Voicemail-Based Phishing Scams Targeting Microsoft Office 365 Users
- A new phishing campaign uses fake voicemail messages to lure recipients into providing their account credentials.
- The actors limit the message to a simple “hello”, which is more than enough in most cases.
- The targets are mainly middle and higher management executives who work in the services sector.
There’s a notable uptick in the use of fake voicemail messages that try to trick Office 365 users into giving away their login credentials. The new campaign was discovered by McAfee researchers, who warn about the luring methods that seem to have notable success in harvesting user credentials. The researchers have found three different phishing kits, but this is likely only the surface of the iceberg at this point.
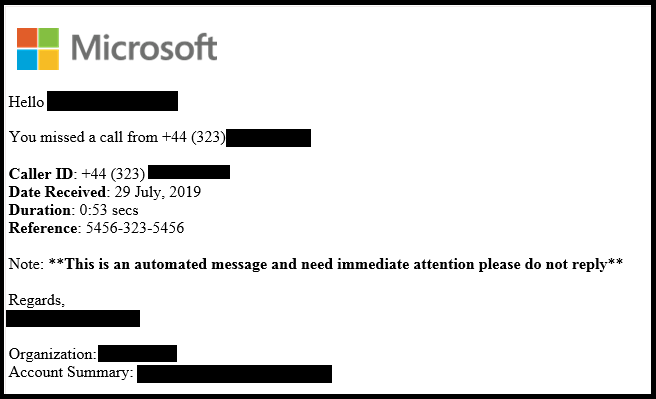
The trick is pretty straight forward. An email arrives informing the recipient that they have missed a call from a particular number, full with details about the date, call duration, etc. The email also contains a short voicemail sample, as the caller is supposed to have left a voice message. The sample autoplay through a .wav file that is embedded in the HTML of the email body, which then redirects the victim to a phishing page that asks for the user’s Microsoft account credentials. This is because the recipient supposedly needs to login to his account in order to access the full message. Those who fall for this bait will have their credentials stolen by the scammers.
Source: Securing Tomorrow
The file attachments that are associated with these campaigns right now are the following:
- 10-August-2019.wav.html [Format: DD-Month-YYYY.wav.html]
- 14-August-2019.html [Format: DD-Month-YYYY.html]
- Voice-17-July2019wav.htm [Format: Voice- DD-MonthYYYYwav.htm]
- Audio_Telephone_Message15-August-2019.wav.html [Format:
- Audio_Telephone_MessageDD-Month-YYYY.wav.html]
If you find any of the above in your inbox, don’t follow the links and don’t insert your account credentials to anything that pops up. Remember, no matter how convincing a login page may seem to be, you should always take a look at the URL bar and check that you are indeed on the official page.
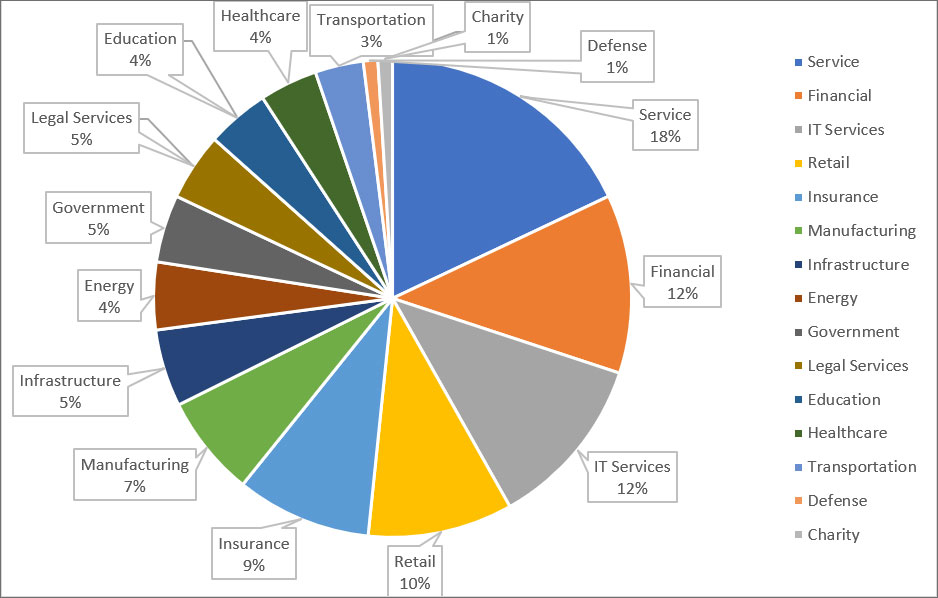
As for the targeted industries, we see a prevalence of the Service, Financial, IT Services, Retail, Insurance, and Manufacturing sectors. The employees that are targeted are engaged between the middle to higher management, as these people hold the keys to an easier and wider corporate network infiltration and BEC compromise potential.
Source: Securing Tomorrow
While this menace is a pretty realistic one, it is nothing compared to deepfaking a CEO’s voice to trick employees into transferring money. AI-generated deepfakes are here and they will work both to our advantage as well as against us. BEC, phishing, and scamming, in general, will undoubtedly be a couple of fields of deployment. That said, and while the above story indicates a certain risk, it is nothing compared to what’s about to become mainstream.
Do you have anything to comment on the above? Feel free to do it in the section down below, or on our socials, on Facebook and Twitter.