ZipLine Social Engineering Campaign Targets U.S. Manufacturing Sector with Custom Malware
- Targeting manufacturing: A sophisticated social engineering campaign targets supply chain-critical manufacturing companies with MixShell malware.
- How it starts: Hackers start AI-themed, business-oriented email conversations via the company’s public “Contact Us” form.
- Deploying malware: Attackers leverage these legitimate-looking interactions to stealthily deliver a custom malware implant via a ZIP attachment.
A sophisticated social engineering operation, designated the ZipLine phishing campaign, has been identified targeting supply chain-critical manufacturing organizations in the U.S. A new analysis reveals a highly patient and resourceful threat actor leveraging a reversed phishing flow and custom malware to achieve initial access and persistence.
Advanced Social Engineering and Infection Chain
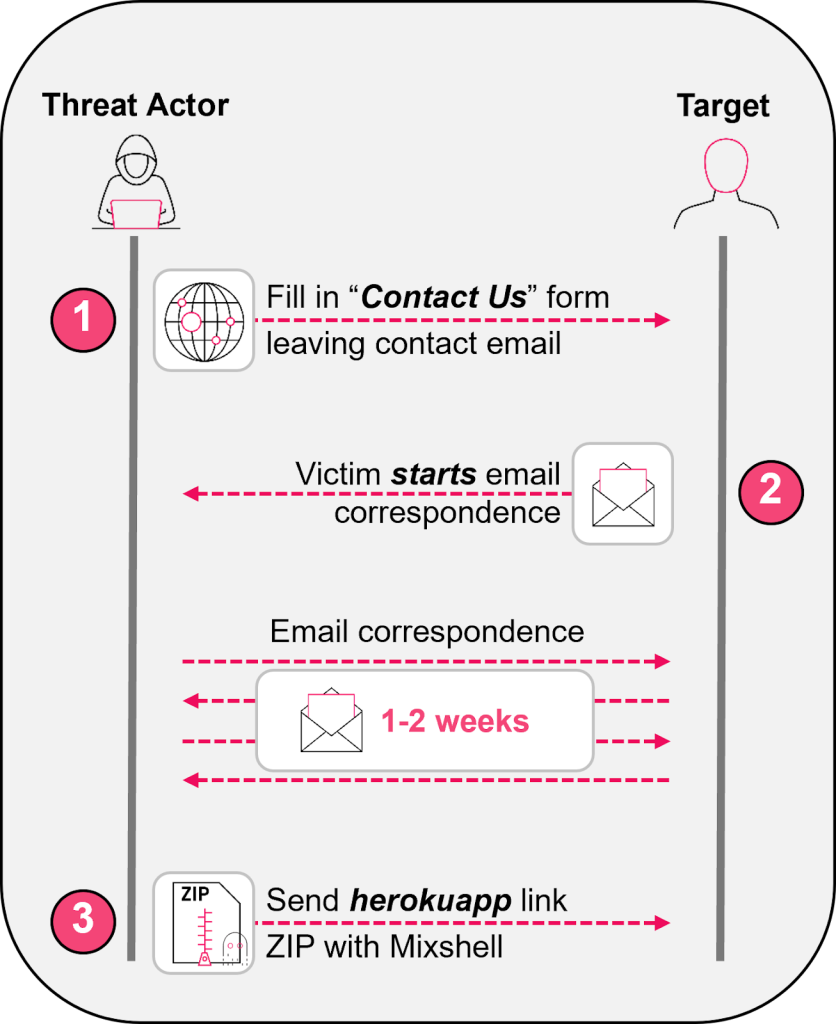
The phishing attack on U.S. companies initiates through the target's public "Contact Us" web form, reversing the typical email-based attack vector and establishing immediate legitimacy, according to a new cybersecurity report from Check Point Research (CPR).
Threat actors engage in prolonged, business-oriented email correspondence, sometimes lasting weeks, before delivering a malicious ZIP archive hosted on trusted platforms like Heroku.
Recent iterations of the campaign have incorporated an "AI Impact Assessment" pretext to enhance social engineering effectiveness.
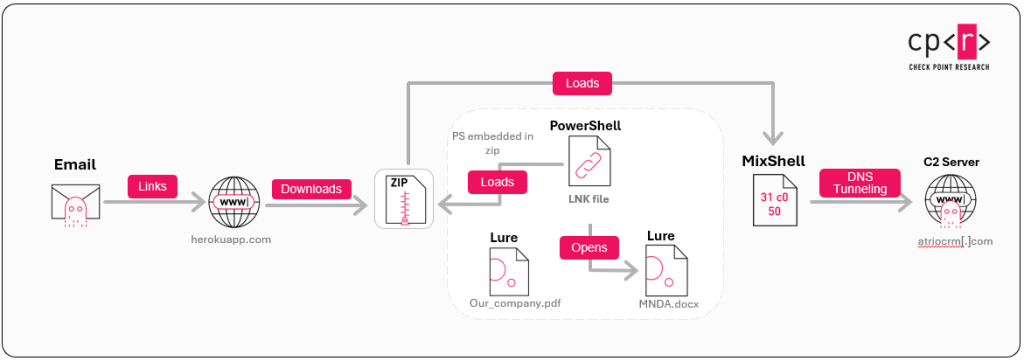
The infection chain begins when a victim opens a malicious LNK file within the delivered ZIP archive. This action triggers a PowerShell loader that extracts and executes a script embedded within the archive's binary data.
This script establishes persistence using TypeLib hijacking of a Microsoft Web Browser COM object and deploys the MixShell malware implant directly into memory.
MixShell Malware and C2 Infrastructure
MixShell is a custom, in-memory shellcode implant featuring advanced evasion and command-and-control (C2) capabilities. The malware uses a custom ROR4 hashing algorithm for API resolution and communicates via DNS TXT record queries, with an HTTP fallback mechanism.
Its functions include file operations, command execution, and a reverse proxy. A PowerShell variant with enhanced anti-debugging and sandbox evasion has also been observed.
The campaign's infrastructure utilizes selected and repurposed aged domains, many of which matched previously registered U.S.-based LLCs, to lend credibility and legitimacy to their attack infrastructure.
Domains often hosted cloned websites with identical layouts and even reused stock imagery, increasing their effectiveness in bypassing security filters and gaining the trust of targeted organizations.
This strategic use of established, business-sounding domains and template-based content demonstrates a deliberate effort to evade detection and enhance the success of their phishing operations.
Campaign Targets
Most targets are in industrial manufacturing, including machinery, metalwork, component production, and engineered systems, while hardware & semiconductors, consumer goods & services, and biotech & pharmaceuticals are among the less targeted sectors, suggesting focus on entry points across wealthy operational and supply chain-critical industries.
This operation highlights evolving cybersecurity threats in 2025, demonstrating how threat actors weaponize trust and legitimate business workflows to bypass traditional security controls.