Xiaomi’s Guard Provider Security App Makes Phones Vulnerable to MITM Attacks
- Xiaomi’s Guard Provider makes the devices vulnerable to MITM attacks, leading to malware infection.
- The vulnerability lies in the fact that the app indulges in unprotected network communication.
- An update that fixes the issue is already out, but the use of multiple SDKs may hide more problems.
As counter-intuitive as it may sound, Xiaomi’s pre-installed and non-removable “Security” app otherwise known as “Guard Provider”, is an open door for malicious actors who want to carry out a MITM (Man-in-the-Middle) attack on the phone. According to Check Point researchers, the app operates through a labyrinthine process of using multiple SDKs, with the inevitable gaps in the communication between some of them acting as “security holes”. This makes the device susceptible to the implantation of viruses, data-stealing malware tools, ransomware, and anything else the attacker would like to inject. The vulnerabilities have been disclosed to Xiaomi prior to their publication, so if you have not updated the Security app (com.miui.guardprovider) yet, you should do so immediately.

image source: blog.checkpoint.com
The Xiaomi Guard Provider is there to help your phone stay safe from malware and virus infections, and this critical role is what makes it non-removable. Moreover, it offers file-clearing features, as well as device-boosting functionality. The app incorporates three AV choices for the user, namely the Avast, AVL, or Tencent. Upon the user’s selection, the product deploys the designated AV engine and scans the device. This versatility and galore of choices, however, comes with the need to use multiple SDKs (Software Development Kits).
SDKs are there to help developers not having to re-invent the wheel every time they want to implement a new feature in their application. However, when using a number of different SDKs for a single app, a couple of serious drawbacks arise. First, if one of them is problematic or insecure, it can affect the others, acting as a point of infection. Secondly, the storage of sensitive data of one SDK cannot be isolated from the rest, so another SDK can potentially access this data. When apps like the Guard Provider use a rich collection of different SDKs, the situation can easily grow out of the developers’ control, especially as far as security matters are concerned.
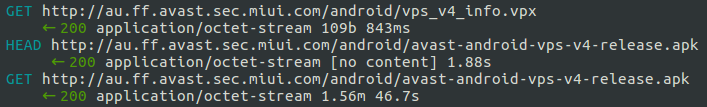
The vulnerability in the Guard Provider is located in the way its network communication works, allowing for arbitrary remote code execution. The network traffic from a Xiaomi device is not adequately secured, and so when the app periodically checks the virus signatures database of the selected AV vendor, the data can be intercepted. Moreover, when the time to update the database comes, it is done through the establishment of an unsecured HTTP connection. This is where a MITM actor could kick in, blocking the connections to the legitimate server, pushing AV-disabling code to the device through path traversal, and then planting anything he/she likes on the compromised device.
image source: research.checkpoint.com
Are you using a Xiaomi device? Have you been blindly trusting the Guard Provider app? Share your thoughts in the comments below, and help us raise awareness by sharing this story through our socials, on Facebook and Twitter.