Zero Day Vulnerability Discovered in the Mac Zoom Client
- Zoom is plagued by a zero-day that enables malicious websites to force users joining meetings.
- The developers of the conferencing app did fix one part of the vulnerability, but not the main problem.
- Zoom believes that their core differentiator in the market is what makes the attack possible.
Security researcher Jonathan Leitschuh has disclosed a severe zero-day vulnerability in the Mac Zoom Client that allows a malicious website to activate your camera without asking for user permission. Zoom is a popular video conferencing tool that is used by about 750000 companies right now, so the exposure potential and the associated damage is huge. The vulnerability remains accessible by attackers even if Zoom is no longer installed on the device, but has been used at some point in the past. The associated DOS vulnerability is assigned the identifier “CVE-2019-13449”, while the meeting auto-join and webcam activation is the “CVE-2019-13450”.
According to the researcher, the vulnerability allows a malicious website to force a user to join a Zoom call and activate the camera, both automatically and without requesting for permissions. If the attacker wants to, they could create repeated user joining sessions to invalid calls, laying the ground for an inevitable Denial of Service (DOS) condition. The installation of the Zoom client creates a localhost web server on the machine, which stays there even after uninstalling Zoom. This is what makes it possible for the attackers to re-install Zoom on a machine that used it before.
image source: medium.com
The exploitation is based on abusing the meeting link sharing functionality of Zoom that wasn’t implemented securely as it seems. This is what the developers of Zoom perceive as the main advantage of their app, as it makes using it seamlessly. The researcher disclosed the problem to Zoom on March 26, 2019, along with a proposal on how to fix the flaws by changing the server logic. Zoom only met to discuss the matter and the possible fixes on June 11, 2019 and decided to go ahead with the researcher’s suggestion. Although Zoom disabled the host’s ability to activate the client’s webcam automatically, they have not plugged the flaw that allows a website to forcibly join the visitor to a call.
The researcher adds that a regression in the implemented fix allows the camera activation, so we can deduce that nothing on this part was really fixed after all. What was addressed though is the DOS vulnerability that was based on the sending of numerous GET requests for a bad number, as demonstrated by the associated proof of concept code. The DOS was fixed with 4.4.2, so if you’re using an older version you should upgrade immediately. However, even if you get the latest 4.4.4, you will still be vulnerable to the Zoom webserver localhost interaction and the forced meeting joining with your camera activated.
image source: medium.com
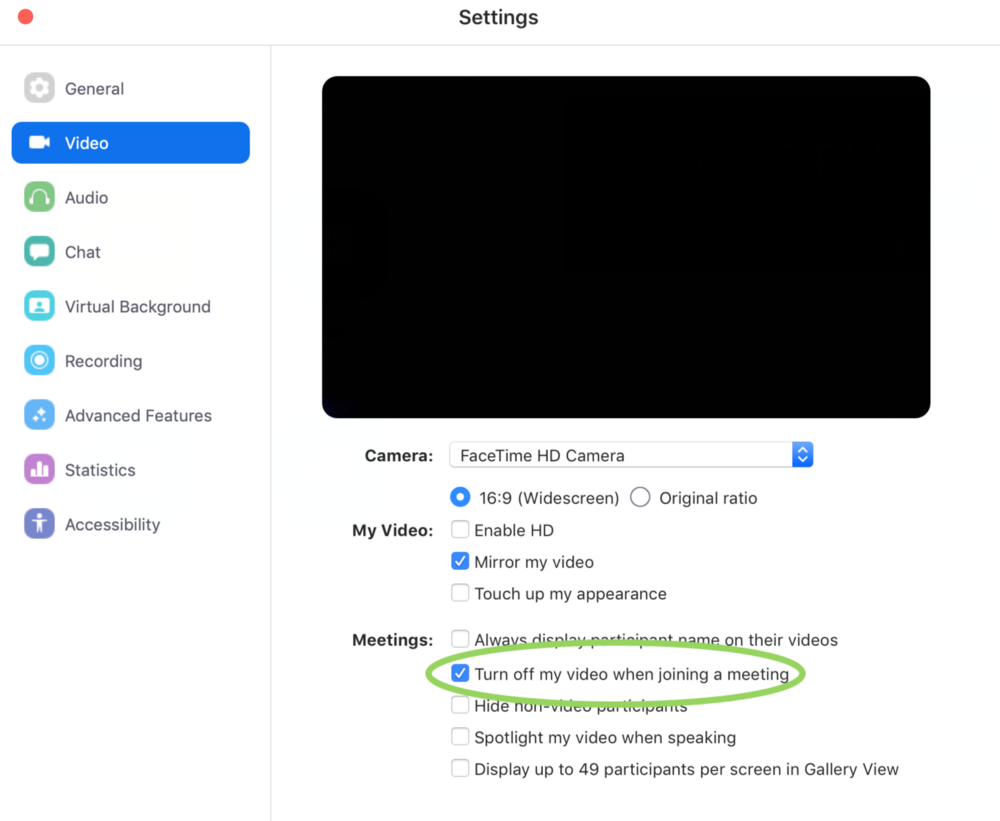
To check if localhost is still on your machine, open a terminal and run “lsof -i :19421”. This is the port number that the Zoom web server should be running if it's still there, so you can kill it with “kill -9 [PID number]”. If you want to use Zoom safely, go to the Video settings and tick the box that disables webcam activation when joining a meeting.
Do you trust Zoom for your daily conferencing and communication needs? Share your thoughts in the comments down below, or join the discussion on our socials, on Facebook and Twitter.