Voice Phishers for Hire Are Targeting Corporate VPN Networks
- Voice phishing against the VPN networks of large companies is going rampant right now.
- Actors are calling new employees and pretend to be from the firm’s IT, looking to fix their “VPN issues.”
- Companies could render these attacks useless if only they implemented multi-factor authentication steps.
We are gradually entering an age of highly sophisticated phishing attacks launched by “hackers for hire” groups, and it looks like corporate VPN tools are carrying the burden right now. As reported by Krebs on Security, who claims multiple sources, there’s a notably successful phishing gang operating out there upon paid requests, accessing specific companies and corporate networks on the accounts for those who hire them.
With most companies having their employees working from home right now, voice phishing has gotten a lot more effective, so malicious crooks embrace it.
Related: Using Caller ID Spoofing in “Vishing” Attacks Is Becoming a Growing Problem
The most targeted sectors are the financial, telecommunications, and social media, while the size of the target companies is at the higher end of the spectrum. Typically, the actors call employees who are working remotely, tell them that they’re calling from the IT department of the firm, and they are looking to troubleshoot a problem with the VPN tool.
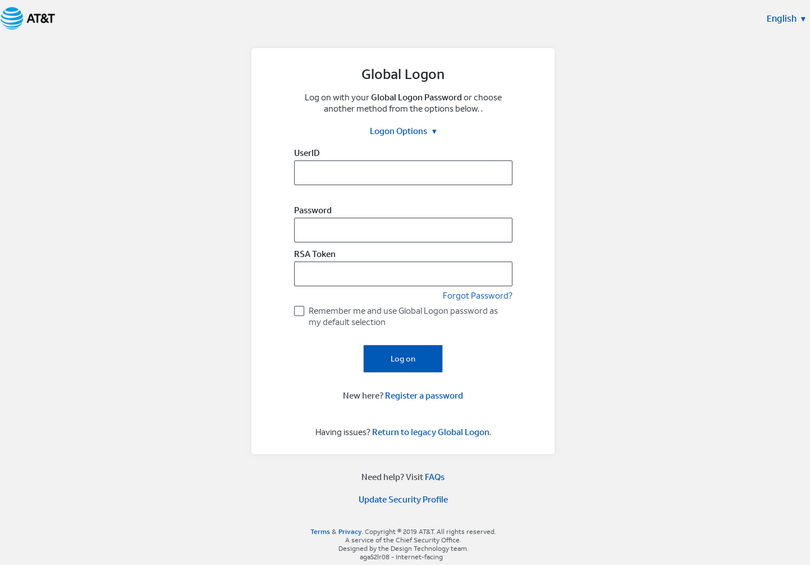
In some cases, the targets are asked to share their credentials over the phone, but most of the time, they are simply directed to a phishing website that is crafted to look legitimate enough.
Source: Krebs on Security
The phishers deploy several tricks to succeed, one being the creation of fake LinkedIn profiles that they attempt to connect with actual employees of the target company.
Moreover, they target new hires in the company, who would be more susceptible to these attacks. As for how they know who is a new hire, LinkedIn is the answer again.
Source: Krebs on Security
The phishing domains used in these campaigns are selected to contain something from the company’s name, followed by terms like “VPN,” “ticket,” “portal,” etc. To make them even more convincing, the crooks insert links in the phishing sites that point to the target company’s online resources, so even if one were to check the legitimacy of the webpage, the cover wouldn’t be blown.
Once the victims enter their credentials on the phishing portal, the actor grabs the username and password while the employee gets an error message. From there, the actors move quickly to access the corporate VPN network before the company realizes the breach and reset the victim’s account.
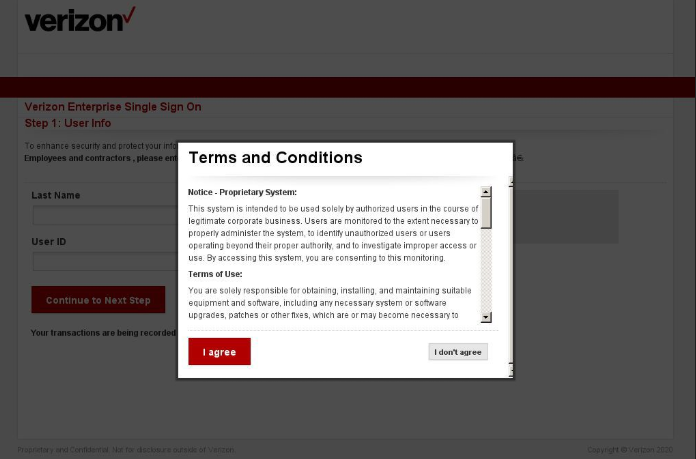
Verizon terms and conditions on a phishing page, Source: Krebs on Security
To hide their identities, the actors register the phishing domains only on registrars that accept Bitcoin payments. Moreover, they create one domain per account, so even if a phishing page gets reported, the rest will stay online. Finally, they only keep the portal online only during the time of an attack, as registrars will only take something down if they catch it in the act.
A simple security measure to take against these phishing actors would be to enable multifactor-authentication for VPN accounts so that stealing the credentials wouldn’t be enough to access the corporate network. Weirdly, even though everyone talks about the need for raised security levels during this pandemic, many large companies are totally bypassing even the most basic precautionary measures.