UpCrypter Phishing Campaign Delivers DCRat, Babylon RAT, PureHVNC
- RAT delivery: Security researchers observed a global campaign delivering PureHVNC, DCRat, and Babylon RAT, among others.
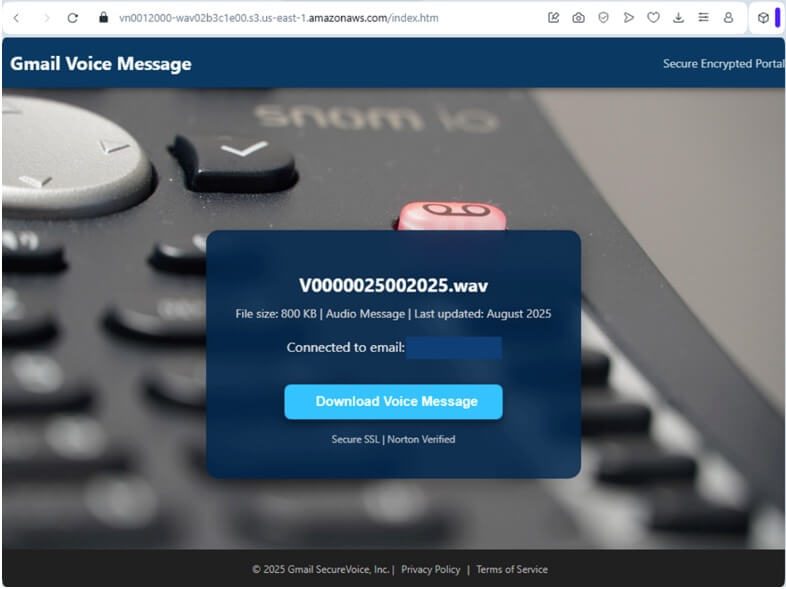
- Enterprise campaign: Phishing emails with voicemail or purchase lures redirect to spoofed pages featuring the victim’s email and company logo.
- Malware delivery: The targets are urged to download a file via an archive that ultimately gives attackers long-term control.
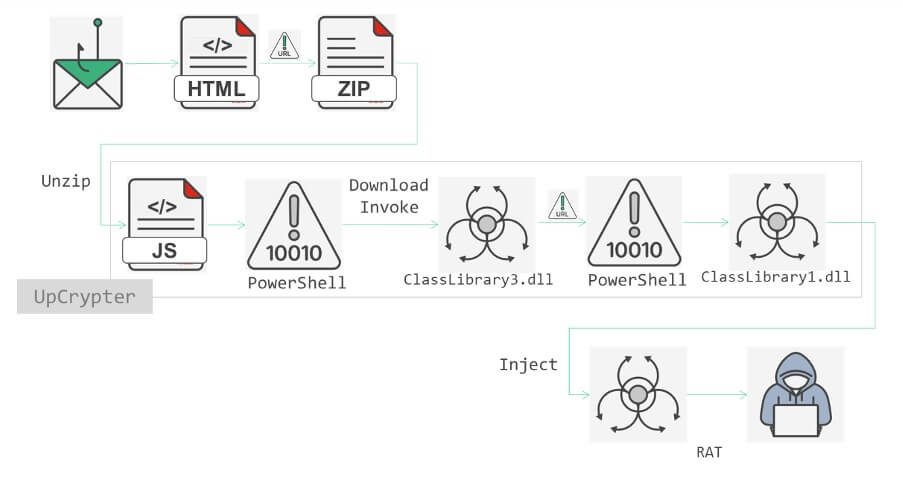
A sophisticated UpCrypter phishing campaign has been identified targeting companies globally through carefully orchestrated emails designed to deliver multiple remote access tools (RATs) such as DCRat, Babylon RAT, and PureHVNC.
Multi-Vector Attack Chain Analysis
The attackers are employing dual-themed lures to maximize target engagement, FortiGuard Labs' analysis reveals. Primary variants include voicemail-themed messages with subjects like "Missed Phone Call" and purchase order notifications containing Chinese characters.
Each phishing email contains HTML attachments featuring obfuscated JavaScript that redirects victims to personalized landing pages incorporating the target's email domain and corporate logos.
These sophisticated phishing sites employ dynamic content generation, fetching domain-specific imagery to enhance credibility while suppressing error messages through anti-analysis techniques.
Upon successful social engineering, victims receive ZIP archives containing heavily obfuscated JavaScript files designed to execute PowerShell commands with elevated privileges.
Technical Infrastructure and Evasion Methods
The UpCrypter framework demonstrates advanced anti-analysis capabilities targeting forensic tools, debuggers, and sandbox environments. Detection of analysis tools triggers immediate system restart and artifact deletion, effectively terminating investigative sessions.
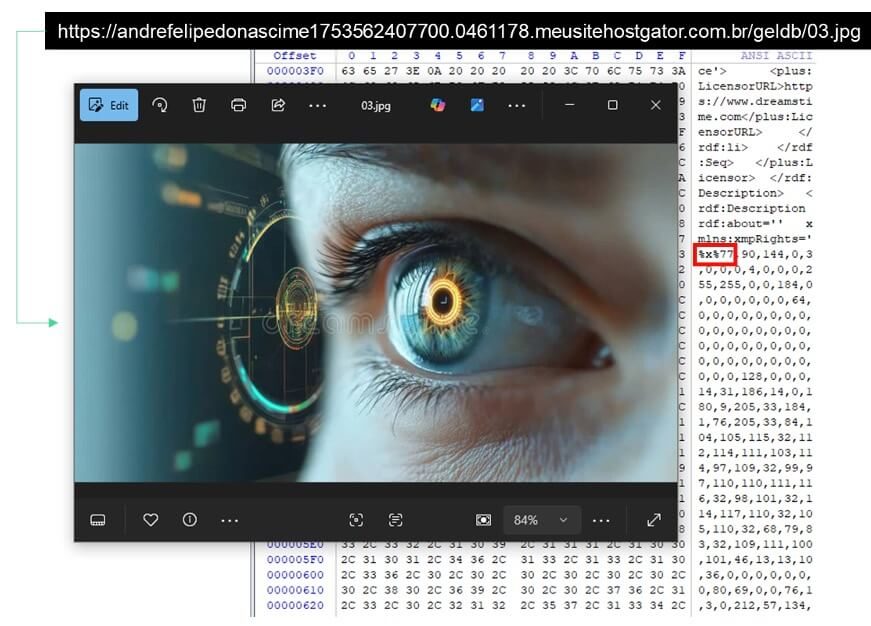
The payload delivery mechanism employs steganography to embed malicious code within image files and plain text for loader data. This dual-format approach significantly enhances evasion rates against static detection systems.
The malware establishes persistence through Windows Registry modification and deploys multiple RATs, including PureHVNC, DCRat, and Babylon RAT, which enable full remote control of compromised systems.
Global Impact and Cybersecurity Threats 2025 Implications
Telemetry data indicates rapid campaign expansion, with detection counts doubling within two weeks across manufacturing, technology, healthcare, construction, and retail sectors.
This UpCrypter phishing campaign represents a paradigm shift toward weaponized, publicly available tools enabling comprehensive network compromise rather than simple credential harvesting.
Frankie Sclafani, Director of Cybersecurity Enablement at Deepwatch, described the campaign as “a highly sophisticated and dangerous threat” and recommended multi-layered defenses such as robust email filtering, comprehensive staff training, and behavioral analysis.
J Stephen Kowski, Field CTO at SlashNext Email Security+, similarly warned that the campaign’s personalized phishing pages and RAT payloads enable long-term system control, stressing the importance of blocking such threats at the email and web layer.
To stop malicious scripts like those used in this campaign, security teams should enforce PowerShell script signing, use Constrained Language Mode, restrict PowerShell execution for standard users, and implement Application Allowlisting.
Sclafani noted that this control can “prevent the malicious JavaScript droppers and subsequent RAT payloads from running, neutralizing the threat even if a user is tricked into downloading the file.”
“Looking for the chain of events of opening an HTML attachment in email that leads to PowerShell usage provides an easy and quick win for detection (and hopefully prevention),” said John Bambenek, President at Bambenek Consulting, adding that few users actually need PowerShell access.
In other news, TechNadu this month reported on a Gmail voicemail phishing scam that uses malicious CAPTCHA on fake websites to steal user credentials and fake Gmail security alerts prompting users to reset passwords via email and phone.