Attackers Bypass SentinelOne EDR Using ‘Bring Your Own Installer’ Technique
- A critical flaw has surfaced in the SentinelOne EDR system, exposing organizations to potential cybersecurity exploits.
- Attackers could bypass SentinelOne via agent version change interruption.
- The attacker uses multiple installer versions and targeted termination.
A loophole in the SentinelOne Endpoint Detection and Response (EDR) system was discovered, which threat actors can manipulate during SentinelOne’s agent upgrade or downgrade process to disable protection on targeted systems and leave endpoints vulnerable.
Dubbed the "Bring Your Own Installer" technique, this attack leverages a significant oversight in the SentinelOne EDR process, Aon’s Stroz Friedberg Incident Response Services (“Stroz Friedberg”) recently reported.
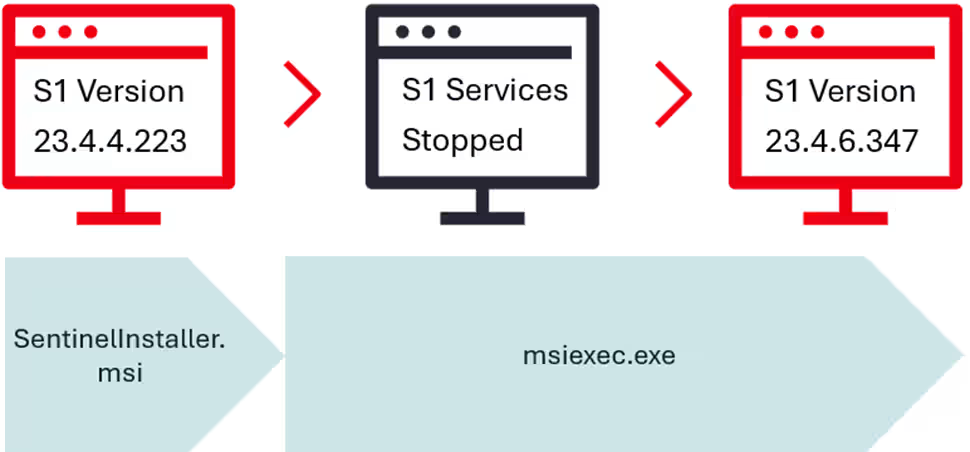
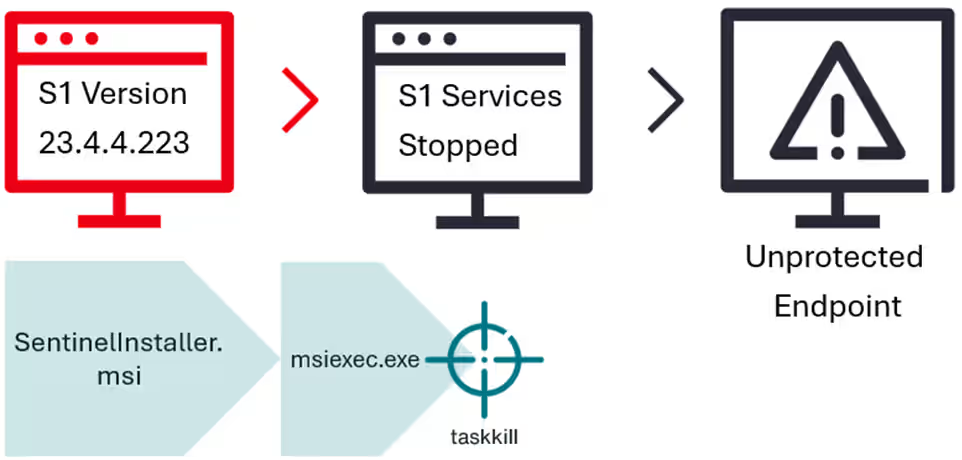
The vulnerability emerges during an agent version update or downgrade when SentinelOne processes are temporarily terminated. By precisely timing and interrupting this process, attackers managed to leave systems unprotected.
The threat actor uses numerous legitimate, signed versions of SentinelOne installer files to initiate updates or downgrades. During the upgrade or downgrade, all SentinelOne processes are terminated for approximately 55 seconds.
By halting the msiexec.exe process in this critical window, the upgrade process is disrupted, leaving the system without active SentinelOne protection.
The attack method was successfully replicated in a controlled environment on a Windows 2022 server, reinforcing the validity and potential risk of such an exploit.
SentinelOne has responded to the vulnerability with mitigation recommendations for its customers. A key protective feature, “Online Authorization,” prevents local upgrades or downgrades without external validation. When enabled, this feature blocks unauthorized manipulations, effectively neutralizing the exploit.
Stroz Friedberg’s testing confirmed that enabling this security measure provides a robust line of defense, preventing the deactivation of SentinelOne's protection under this attack scenario.