The US Sanctions Three Individuals Linked to Vicious ‘911 S5’ Botnet
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) took decisive action on Tuesday, imposing sanctions on three Chinese nationals and three Thailand-based companies. These entities were found to be instrumental in operating the nefarious 911 S5 botnet-like infrastructure that siphoned off billions of dollars from the U.S. government masked by residential proxies.
"These individuals leveraged their malicious botnet technology to compromise personal devices, enabling cybercriminals to fraudulently secure economic assistance intended for those in need and to terrorize our citizens with bomb threats," Under Secretary of the Treasury, Brian Nelson, said in the official press release.
OFAC sanctioned Yunhe Wang, 35, on accusations of being the primary administrator of 911 S5 and three companies (Spicy Code Company Limited, Tulip Biz Pattaya Group Company Limited, and Lily Suites Company Limited) based in Thailand for being owned or controlled by Wang. The actor was a registered subscriber of MaskVPN and DewVPN, specific to the botnet operation.
Another is Jingping Liu, 58, sanctioned for laundering proceeds from the botnet, mainly virtual currency “converted into U.S. dollars using over-the-counter vendors who wired and deposited funds” into his bank accounts.
Last on the list is Wang's attorney Yanni Zheng, 50, who the Treasury said “participated in numerous business transactions, made multiple payments, and purchased real estate property on behalf of Yunhe Wang, including a luxury beachfront condominium in Thailand.”
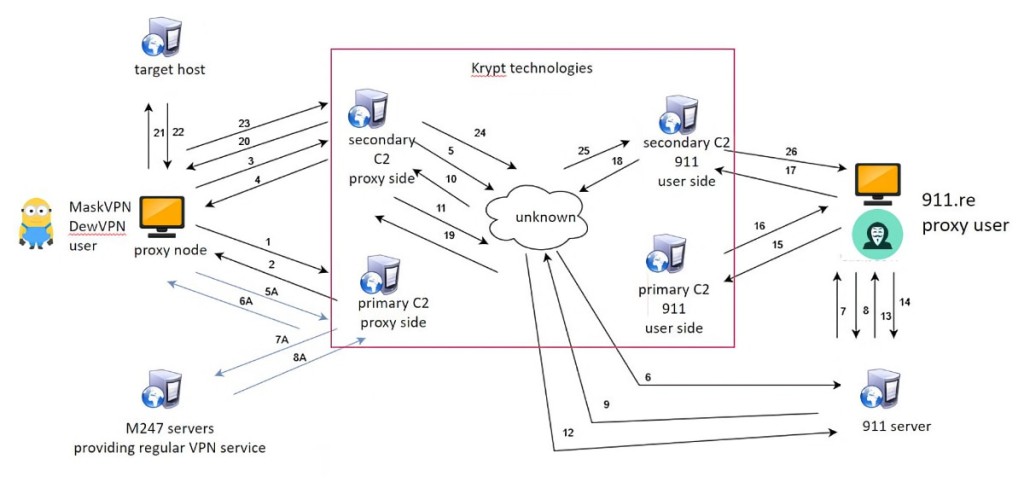
The 911 S5 was a malicious Residential Proxies As A Service (RPAAS) that operated by stealing residential IP addresses. These addresses were then used to mask cybercriminal activity, leading back to the infected devices. The 911 S5 paid users would select preferred IP addresses of compromised computers to use in their cyberattacks.
This illegal residential proxy service offered free access to two legitimate VPNs, Mask VPN and Dew VPN, which simultaneously installed malware that added their IP addresses to the 911 S5 botnet through a permanent TCP socket connection made to the C2 servers of the 911.re backend infrastructure, compromising some 19 million IP addresses.
These were used to file tens of thousands of applications for the Coronavirus Aid, Relief, and Economic Security (CARES) Act programs, including Small Business Administration loans and unemployment insurance funds in over a dozen states, which saw billions stolen from the US government – at least $20 million in U.S. Covid relief benefits.
The stolen residential IPs were also linked to several bomb threats made in the U.S. in July 2022, immediately after which the service went offline due to an alleged hacking incident, which was first reported by Krebs on Security.