Volkswagen’s Connected Car App Flaws Allow Brute Force Attacks, Expose Owner PII
- Security report underlined critical flaws in the My Volkswagen app account onboarding.
- An attacker could perform brute-force attacks via the OTP field, highlighting critical risks in the automotive IoT ecosystem
- The car owner’s personal details and vehicle service history were also exposed via VIN enumeration.
Volkswagen’s “My Volkswagen” mobile application reportedly has systemic flaws that could impact millions of drivers. Substantial vulnerabilities allow brute forcing and expose user details and car service history.
The flaws were reported to Volkswagen in late November 2024. After a multi-month coordinated disclosure and remediation process, all identified vulnerabilities were patched as of May 2025.
According to a recent security analysis conducted by LoopSec, the app’s onboarding mechanism relies on inputting the vehicle’s VIN and a four-digit OTP sent to the former owner’s phone during the process of connecting a pre-owned vehicle with the My Volkswagen app.
Critically, the OTP field had no effective lockout or rate limiting, making it susceptible to automated brute-force attacks. A straightforward Python script enabled the researcher to quickly cycle through all 10,000 possible codes and gain unauthorized access to vehicle controls and personal data.
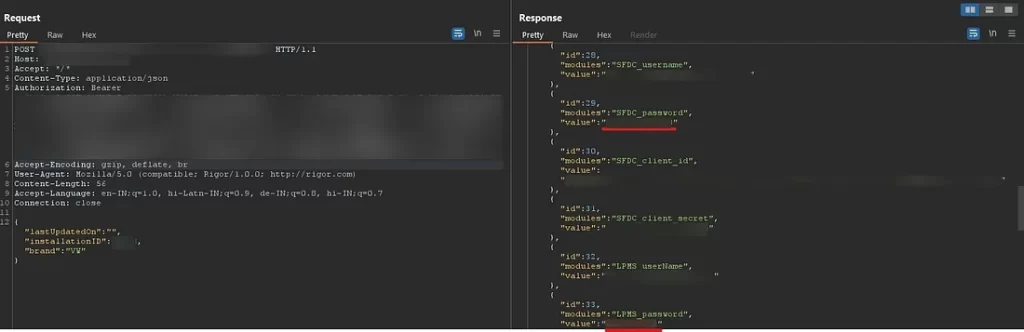
One of the app’s API endpoints leaked sensitive credentials for Volkswagen’s internal environments, including plain text passwords, API tokens, and usernames. These credentials granted access to back-end systems such as payment processors and Salesforce CRM platforms.
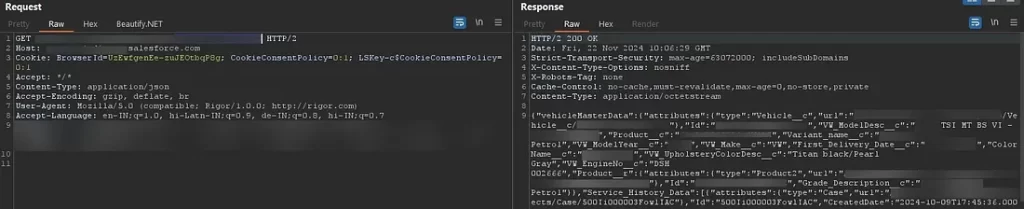
Major endpoints exposed extensive personally identifiable information (PII) simply by enumerating VINs, which are easily visible on any windshield. Data leaked included customer names, phone numbers, home addresses, emails, full vehicle details (including registration and engine number), as well as active contracts and payment records.
Additional endpoints revealed comprehensive service histories, work performed at dealerships, and even educational and driver’s license numbers. These exposures present severe privacy and safety risks.
With unauthorized app access, an attacker could retrieve or modify sensitive vehicle settings, access location, engine diagnostics, fuel status, and exert control over geo-fencing or status reporting features.