USB Redirection Software Bug Introduces Novel Way to Launch Cyber Attacks
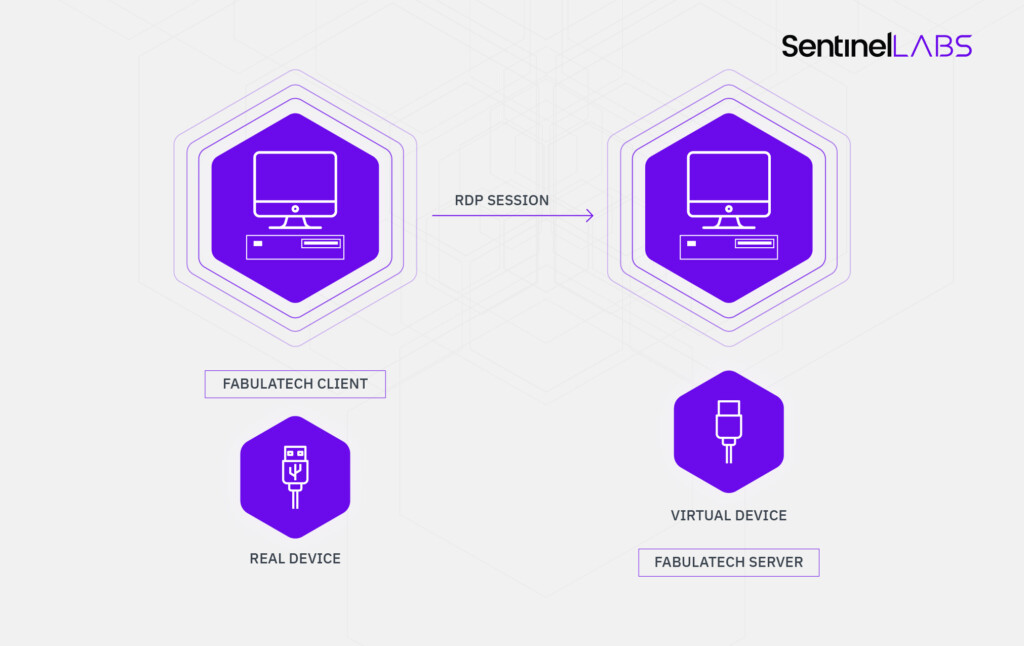
- FabulaTech’s “USB for Remote Desktop” allows hackers to create fake virtual USB devices and launch attacks on the software’s users.
- This is already known among some crooks, as attacks that happened in the wild led to the discovery of the bug.
- The software vendor hasn’t acknowledged or fixed the bug yet, even after three months since it was reported to them.
Researchers from the Sentinel Labs have discovered the potential for abusing CVE-2020-9332 to launch devastating remote attacks over an unsuspecting victim. The software that creates the attack surface is one of “FabulaTech’s” products called “USB for Remote Desktop”. This is a tool that helps admins access USB devices in remote Windows sessions, but it is also introducing hacking risks for the user. Although Sentinel Labs reported their discovery to FabulaTech on January 29, and then again on February 4, 2020, they received no response to this day, and the vulnerability remains unfixed.
Unfortunately, the discovery of the flaw came through the realization of an exploitation event on one of Sentinel Lab’s clients’ computers. Upon investigating the suspicious events, the IT experts found out that someone had planted a virtual USB device on the Fabula server. To make matters worse, the OS fully trusts this device, as it calls an insecure routine (IoCreateDevice) that doesn’t even deal with security descriptors or privilege levels. So, a hacker had created a virtual USB that repeated all I/Os made by the real device, allowing non-privileged users to access data that should be out of their reach.
Source: labs.sentinelone.com
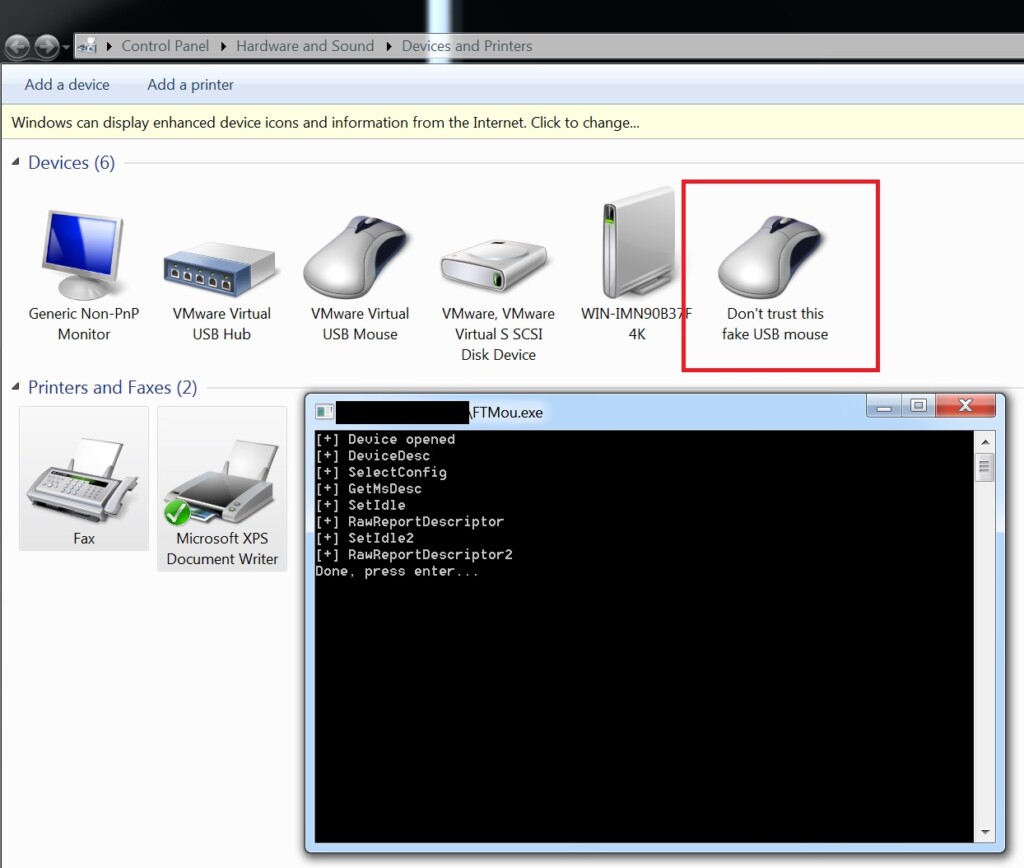
The implications of this flaw are multiple and severe. A hacker could add a fake mouse device and click on consent windows, or add a USB keyboard and type malicious commands on the target system. Going even further, Sentinel Labs mentions the possibility of adding a USB-Ethernet network card to perform man-in-the-middle attacks. The researchers dived deeper into the technical aspect of this vulnerability, and they developed a proof of concept (PoC) to present to FabulaTech and convince them of the criticality of the problem. The PoC involved the addition of a fake (virtual) USB mouse device by using a VendorID 0E0F and ProductID 0003 to abuse the vulnerable driver, but it could be anything, really.
Source: labs.sentinelone.com
As the vendor of the vulnerable software hasn’t responded to the reports and considering it’s been over three months since the initial discovery and reporting, you are advised to refrain from using FabulaTech’s “USB for Remote Desktop.” The fact that the whole investigation started after someone exploited this flaw in the wild should be enough to convince you of the dangers. Whatever FabulaTech’s response will be now that the matter has gone public, this case doesn’t give a good impression on the company’s reflexes to fix critical security issues.