WP-VCD Still Remains The Biggest Threat for WordPress Websites
- The WP-VCD malware strain is still the most prevalent and common problem in the WordPress ecosystem.
- The more websites are infected by this malware, the higher the Google rank of the distribution channels gets.
- A solid method to keep your website safe is to refrain from installing themes and plugins from unknown sources.
As reported by Wordfence, the WP-VCD malware strain is continually evolving and getting around technical blocks. The "love" from malware writers and special attention from the actors is keeping the tool relevant and active in current campaigns that target the WordPress ecosystem. Last time we talked about WP-VCD was back in November when a surge of infections that came through pirated plugins troubled the community. As it seems, the distribution of WP-VCD continues at the same pace right now, and the channels of distribution are similar.
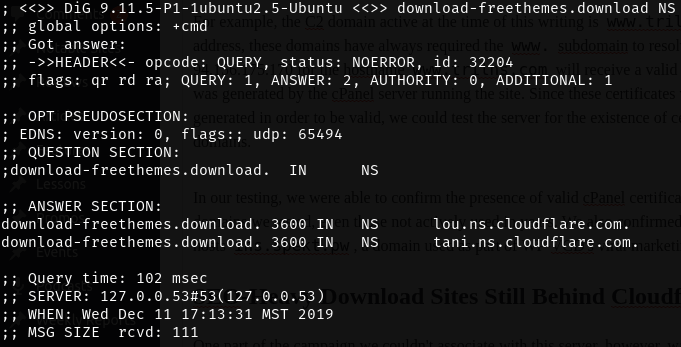
WP-VCD is a specialized malware tool that targets WordPress websites. Its main function is to monetize for the actors with the use of malvertising scripts. Redirects to malvertizing or phishing web pages is also a common side-effect of WP-VCD infections. Another element that is never missing is the search engine ranking boost for the distribution channels through the exploited websites. So, the more websites are infected by WP-VCD, the more aggressively it is promoted and further distributed, which creates a global-scale problem. As for the malware’s resilience, the C2 domain can be changed on the fly, while the actors like to use DNS routing through legitimate CDNs to avoid getting identified.
In almost all cases, the problem starts with the installation of a WordPress plugin that has been infected with WP-VCD. These are usually pirated plugins that are used by admins who don’t want to pay for a safe version. However, they can also be free plugins that are distributed via fake channels and spoofed websites. These websites manage to rank higher among Google search results during periods of massive infections, so people should be very careful with the software sources they trust.
Source: Wordfence Blog
Last month, Cloudflare took action against the actors who used their CND, so the latter were forced to move to AliDNS. According to data that was published by Cloudflare, the primary server behind this latest campaign is linked to Verdina LTD, a Belize-based company that operates infrastructure in Bulgaria. According to Wordfence, this is probably not coming directly from the company, but by cybercriminals who compromised its systems to launch their attacks. This is how and why the C2 rotation is happening anyway.
If you want to stay away from the dangers of WP-VCD, always download WordPress themes and plugins from the official websites of their respective developers. If you can’t afford to pay for something, it is preferable to use a free, inferior, but safe alternative.
Have you ever stepped on the trap of using a nulled plugin that wreaked havoc on your website? Share the details with us in the comments down below, or on our socials, on Facebook and Twitter.