AI-Powered Cloaking Services ‘Hoax Tech’ and ‘JS Click Cloaker,’ Most Used in Phishing Campaigns
- Trick Cloaking: The Hoax Tech and JS Click Cloaker intelligent cloaking solutions are used for shielding fraudulent websites.
- AI-powered tools: Cybercriminals increasingly leverage these AI services to shield phishing sites, scam storefronts, and malware from detection.
- CaaS trend: Cybersecurity researchers flagged a trend in using cloaking-as-a-service (CaaS) for phishing and fraud infrastructure.
Cybercriminals are increasingly leveraging AI-powered cloaking services to evade detection and prolong the lifespan of phishing sites, fake stores, and malware, adopting techniques once used by shady advertisers in a cloaking-as-a-service (CaaS) trend.
AI-powered cloaking services operate by presenting dual content via white pages and black pages – also called trick cloaking.
Cloaking Methods and Platforms
Automated security tools and moderators see harmless “white pages,” while real users are exposed to “black pages” containing malicious content. Platforms like Hoax Tech and JS Click Cloaker lead this trend, according to a recent cybersecurity report from SlashNext.
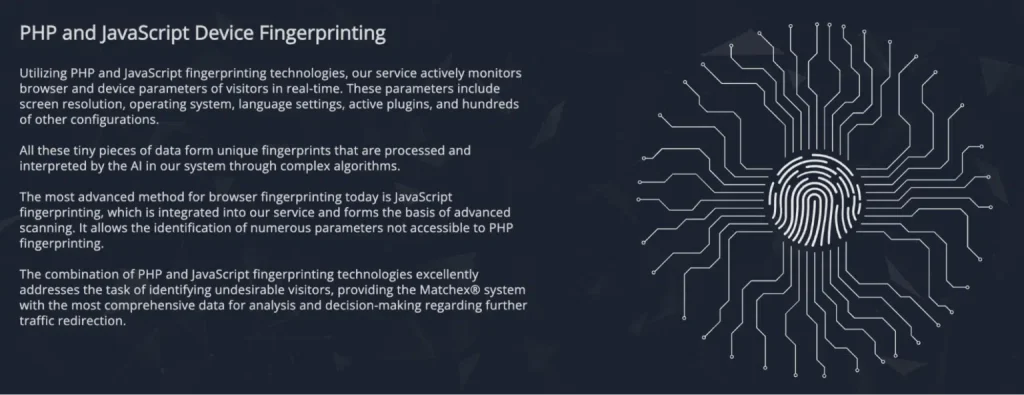
Hoax Tech Cloaking employs JavaScript fingerprinting and machine learning to examine visitor traits such as location, device type, and browser behavior. Its AI engine, Matchex, adapts to new patterns, ensuring malicious sites remain invisible to bots and uncovering even advanced security crawlers.
JS Click Cloaker evaluates traffic across 900+ parameters, assessing cues like IP addresses and behavioral actions. This platform provides granular filtering capabilities, enabling attackers to block security tools while seamlessly redirecting genuine visitors to phishing or scam pages.
By integrating AI for dynamic profiling and content switching, these services allow scams to bypass detection and trap more victims over time.
Andy Bennett, Chief Information Security Officer at Apollo Information Systems, warns that AI-powered cloaking marks a dangerous evolution of familiar marketing tools into adversarial threats.
“Just as threat actors weaponize encryption for ransomware, they’re now twisting audience-targeting technologies to evade detection and personalize malicious content,” he explains.
Bennett adds that attackers can distinguish between security scanners and real users, dynamically crafting unique payloads in real time.
Countering AI-Powered Cloaking
To tackle the growing sophistication of cloaking services, organizations must adapt by integrating AI-driven defenses, updating incident response protocols, and adopting zero-trust principles for robust security, according to expert advice from Mayuresh Dani, Security Research Manager at Qualys.
Dani recommends using real-time behavioral analysis and multi-perspective scanning to detect cloaked content and spot discrepancies across geographies or device types. And also emphasizes the need for AI-powered defenses, zero-trust frameworks, and incident response plans tailored to AI-driven threats.
Trey Ford, Chief Information Security Officer at Bugcrowd, says that endpoint patching, hardening, and browser protection remain critical points of control and monitoring, adding that AI-powered cloaking services are the modernized version of FastFlux DNS.
He explains that just as attackers once used FastFlux to map and profile targets, these advanced cloaking tools now serve a similar purpose — enabling threat actors to stay a step ahead of both defenders and advertisers who continue to rely on gray-area tactics to retain value.
TechNadu reported on a similar case in December 2024, when threat actors used AI-generated “white pages” for malvertising targeting Securitas OneID users and the popular remote desktop program Parsec used by gamers.