University Students Discover Access Flaws in 16 IoT Cameras
- A team of researchers has experimented with the potential for domestic abuse and harassment via IoT flaws.
- The students have found that 16 out of 19 popular IoT camera models are susceptible to this type of exploitation.
- IoT vendors focus more on the usability of the devices rather than securing them against access peculation.
Three students of the Florida Institute of Technology have discovered authentication and access control design flaws in 16 models of IoT (Internet of Things) cameras. These flaws could allow someone to access video and audio feeds from the devices, essentially stalking the owners or other users of the device without having to engage in skillful hacking. The team of researchers presented a paper where they describe an attack methodology that demonstrates the possibility to persist even after the revocation of the user access. Moreover, they evaluate the susceptibility of 19 widely used IoT cameras and smart doorbell devices, finding that 16 of them are vulnerable to exploitation.
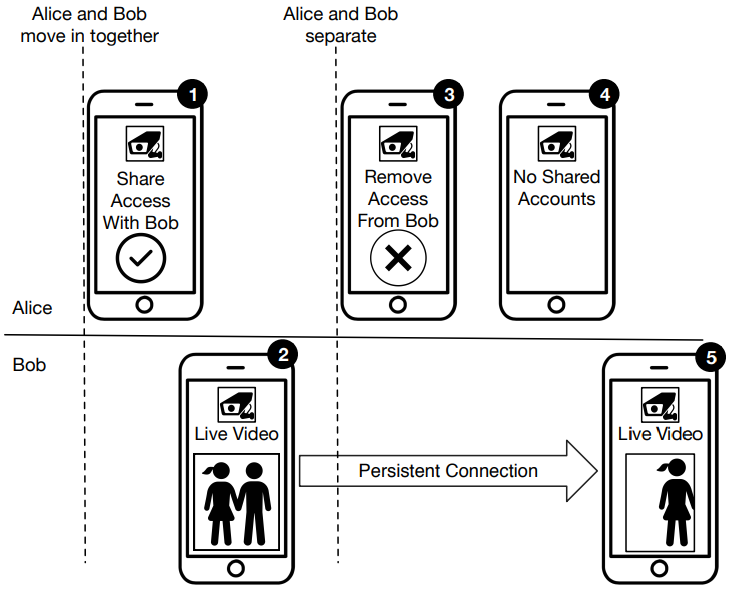
Instead of exploring external attack scenarios launched by hackers, the students tap into access abuse done in the context of domestic violence, stalking, and harassment. The researchers' example involves two people (Bob and Alice) who share a residence and have access to the same IoT. At some point, Alice, who is the owner of the device, revokes Bob's access when the two separate. While the API is no longer serving the barred out user with a new token, the old token is still valid, allowing Bob to surreptitiously maintain access to the camera feeds. Alice would falsely think that Bob doesn't have access to the camera, and she wouldn't have a way to figure out what is going on.
The flaws are systemic and are analyzed in problems such as the lengthy token expiration, login auditing problems, and relaxed access control in general. Starting with the last one, vendors tend to throw encryption out of the window to deliver media feeds with low latency. The problem of password reuse has also been highlighted in the past, as credentials spraying has uncovered fundamental problems in Ring security before. And as for the token expiration, most devices maintain timeouts that last for quite a few hours, if not indefinitely, and they do this for reasons of user comfort. This approach, of course, comes at the expense of security.
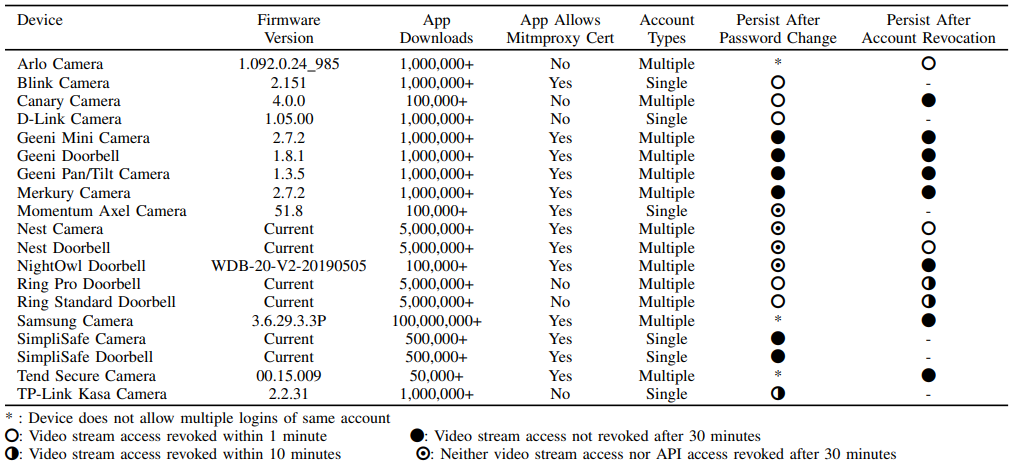
The following table gives the test results on 19 IoT models that demonstrated various susceptibility levels to the attacks. As can be easily deduced from the data provided below, many millions of users and owners of IoT devices are running the risk of being eavesdropped by malicious individuals.
Of course, the above models are just some of the most popular IoTs in the market, so countless more models could be vulnerable to exploitation. Your best bet would be to keep the software (companion app) and the device firmware up to date and let the device stay connected to the network only when you need to use it. Plus, set up a separate WiFi network for your IoT device ecosystem and reset your credentials often.