New RansomHub Attack Uses TDSKiller to Disable EDR and Steal Credentials
- The RansomHub Ransomware group was observed abusing Kaspersky's TDSSKiller tool.
- The hackers managed to disable EDR services and deploy credential-harvesting malware.
- LaZagne can exfiltrate login details from browsers, email clients, and databases.
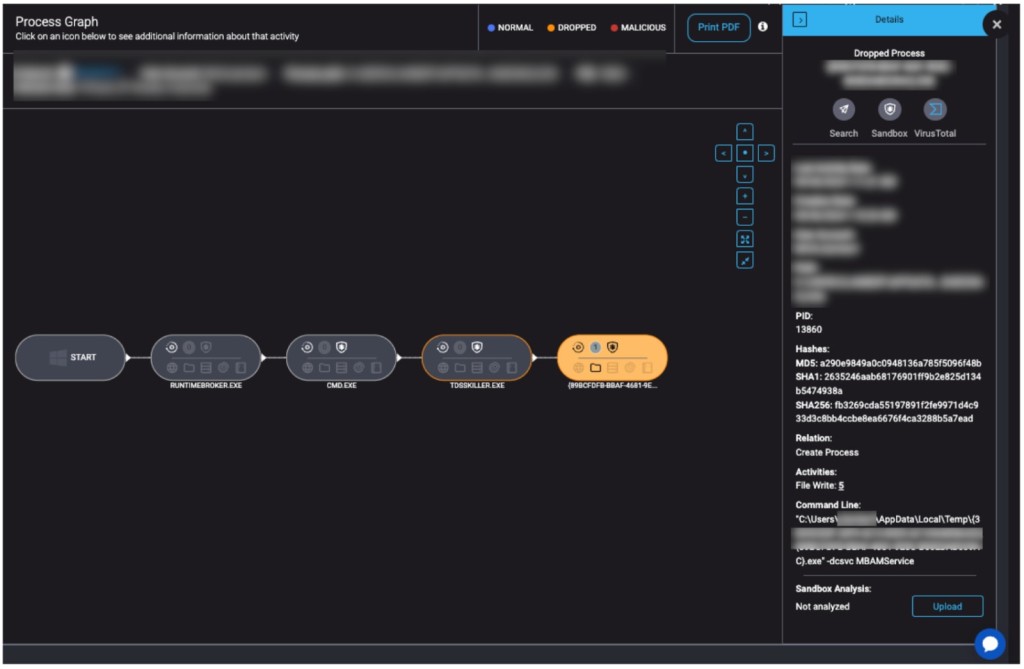
The RansomHub ransomware group has been exploiting Kaspersky's TDSSKiller, traditionally used for identifying rootkits and bootkits, to disable endpoint detection and response (EDR) software and compromise target systems more efficiently, according to the latest report from the ThreatDown Managed Detection and Response (MDR) team.
RansomHub leverages TDSSKiller, a legitimate tool, to disable EDR services by interacting with kernel-level operations. The tool is typically executed from a temporary directory with a dynamically generated executable name, minimizing detection risks.
Following the deactivation of security defenses, RansomHub deploys the LaZagne malware to extract sensitive login data from various applications, including browsers, email clients, and databases.
Originally developed by Kaspersky to tackle difficult-to-detect malware, TDSSKiller operates with a valid certificate, which allows it to bypass security solutions without raising alarms.
Disabling EDR solutions, which operate at the kernel level to monitor low-level system activities, leaves systems vulnerable to additional attacks. By obtaining login information, RansomHub can move laterally across networks, increasing their access and potential damage.
RansomHub is a ransomware-as-a-service (RaaS) active since February. Known to overlap with other ransomware groups, such as ALPHV (BlackCat) and Knight Ransomware, the group reportedly targeted over 210 victims in various sectors, including healthcare, government services, and critical infrastructure.
The RansomHub ransomware gang recently hit Planned Parenthood of Montana and the Halliburton oilfield services giant. Change Healthcare's data breach was posted on RansomHub’s leak website after the cybercriminal group that claimed it, ALPHV, was shut down.
The recent Patelco Credit Union breach was also attributed to the RansomHub ransomware group, which leaked 726,000 customers’ data on the group's extortion portal on August 15 after the ransom payment negotiations allegedly failed.