“WastedLocker” to Attack Large Corporations in the United States
- Russian actors were caught preparing large company networks for WastedLocker infections.
- The attacks deployed a set of tools like Cobalt Strike, which help the hackers establish a wide presence.
- The actors are pushing a fake browser update via 150 compromised websites, with the ZIP containing Cobalt Strike.
Symantec researchers are warning about an imminent wave of attacks against multiple American organizations. Reportedly, the threat actors are planning to deploy the “WastedLocker” ransomware strain to cripple corporate networks of key firms, including eight Fortune 500 companies. The motives behind this malicious campaign are purely financial, as it seems. Symantec says they have noticed and recorded cases of network breach and preparatory work for extensive system lock-downs. The actors are using the “SocGholish” JavaScript framework to push fake updates through 150 compromised websites, and then deploy the Cobalt Strike malware to steal credentials, escalate privileges, and move laterally.
All of this preparation is done to establish a presence on a large number of systems in the compromised network, thus having the capacity to cripple a firm’s IT system by encrypting large portions of it. Hitting one or two computers with WastedLocker wouldn’t do much against companies that follow security practices such as network layering and segmentation. This presence-establishing process often takes time, though, and the actors run the risk of getting noticed. The Symantec’s Threat Hunter team already confirmed hacking attempts against 31 organizations based in the U.S. The actors got noticed by Symantec's AI, which identified specific patterns.
Source: Symantec
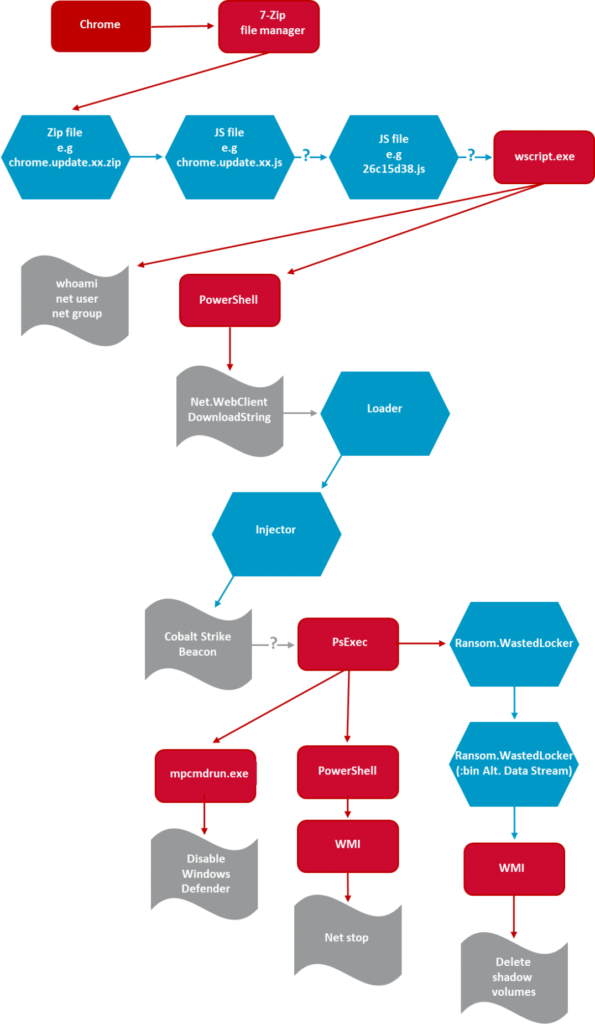
The success of these attacks is again based on the human factor, as the hackers are pushing fake browser updates in ZIP files. Opening the file leads to a series of unfortunate events as detailed in the below flowchart. Windows Defender is unable to stop the infection as the attackers are disabling the scanning of downloaded files and attachments through a PsExec command-line action. In some cases, researchers noticed the removal of all installed definitions or even the disabling of real-time monitoring.
Source: Symantec
As for the attribution, Symantec is limited to assumptions for the time being. WastedLocker is a new ransomware strain that appeared fairly recently and is thought to be the work of the “Evil Corp” group. This is a hacking group that has also been associated with the BitPaymer strain and Dridex banking Trojan. Two Russian hackers have been linked with Evil Corp by the U.S. DoJ, so this could be yet another case of Russian actors going against American firms.
System admins are advised to deploy file-based protection and also intrusion prevention solutions, as they should have anyway. Firms should train their employees to not apply browser updates via ZIP files that appear all of a sudden when browsing on unrelated websites. Symantec has already reported the C2 domains to the corresponding registrars, so the actors will notice a disruption in their operations now.