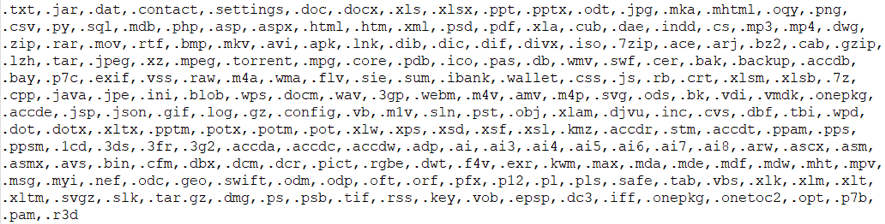
The file used as a lure was an executable masked with a text icon to trick potential victims into believing it was a text file containing stolen Minecraft usernames and passwords. Once the gamers take the bait, the Chaos variant looks up files less than 2,117,152 bytes on the drive and encrypts them adding a random alphanumeric four-character file extension to them.
It also looks up other files larger than 2,117,152 bytes to corrupt them with random bytes. This makes the ransomware highly destructive because these files will not be recovered even if the ransom is paid. The reason behind this is not known. However, the Chaos malware was originally classified as a "wiper malware" and the ransomware component was added later on.
After the encryption is done, the attackers drop a ReadMe.txt ransom note asking for either Bitcoin payment and pre-paid card-based funds transfers, without mentioning the preferred pre-paid card type. The file decryption ransom was set very low compared to other strains, at about 2,000 Yen ($17).
In Japan, there are over 50,000 convenience stores that sell all kinds of pre-paid cards (online shopping and streaming services, gaming, music, mobile phone credit) and are open non-stop. However, the actors apologize and mention they are only available on Saturdays.