Babuk Ransomware Actors Compromised Washington D.C. Police’s Systems
- The Metropolitan Police of Washington D.C. has just had a network intrusion from the Babuk gang.
- The FBI is helping the police department conduct a subsequent investigation, but important files appear to have been stolen.
- This is a failure not only in network security but most importantly in responsible data management and protection.
Babuk, the ransomware group that hit Houston Rockets two weeks ago, has just added another high-profile victim on its dark web portal, and it’s the Metropolitan Police force of Washington D.C. The actors accompanied their post by declaring that no comments are necessary this time and just underlined that even organizations of this kind and significance have huge security gaps. From its side, the Washington D.C. police stated that they are aware of unauthorized access on their server and will continue to review the activity with the help of the FBI.
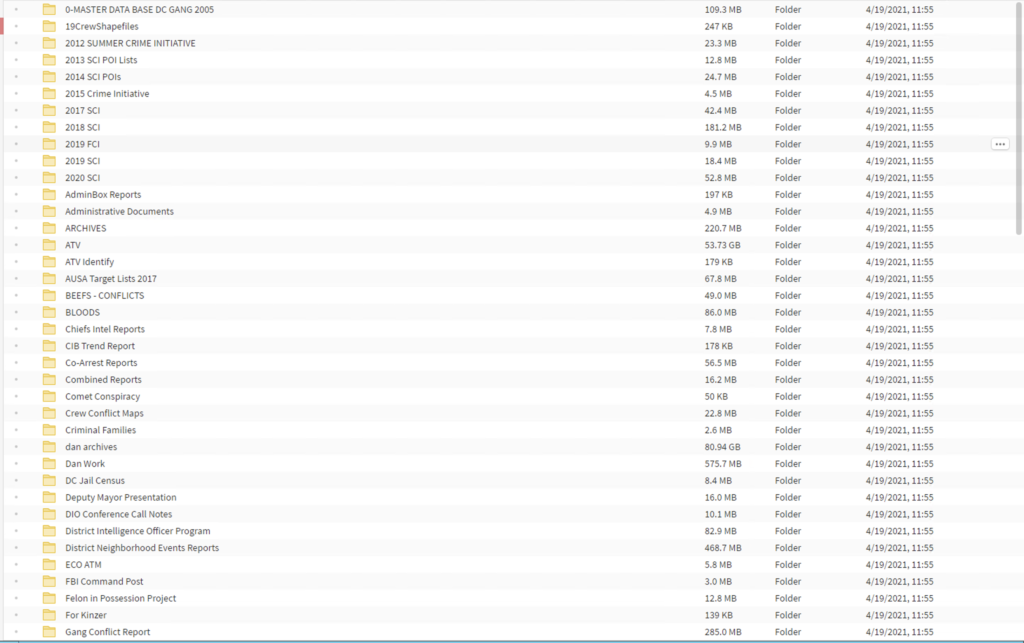
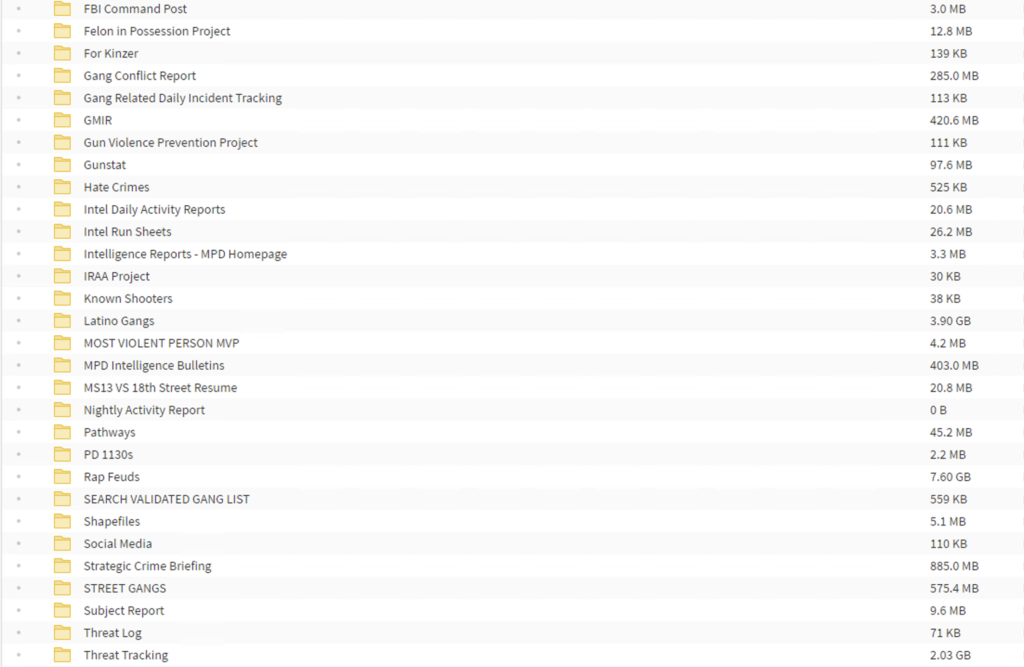
The website of the Washington police is up as normal, and all operations appear to have remained unaffected by this incident. However, the actors claim to have exfiltrated sensitive information and even posted screenshots on their portal to prove the claims. In there, we can see Chief reports, documents detailing police operations, arrest targets, gang categorizations, POI (person of interest) lists, intelligence reports, HR-related stuff, informants, and various extremely sensitive stuff that shouldn’t have been leaked.
In total, the crooks claim to be holding 250GB of data and threaten to publish everything if the state of Washington doesn’t pay them the ransom. It is really sad to see that large police departments store information of this type without encrypting it.
Data breaches and leaks are almost inevitable, so preparing for their occurrence should be a priority. This incident brings great danger to “key persons” who work with the police, destroys the prospect of key investigations and undercover operations, “burns” secret agents, and informs POIs that the police are on their back.
The same thing happened again last year when hackers breached a central information hub, and also in 2019 when three FBINAA sites got hacked and thousands of sensitive documents were leaked online. Even the Argentinian police got a taste of this last May when a 259GB data dump exposing them appeared on the dark web, leaking officer images, emails, documents, crime reports, and wiretap recordings.
Last week, the Babuk group posted a message on its portal to inform their fellow cybercriminals that the strain has been fixed and that Emsisoft’s unlocking tricks won’t work anymore. Expert M. Gillespie told us that Babuk’s strain is very badly written and still carries many flaws. As we see now, though, the encryption part isn’t even the main point in these operations. The problem remains the stolen data, and paying any amount won’t fix it.