The “Winnti” Group Is Now Actively Targeting the Gaming Industry
- The Winnti Group is deploying yet another custom modular backdoor to hit gaming companies.
- The Chinese hackers are going after makers of MMORPG titles based in South Korea and Taiwan.
- The backdoor and its modules were using a stolen code-signing certificate that has now been revoked.
The Chinese APT hacking group known as “Winnti” is back to targeting its favorite field - the gaming industry. We have looked into this activity back in April through a report by QuoIntelligence, who tracked the hackers going after the creator of the “Ragnarok Online” MMORPG title, Gravity. Now, another report by ESET has been published, revealing that Winnti is actually targeting many more gaming companies based in South Korea and Taiwan. The group is compromising their services, taking control of their build systems, and possibly even injecting arbitrary code into the game executables.
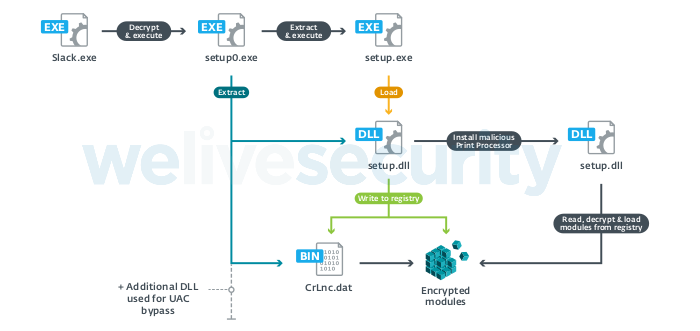
According to the ESET report, Winnti has been using two variants of the PipeMon malware, which is a novel backdoor that we haven’t seen before. The first version could be a testing one, as the second version is more whole, but both are featuring an installer that drops the payload in the Windows Print Processors directory and then restarts the print spooler service to establish persistence. The loader is encrypted and stored within a library file named “setup.dll” or “core.dll,” which sets the required registry value. From there, more encrypted payloads like the “CrLnc.dat” are loaded, decrypted, and executed, as shown in the following process diagram.
Source: We Live Security (ESET)
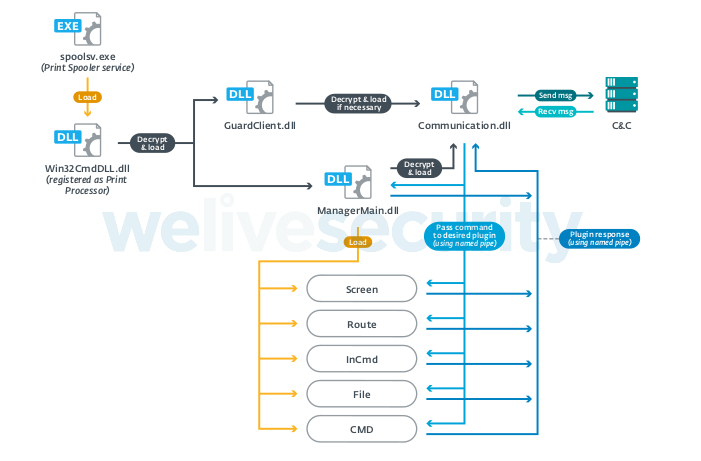
PipeMon is a modular backdoor which got its name from the fact that it uses multiple named pipes for inter-modular communication. The four main modules that have been identified by ESET researchers are the following:
- Win32CmdDll – Decrypts and loads other modules like ManagerMain and GuardClient.
- GuardClient – Periodically checks whether the Communication module is running and loads if needed.
- ManagerMain - Contains the encrypted C&C domain, loads the Communication module, and executes commands that it receives through it.
- Communication – Manage communications between the modules and the C2 server via named pipes.
Other modules that are loaded on-demand through commands are the Screen, Route, CMD, InCmd, and File, but ESET couldn’t retrieve any of these for analysis. The following diagram shows how the whole process would work.
Source: We Live Security (ESET)
Finally, PipeMon modules and installers are all signed with a valid certificate that will help the malware pass through AV protection layers. The certificates were stolen, and the owner has already revoked them after ESET informed them of the issue. This is another case of Winnti deploying a custom modular backdoor and a demonstration of the particular group’s sophistication. For now, ESET uncovered their operation, and the researchers managed to decrypt the hardcoded C&C IP addresses and domain names, providing us with the following four:
- 154.223.215.116, ssl2.dyn-tracker.com, #client.gnisoft.com
- 203.86.239.113, ssl2.dyn-tracker.com, #client.gnisoft.com
- 203.86.239.113, www2.dyn.tracker.com, #nmn.nhndesk.com
- ssl.lcrest.com