‘View Media’ Exposed 39 Million User Records on Unprotected AWS Database
- A big marketing firm has exposed a vast user database online for an unknown period.
- The data comprises names, addresses, and phone numbers of about 23.5 million Americans.
- Spamming, phishing, scamming, and social engineering are some of the dire possibilities.
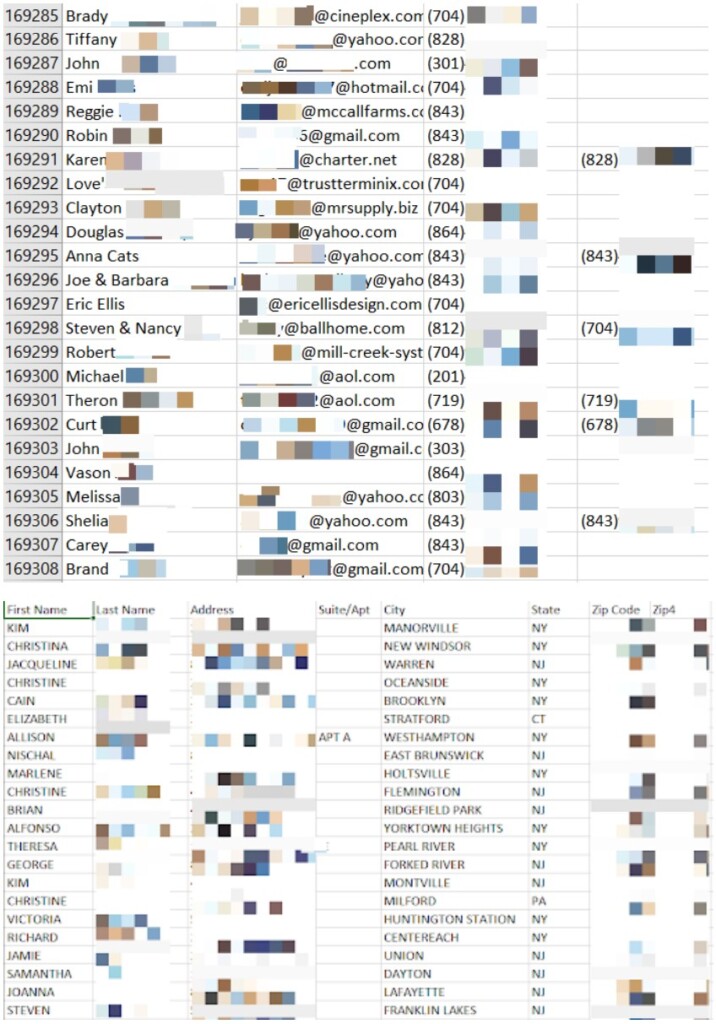
An online marketing company called ‘View Media’ has left a humongous bucket accessible by anyone online after they misconfigured their Amazon Web Services server. The massive database that was left free to access and download contained approximately 39 million user records, mostly belonging to American citizens.
The type of data found there includes full names, email addresses, street addresses, ZIP codes, and phone numbers. That would be enough for scamming and phishing actors to engage in their malicious operations, so go ahead and check by using this tool to figure out whether you’re running a risk from this incident.
CyberNews researchers discovered the database on July 27, 2020. They notified Amazon immediately, as they initially couldn’t tell who owns the data. Amazon closed the bucket two days later, so the chances of this database having been accessed and downloaded are significant.
On August 21, 2020, CyberNews found out that View Media is responsible for this after they reached out to one of the clients mentioned in the statement of work documents. They then contacted the marketing firm, but they are yet to hear back from them.
Source: CyberNews
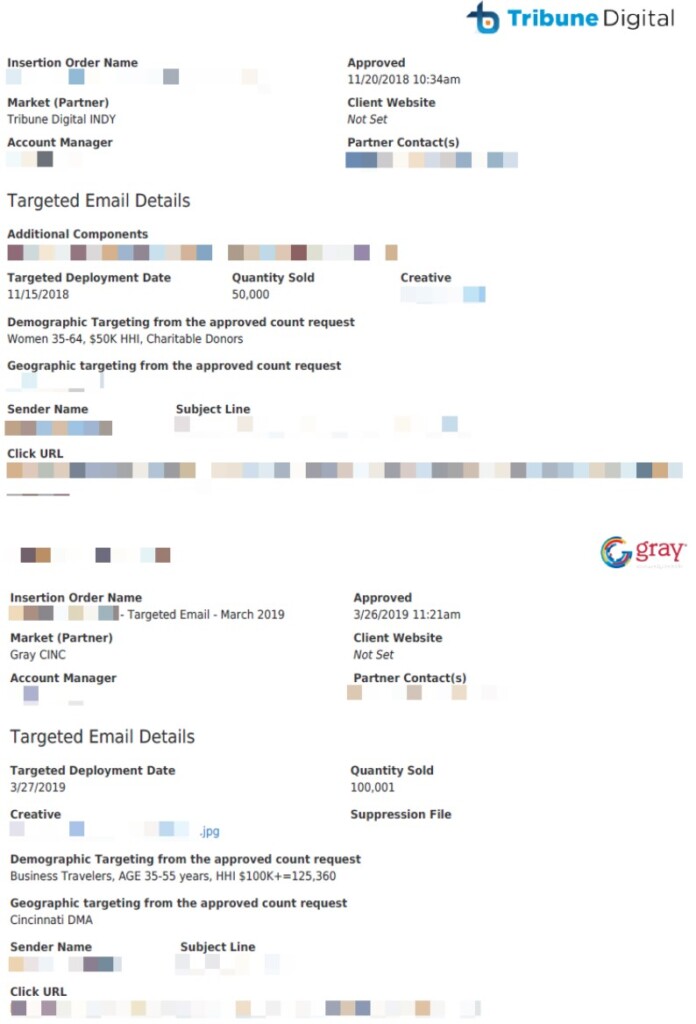
Of the 39 million records logged in 59 CVS and XLS files, the researchers confirmed that 23.5 million are unique entries, so this is the number of the affected individuals. View Media used this data for digital marketing purposes, i.e., sending emails on the account of advertisers.
While the exposed details aren’t highly sensitive, they are still compromising millions of people’s privacy. Email addresses can be changed, but the rest of the information found there is impossible to reset. This practically means that the exposed individuals should stay vigilant against social engineering attempts for a long time.
Source: CyberNews
If you have found yourself in the leak, change the email password on your account immediately. If you receive any suspicious emails, do not click on links or embedded buttons featured in the body, and do not download or try to open any attachments. Also, since phone numbers are included in the leak, SMS links and robocalls are also a possibility.
The database remained online and accessible for an unknown period of time, so your details may have been leaked a long time ago already. However, the large number of records in the database could have helped in this case, as actors need time to scrutinize and actually exploit millions of entries. Still, if the set was exfiltrated, it may be kept to be used in combination with other leaks for the purpose of identity thefts.
Read More:
- The ‘American Payroll Association’ Suffered a Catastrophic Data Breach
- A Trove of Email Addresses Was Left Exposed and Accessible Online
- Unprotected Server Contains Sensitive Data From Various Firms