US Indicts 16 Russian Nationals in DanaBot Case as Part of Global Operation Endgame
- The U.S. DoJ unsealed criminal charges against 16 individuals allegedly involved in DanaBot operations.
- The Russian nationals are accused of operating the MaaS platform and distributing the malware.
- This action is part of Operation Endgame, a global initiative that disrupted ransomware delivery chains.
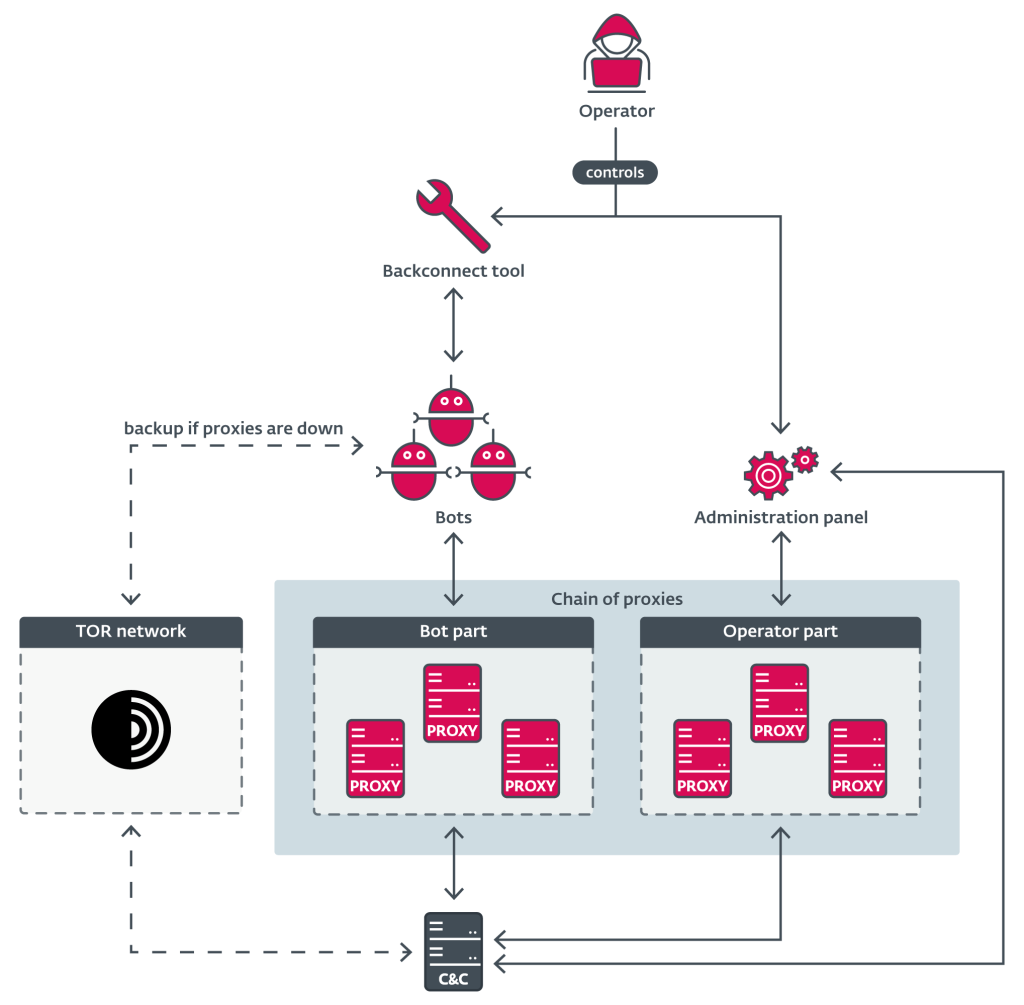
Several individuals were accused of operating and distributing DanaBot, a major malware-as-a-service (MaaS) platform active since 2018, which specializes in credential theft and banking fraud.
The U.S. Department of Justice has unsealed criminal charges against 16 Russian nationals linked to DanaBot, whose operators sold access for up to $4,000 per month to more than 40 affiliates. Half of the indicted individuals’ real names were revealed, and the other half were mentioned by their alias.
Partners such as ESET, Proofpoint, Microsoft, Zscaler, Lumen, and others played vital roles in intelligence gathering, technical analysis, and remediation efforts.
The FBI’s operation is notable for capitalizing on a series of self-infections, as several DanaBot operators unwittingly infected their own machines, exposing their real-world identities through uploaded credentials and internal communications.
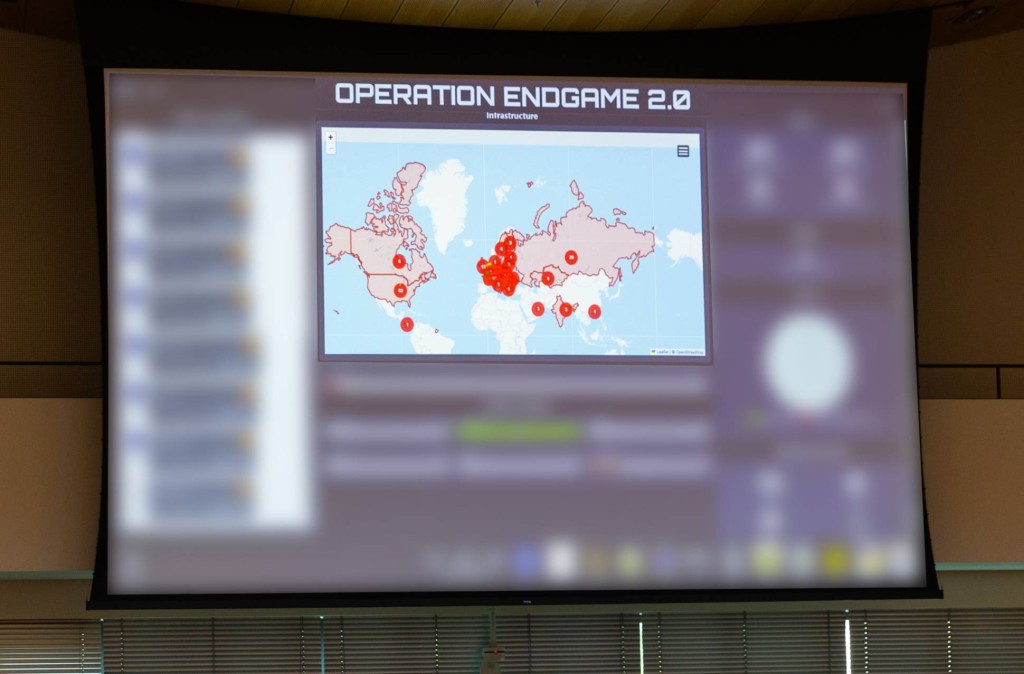
The initiative culminated in the seizure of DanaBot command-and-control servers, with support from global partners across law enforcement and the private sector.
Concurrently, Europol, Eurojust, and allied agencies announced the latest phase of Operation ENDGAME. By coordinating from May 19 to 22, authorities dismantled critical infrastructure behind multiple malware strains used to deliver ransomware.
This led to the takedown of approximately 300 servers and 650 domains, the arrest of 20 suspects, and the seizure of €3.5 million in cryptocurrency.
Notably, strains such as Qakbot, DanaBot, Bumblebee, Trickbot, Lactrodectus, HijackLoader, and Warmcookie were disrupted. Authorities seized a total of over €21 million and issued 20 international arrest warrants, with 18 suspects soon to be added to the EU Most Wanted list.
These efforts struck at successor groups that emerged after last year’s takedown. With over 300,000 infections and upwards of $50 million in global losses, this takedown is among the largest targeting Russian-language cybercriminal circles.
Investigations revealed not only widespread credential theft and financial fraud but also an evolution in DanaBot’s usage.
A second version of the malware, deployed in 2021, was leveraged for espionage, targeting military, diplomatic, and NGO systems in multiple countries, including the U.S., Germany, the UK, Belarus, and Russia.