New Spook Ransomware Building on Prometheus Codes Exposes All Victims, Even Paying Ones
- Spook is a new ransomware taking corporate data hostage across major US industries, with a focus on manufacturing.
- It is based partially on the previously notorious ransomware families Prometheus and Thanos and divulges stolen data no matter if the ransom is payed.
- With the capacity to negate anti-ransomware like Raccine, it has claimed 17 victims so far.
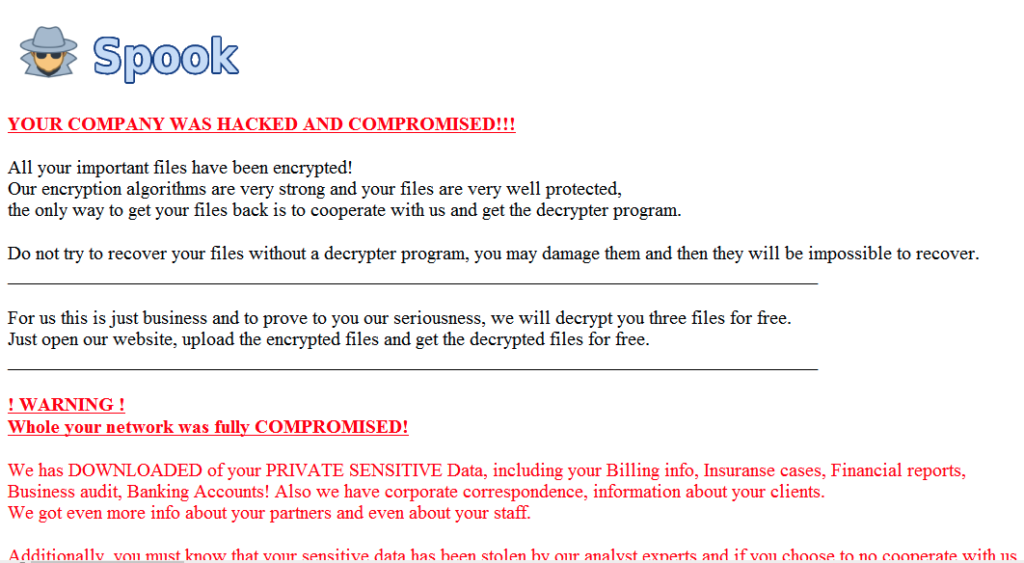
A new ransomware called Spook is emerging as a big threat in the cybersecurity space, and it was first noticed in late September this year. The malware seems to be based on previously known malware like Prometheus, which itself is based on another previous malware called Thanos. To date, according to Spook’s own website tally, it has claimed 17 victims and has been attacking industries without any discernable discretion. The data for which the ransom is not paid is listed as “For Sale” while negotiations happening for others via its TOR payment portal are put under “Company Decides.”
Apparently, Spook and Prometheus share a code similarity between 29 to 50 percent. SentinelLabs researchers have noticed they also have layout and structure similarities, particularly in the payment portal. Spook has a “very strong (AES) encryption” along with the threat of leaking victim data to the public. This malware encrypts target devices without needing an internet connection. An entire disk full of data can get encrypted in a matter of minutes few minutes.
Following this, the victim gets a ransom note on their desktop alongside several system notifications. The ransom note is further highlighted after the system is rebooted. Once the malware confirms optimal encryption on the victim’s drive, the malware gets on enumerating local files and folders as well as accessing available network resources.
As a Thanos-derivative, Spook uses random strings sets at runtime for passphrase-protecting file encryption (AES). This arbitrary string set passphrase is added to the attacker’s public key and included in the ransom notes, making it impossible to recover the encrypted data with the private key.
Further, the malware will prevent antivirus or anti-malware software bootups. It also maintains a startup directory shortcut for displaying the ransom note every time a system is rebooted. The first part of the process inhibits Raccine anti-ransomware process popularly used by organizations. This product is used for disabling ransomware UI components and update features from the attacker’s side. The actions for doing this are executed via basic OS commands like reg.exe and schtasks.exe.
Spook continues to target victims across cyberspace in virtually all industries, and organizations with crucial data accessible online are recommended to use viable methods of securing their networks and data infrastructure.