New VPNFilter Botnet Discovered by Security Researchers JASK and GreyNoise
- The VPNFilter botnet that was discovered which may have infected over 500,000 home and business routers may be back in action.
- VPNFilter was taken down by the FBI but the botnet seems to be making a comeback, and it can potentially affect new routers across the globe.
- According to security researchers Jask and GreyNoise, the same threat was detected which can affect new routers.
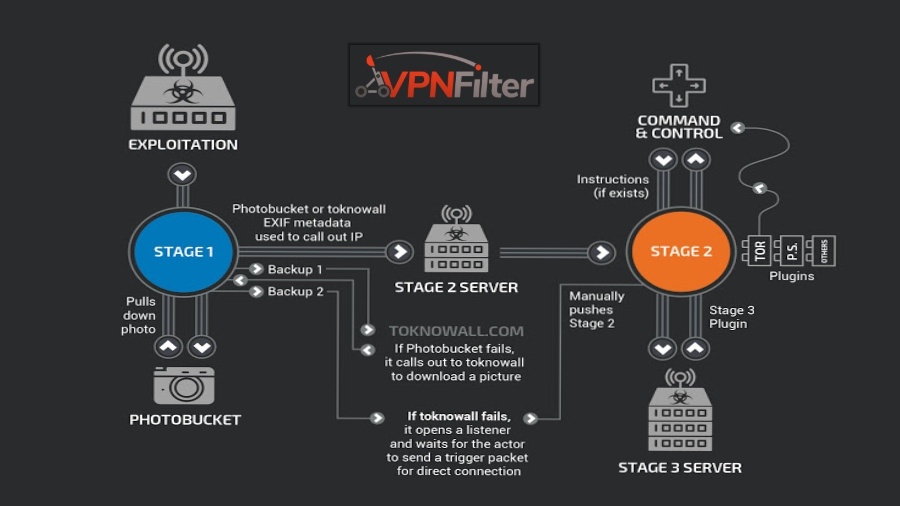
The recently discovered VPNFilter botnet that affected over 500,000 home and business routers seem to be making a comeback. Despite the botnet being taken down by the FBI, a new version of the exploit has surfaced according to security researchers Jask and GreyNoise. The exploit can be used to attack Mikrotik routers which have set the port 2000 to open.
According to the research report, the exploit can only affect Ukrainian routers. While the previous exploit was actively looking for routers and NAS devices from all over the world. The new exploit which was discovered on May 8 is meant to exploit Ukrainian routers only. When the exploit was disclosed to the public, the researchers believed APT28 (cyber-espionage unit) was behind the exploit.
Image Courtesy of FossBytes
The FBI stepped in and shut down most of the VPNFilter infrastructure and shut down the botnet. Most of the command and control protocol was taken over by the FBI. According to Jask and GreyNoise, the exploit is one of the most advanced IOT technology exploits out there, and it can affect routers in multiple stages. The FBI confirmed that it was indeed the APT28 who was behind the attack and it’s not the first time Russian intelligence agencies have attacked Ukrainian IT infrastructure to acquire access to data.
While the first stage of the exploit simply hijacks network data, the latter stages can inject trojan horse programs into computers. Attackers can use the exploit to steal data, remove the OS from a computer and monitor device traffic. After the exploit was made known to the public, manufacturers of routers were asked to patch their firmware to prevent the exploit as soon as possible. If you own a home router, it is recommended to check for firmware updates for potential security patches.