“Molerats” Using New Tools in Middle East Espionage Campaign
- The group of Gaza-based hackers known as “Molerats” has refreshed its toolset with two new backdoors.
- The actors are targeting high-ranking officials from Turkey, the UAE, Egypt, and Palestine.
- The infection chain starts with a phishing attempt that leverages legitimate cloud services.
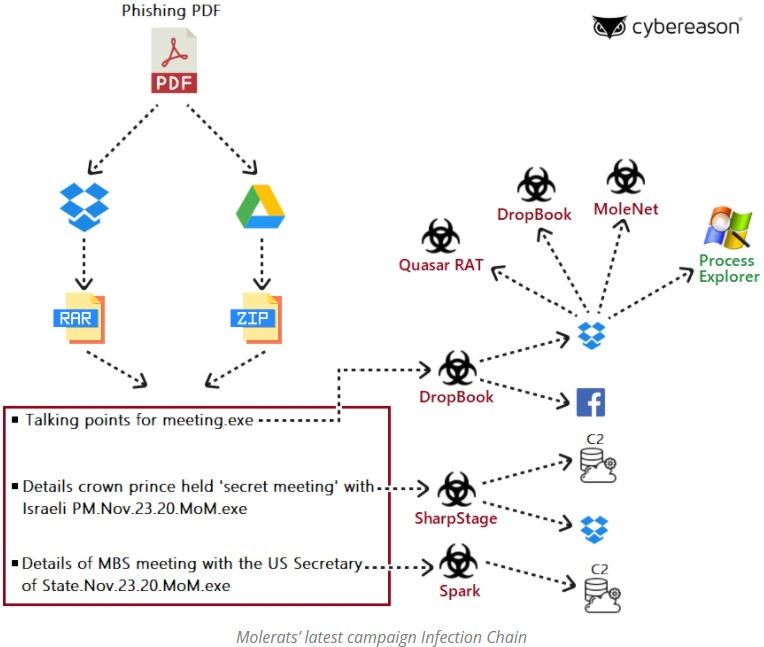
Cybereason researchers report on the most recent activity of “Molerats,” the Gaza-based hacking group that has been engaging in sophisticated cyber-operations since 2012. According to the details shared in the report, the hackers are now using two new backdoors dubbed “SharpStage” and “DropBook,” a MoleNet downloader, and the “Spark” backdoor that was used by the particular APT since at least October 2019.
This toolset enables the actors to execute arbitrary code on the target systems, collect sensitive information, and exfiltrate it without raising security alarms. The targets of the new campaign include high-ranking political figures and government officials in Palestine, the United Arab Emirates, Egypt, and Turkey.
Because of the relatively wide scope of targeting, the actors have to use a range of lures and also make them convincing. The phishing themes include alleged leaked information relevant to pivotal political developments, like elections or international relation events that could quickly shift the dynamics in the region. They all arrive in the form of a PDF file, triggering the abuse of Dropbox and GDrive.
The SharpStage backdoor can perform screen capturing and carries out the exfiltration through Dropbox’s API. It can receive commands directly from the C2, download and execute additional payloads, and even unrar an archive sent through the attacker’s server. The malware checks if the infected machine is using the Arabic language, otherwise it won’t run. Similarly, it performs some sandbox-related checks to determine if it runs on an analysis environment or in the wild.
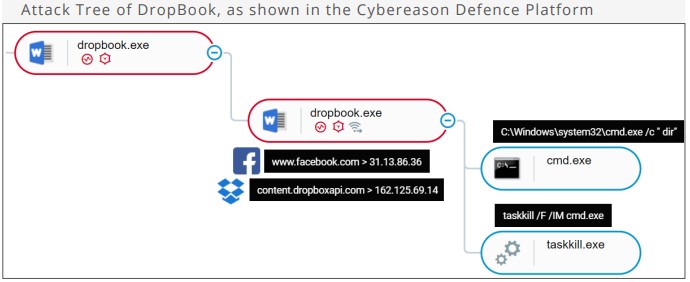
The DropBook backdoor focuses on collecting the names of installed programs and the file names, can execute shell commands that are taken directly from Facebook posts, and download additional payloads via Dropbox. Again, the Arabic language check is performed by the malware, but we see a complementary rather than an overlapping functionality in general.
Cybereason highlights the fact that most of the decoy documents claim something about Israel and its relations with neighboring Arab countries - so if you've received something along those lines, beware. Moreover, the researchers see a connection between Molerats and APT-C-23, whom we saw targeting the Israel Defense Forces through the “Mygram” app back in May 2020. The two hacking groups appear to be operating on behalf of similar interests and are both considered to be sponsored by the same entity in Gaza.