Windows Decoy Dog Trojan Hits 48 Russian Government and Key Companies
- A Windows version of the Decoy Dog malware was found targeting government agencies in Russia.
- There were 48 total victims, including IT, space industry, and energy companies, as well as telecom providers.
- The threat actors presumably targeted these companies for trusted relationship attacks.
The Power Technologies security firm reported that a cybercriminal group called Hellhounds, which keeps attacking the infrastructure of Russian companies via the Decoy Dog backdoor on Linux hosts, is now targeting Windows-based infrastructure. To date, it has compromised 48 victims in Russia in the IT, medical, telecommunication, security, retail, transport and logistics sectors, as well as the mining and space industries.
The researchers say evidence indicates that the threat actor has been targeting Russian companies since at least 2021 and developing the malware since November 2019. The report describes previously unknown details on the group's toolkit and obfuscation methods.
Power Technologies Security reported two incidents in which attackers breached the victims' infrastructure via a contractor, compromising SSH login credentials to install the Decoy Dog backdoor. The C2 server revealed the malicious actor disguised Decoy Dog as ISO images for the iMind online meeting, video conferencing, and webinar service.
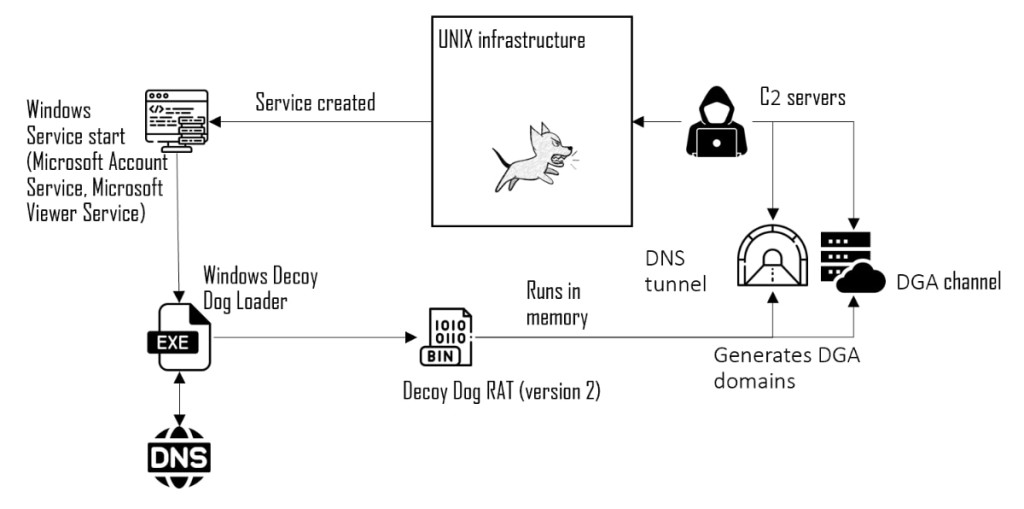
Decoy Dog is a custom variant of the open-source Pupy RAT that significantly extends the malware’s capabilities and ensures persistence on an infected host. It uses DNS tunneling to communicate with its command-and-control (C2) server and remotely control compromised devices.
The Hellhounds actors gain access to the infrastructures through supply chain attacks. They manage to remain undetected for years on their networks, leveraging vulnerable Web services and trusted relationships, often disguising their tools as legitimate software processes – including Positive Technologies’ products.
In the first stage, the attackers installed a service named "Microsoft Account Service" or "Microsoft Viewer Service," which decrypts a list of domains inside the .rdata section and the resulting domain names. These are used for obtaining a part of the key for payload decryption, generating legitimate-looking traffic, and getting around sandboxes.
The malicious actor demostranded effort in disguising their activity on the hosts that it compromised, mimicking MaxPatrol SIEM and Microsoft services. The Linux samples showed the malware could not be run without a valid identifier, which is not the case with Windows samples.
In the second stage, the observed decrypted payload was identical to the Linux Decoy Dog version. The malicious actor relied on the well-known Sliver framework with the C2 server 31.184.204[.]42 (ns2.maxpatrol[.]net).