APT-C-23 has Re-Emerged on the Front Scene with “Mygram” Hacks
- IDF soldiers and officers received fake messages that lured them into downloading “Mygram IM”.
- This software is essentially powerful spyware that can access all user data on a mobile device.
- The actors behind this were confirmed to be “APT-C-23”, who are believed to be Hamas hackers.
Researchers from the “360 Threat Intelligence Center” have caught APT-C-23 activity on their radars, and are now reporting about their findings in detail. The hacking group, which is also known as “Two-Tailed Scorpion”, has been targeting the Israel Defense Forces (IDF) since February 2020, using an instant message app called “Mygram” as a bait. The particular app was actually spyware designed to steal private information from the soldiers and hopefully, also any officers of the IDF. The APT-C-23 attacks weren’t limited solely to IDF targets, though, as the Chinese threat researchers confirmed more attempts targeting other entities in the Middle East.
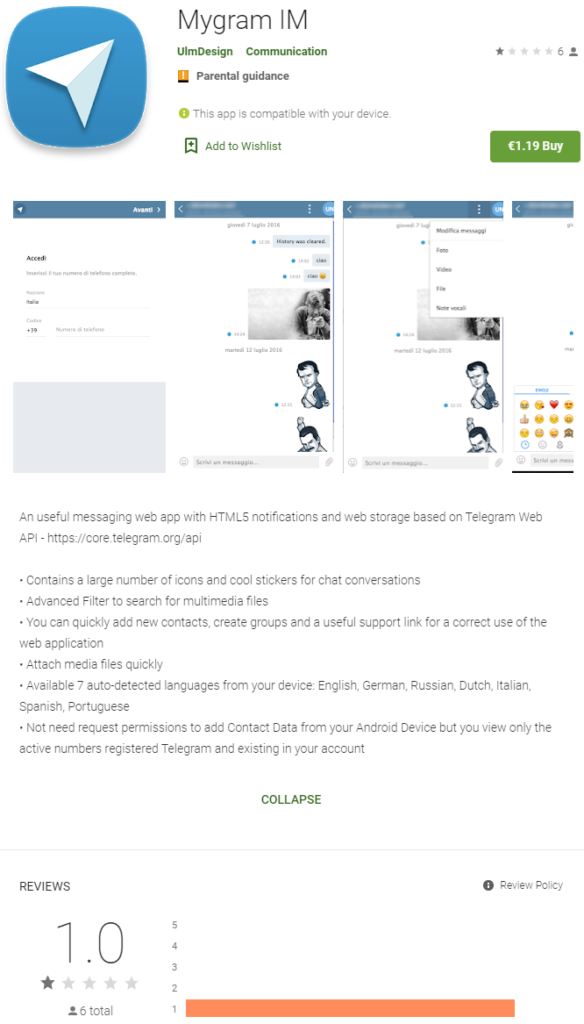
The website that distributes “Mygram IM” is well-crafted, containing detailed descriptions of the features of the chat app, and thus it’s pretty convincing. If someone were to click on the various links that are provided on the website, though, they would quickly realize that none of them works. Moreover, if anyone bothered to check the content for plagiarism, they would immediately realize that everything is stolen from other websites. Thus, the website is fabricated, but not obviously. Mygram IM is also on Google Play, where it promises access to the Telegram API, HTML 5 notifications, and a transparent permission request policy.
Source: Google Play Store
If the user installs the app on their phone, it immediately hides its icon and proceeds to run in the background. The capabilities of the spyware include the following functions:
- Microphone recording
- Camera recording
- Contact access and exfiltration
- SMS access and exfiltration
- Social media (Facebook, Instagram) data exfiltration
- Whatsapp message access and exfiltration
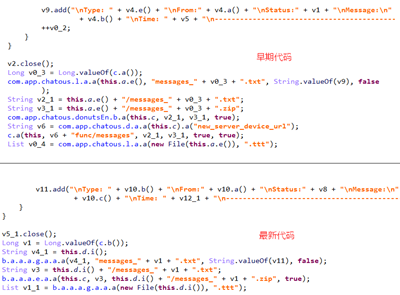
The malware is also capable of receiving Firebase Cloud Messaging commands and functions encoded with Base64. As the researchers point out, the actors are using multiple different spyware versions on their campaigns, switching from one method to the other. However, everything features the same or at least similar code structure.
Source: Blogs360.cn
We have seen Hamas hackers targeting Israeli soldiers with fake IM apps and nicely crafted phishing messages back in February, and the latest reports about the APT-C-23 activity coincide with that time period. The apps that were used then had the names “GrixyApp,” “ZatuApp,” and “Catch&See”, and they were all distributed via nicely crafted phishing websites. Thus, we can now safely assume that APT-C-23 was behind these attacks too. The particular group of hackers has been around since 2016, plaguing the Middle East with campaign names such as “FrozenCell”, “AridViper”, and “Micropsia”, as those were given by the various research groups that are monitoring them.