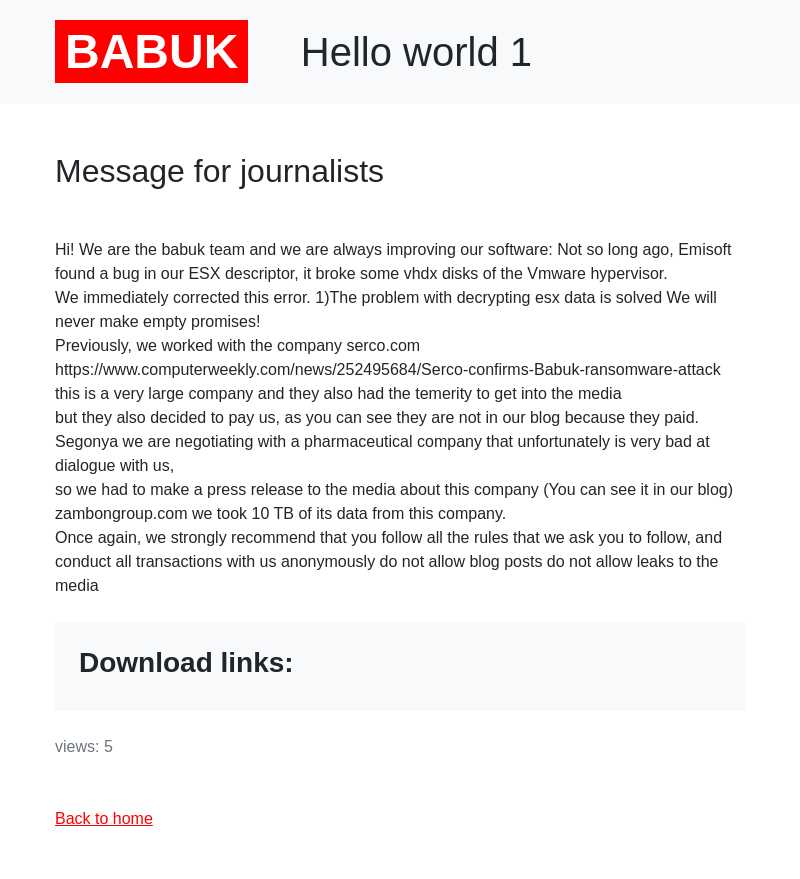
Babuk Has a “Message for Journalists” Meant to Intimidate Victims
- The Babuk ransomware gang has announced the fixing of the bug Emsisoft found last week.
- The researchers believe that the actors are moving too quickly, making too many errors in the process.
- The crooks have also named a victim that paid them and one that isn’t willing to negotiate.
The Babuk ransomware group has posted a “Message for journalists” on its dark web portal over the weekend, explaining that they have fixed a weakness in their malware’s decryption scheme and that paying the requested amount of money is still the best way for victims to resolve a Babuk ransomware infection.
Before we get any deeper into this, we should point out that TechNadu.com is not a mouthpiece for cybercriminals, and we do not reproduce published messages without considering all aspects of the act. From a journalistic perspective, Babuk’s message holds a certain informational value, but we cannot convey it “deshelled,” leaving the intimidation aspect out. We can remind you, though, that you're not supposed to negotiate with ransomware actors or to pay them any money, and you should instead inform the authorities about such infections.
First of all, Babuk confirms that Emsisoft researchers have indeed managed to find a bug in their ESX descriptor, breaking some vhdx disks of the VMware hypervisor. This came out last Wednesday, around the same time the particular group hit Houston Rockets. Emsisoft commented that Babuk has been moving forward too quickly, and this has introduced the element of carelessness as well as multiple fundamental design flaws in both the encrypting and the decrypting parts of the particular ransomware.
The second part of the “message” is directed to victims, urging them to just pay the requested ransom and avoid leaking the news of a data breach to the media. This means Babuk is only posting victims on their site after a certain period of initial negotiations has passed without making any progress. An example of an entity that allegedly paid the group is Serco, which went on to confirm the attack with a three-month delay.
An example of a company that doesn’t want to negotiate with Babuk is allegedly Zambon Group, an Italian pharmaceutical. With the help of KELA, we were able to dig deeper into this and found that Babuk claims to have stolen 10 TB of data after being in the firm’s network for seven whole months. The crooks are also providing screenshots of the stolen data as proof of having “cloned” the servers, but for now, no actual data samples have been leaked.
We have reached out to the Zambon Group to find out if what Babuk claims is true or not, and we have also sent a message to Emsisoft to ask about the fix and whether or not it is indeed addressing the issues that they’ve found. As soon as we hear back from either, we will update this piece.