YiBackdoor Malware Family Linked to IcedID and Latrodectus Uses Unique Encryption Algorithms
- New malware discovered: A new malware family named YiBackdoor was first observed in June 2025.
- Significant code overlap: The malware shares considerable code with the IcedID and Latrodectus malware families, including unique encryption algorithms.
- Advanced capabilities: YiBackdoor can collect system information, capture screenshots, execute arbitrary commands, and deploy additional plugins to expand its functionality.
A new malware family, designated YiBackdoor, exhibits significant code similarities with the established IcedID and Latrodectus malware. First observed in June 2025, this discovery suggests a potential evolution or collaboration between threat actor groups, marking a notable development in the cybersecurity threat landscape.
Technical Analysis and Capabilities
YiBackdoor is a backdoor designed to provide threat actors with persistent remote access to compromised systems, and it was identified by Zscaler ThreatLabz.
Its core capabilities include collecting system information, capturing desktop screenshots, executing arbitrary shell commands via cmd.exe or PowerShell, and dynamically deploying plugins to extend its functions.
The malware employs several anti-analysis techniques, including checking for hypervisors (VMware, Xen, VirtualBox, KVM, Microsoft Hyper-V, Parallels) and measuring code execution time to evade sandbox environments.
Persistence is established by copying the malware DLL to a new directory and creating a Windows Run registry key to execute it via regsvr32.exe on startup.
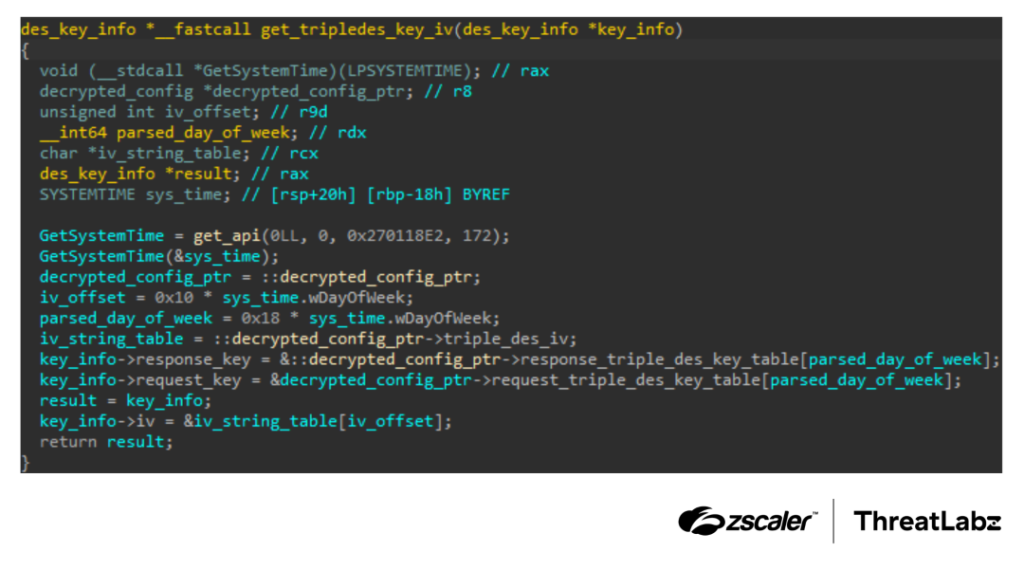
Network communications are encrypted using a unique TripleDES implementation where the encryption key changes daily based on the day of the week, making static signature-based detection more challenging.
The IcedID and Latrodectus Connection
The most critical finding is the IcedID (also known as BokBot) and Latrodectus connection. Latrodectus was created by the developers of IcedID and is actively being developed, with updates to its encryption key pattern and the introduction of new commands.
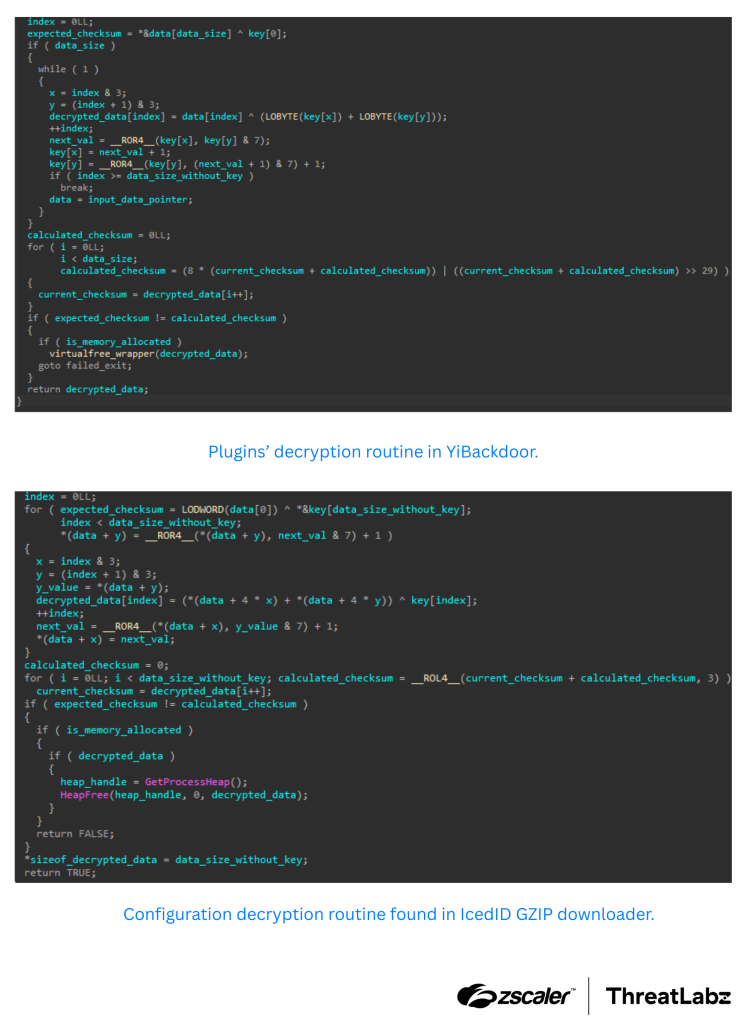
ThreatLabz analysis revealed substantial code overlaps between YiBackdoor and these prominent malware families. This includes the use of identical alphabet charsets for generating randomized strings, a similar configuration decryption key format, and an uncommon code injection technique that hooks the RtlExitUserProcess Windows API function.
Most significantly, the decryption routine for YiBackdoor's plugins is identical to an algorithm previously used by IcedID to decrypt its core payload. This strong link suggests a shared development origin or a direct repurposing of code.
Given the limited deployments observed, researchers assess that this new malware family may currently be in a developmental or testing phase, potentially being prepared for use in initial access operations for ransomware attacks.
In May 2024, a Europol-led effort dismantled infrastructure linked to multiple malware families, including SmokeLoader, Bumblebee, TrickBot, and IcedID.
The Zeus malware gang leader known as Tank, who was sentenced to 18 years in prison in 2024, admitted to being part of the IcedID malware operations for the past years.