New Attacks Loom for MOVEit After 2023 Clop Breach; Global Scanning Jumps from Zero to 682 in 90 Days
- A significant surge in scanning activity targeting MOVEit Transfer systems indicates a potential cyberattack
- Over 400 unique IP addresses were observed scanning for vulnerabilities in the last 24 hours
- In total, analysts witnessed 682 scanning activities in three months beginning in May
File transfer service MOVEit, which made headlines for multiple security incidents stemming from a single vulnerability, has once again drawn attention due to renewed threat activity.
Researchers observed an increase in scanning activity targeting the MOVEit File Transfer system beginning on May 27, 2025.
Designed to be a secure file transfer software, MOVEit was observed being probed by suspicious actors scanning for systems with exploitable vulnerabilities.
“Attackers are exploiting a vulnerability in outdated versions of MOVEit Transfer, emphasizing the importance of keeping software up-to-date with the latest patches,” said Nivedita Murthy, Senior Staff Consultant at Black Duck.
“Attackers are always on the lookout for unpatched and older versions of software to take advantage of. With the help of AI, attackers can automate a lot of their tasks and run attacks faster while making them harder to detect.”
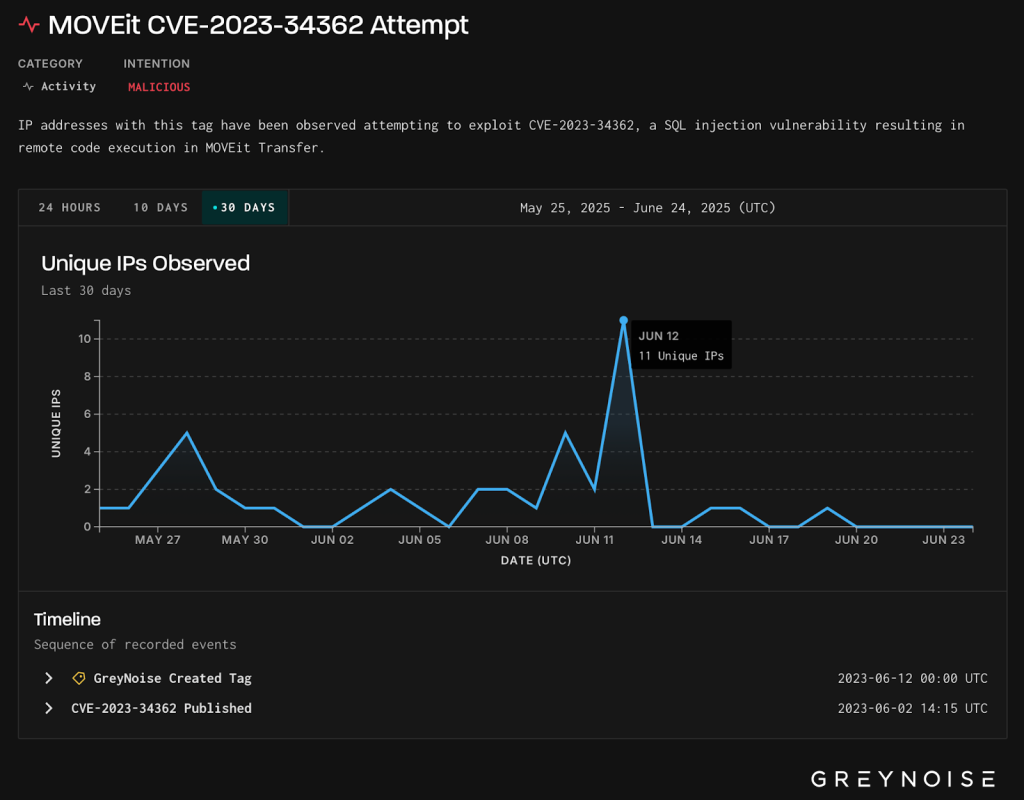
On June 12, 2025, the platform experienced low-level exploitation attempts. Threat actors tried to exploit two previously disclosed MOVEit vulnerabilities, which included CVE-2023-34362
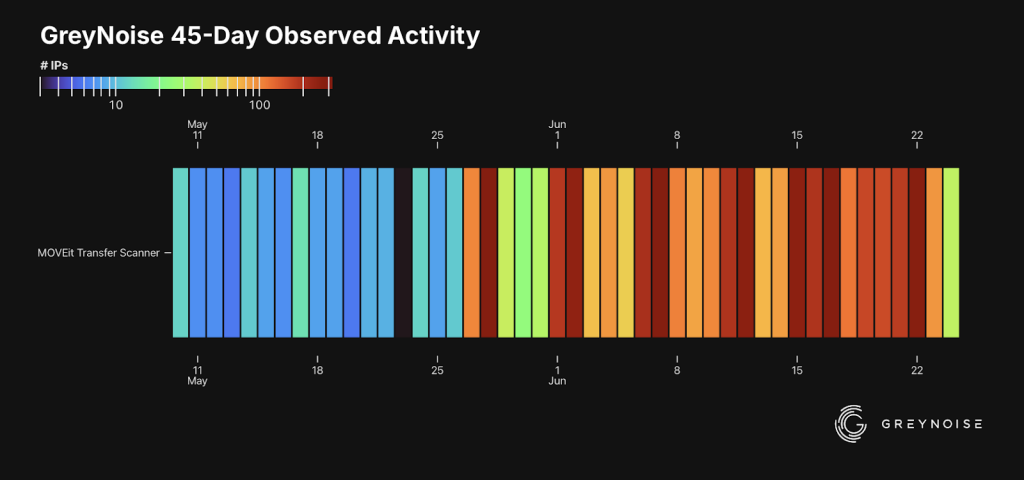
On average, researchers detected nearly 10 IP address scanning events per day. However, on May 27, over 100 unique IP scans were recorded, and 319 on May 28, raising concerns.
Subsequently, scanning activity continued to surge between 200 to 300 IPs per day, according to a GreyNoise report.
“These patterns often coincide with new vulnerabilities emerging two to four weeks later,” GreyNoise added.
Furthermore, research revealed that over 90 days, scanning activities surged to 682 unique IPs. It triggered GreyNoise’s MOVEit transfer scanner tag, where previously, such activity had registered at zero.
Key observations were as follows:
- 303 IP addresses were linked to Tencent Cloud (ASN 132203), making it the most active
- The concentration of scanning infrastructure suggests a deliberate and programmatically managed attempt
- Cloudflare was observed for 113 IPs, Amazon for 94, and Google for 34
- The scanning IPs were traced to the U.K., U.S., Germany, France, and Mexico
Exploitation attempts focused on SQL injection vulnerabilities, CVE-2023-34362 and CVE-2023-36934 for remote code execution.
Regarding the current safety posture of MOVEit Transfer, GreyNoise clarified, “These events occurred during the period of heightened scanning and may represent target validation or exploit testing, but at this time, no widespread exploitation has been observed by GreyNoise.”
“The increase in scanning activity targeting MOVEit Transfer systems is worth monitoring, but doesn’t necessarily indicate imminent or widespread exploitation,” said Shane Barney, Chief Information Security Officer at Keeper Security.
“This type of behavior often reflects opportunistic threat actors probing for unpatched systems – not necessarily a sophisticated adversary.”
“That said, ensuring patches are applied, systems aren’t unnecessarily exposed and privileged access is tightly controlled are all foundational steps that help reduce risk,” he added.
Security teams are strongly urged to block suspicious IPs, audit the public exposure of all MOVEit Transfer systems, and apply patches for vulnerabilities. They are also advised to monitor real-time attacker activities to protect client data.
Murthy also recommended that security teams “inventory all instances of the software using SCA tools, implement additional controls such as authentication and authorization, and regularly scan their software inventory for risks.”
She added, “Maintaining accurate Software Bills of Materials (SBOMs) is also crucial in managing risk and helps confidently unleash business innovation in an era of accelerating risk.”
Barney emphasized that while cybercriminals may leverage automation or AI to scale attacks, core defense strategies remain unchanged: “Establish a zero-trust architecture, manage privilege access and use real-time threat detection to continuously monitor for suspicious activity.”
The Clop ransomware group exploited a MOVEit vulnerability in 2023, resulting in extortion campaigns that affected thousands of interconnected organizations.