Windows GDI Flaws Expose Systems to Critical Threats, Including RCE and Data Leaks
- Three flaws disclosed: Security researchers identified three significant security vulnerabilities in the Windows Graphics Device Interface (GDI).
- Critical impact: These include a critical vulnerability (CVE-2025-53766) that could allow for remote code execution without user interaction.
- Patches released: Microsoft has addressed these vulnerabilities in its Patch Tuesday updates for May, July, and August 2025.
Three security flaws tracked as CVE-2025-30388, CVE-2025-53766, and CVE-2025-47984 within the Windows Graphics Device Interface (GDI), a core component of the operating system, could allow attackers to execute arbitrary code or access sensitive information on affected systems.
Remote Code Execution and Memory Exposure Risks
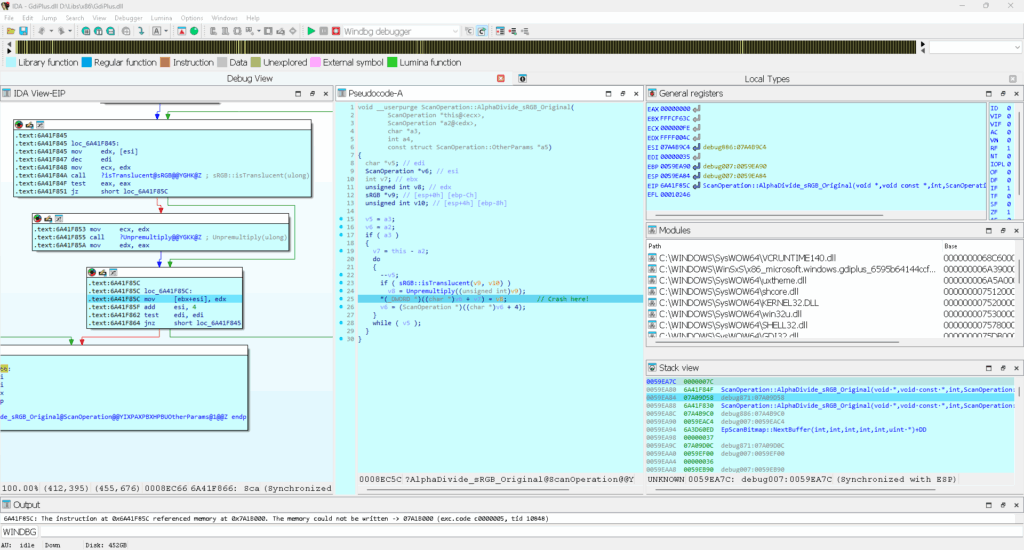
The identified issues highlight persistent risks in how Windows processes graphical elements, particularly within Enhanced Metafile (EMF) formats, according to a recent Check Point Research (CPR) report.
The most severe of the discovered flaws, CVE-2025-53766, is rated critical and could enable remote code execution (RCE). This vulnerability can be exploited over a network without requiring any user interaction, making it a high-risk threat, especially for web services that parse specially crafted EMF+ metafile images.
Another vulnerability, CVE-2025-30388, was found to be an out-of-bounds write issue that could also lead to RCE.
The third flaw, CVE-2025-47984, allows for memory exposure due to an incomplete patch for a previously identified vulnerability (CVE-2022-35837), leading to information disclosure. The research demonstrated that malformed RECT objects in EMF records could trigger these dangerous memory operations.
Microsoft Security Patches Address Flaws
Microsoft released patches to address all three vulnerabilities. The fixes were included in the monthly Microsoft security patches released in May, July, and August 2025.
The updates correct the flawed logic in GdiPlus.dll and gdi32full.dll by introducing proper validation checks for graphic object dimensions and correcting offset arithmetic to prevent out-of-bounds memory access.
Users are strongly advised to ensure their systems are updated with these latest security patches to mitigate the risks posed by these vulnerabilities.
Last month, security researchers discovered that a critical Redis RCE vulnerability, CVE-2025-49844, exploits a 13-year-old UAF bug.