University of Pennsylvania Data Breach Exposes Data of Almost 624,000 Individuals, Including Donors
- Donor Leak: A major data breach at the University of Pennsylvania has compromised the personal information of approximately 624,000 individuals, including donors.
- Sensitive Information Disclosed: The compromised dataset encompasses names, residential addresses, and, for certain records, sensitive demographic data.
- Incident Timeline: The October 2025 breach resulted in exfiltrated data subsequently published online in February 2026 and was claimed by ShinyHunters.
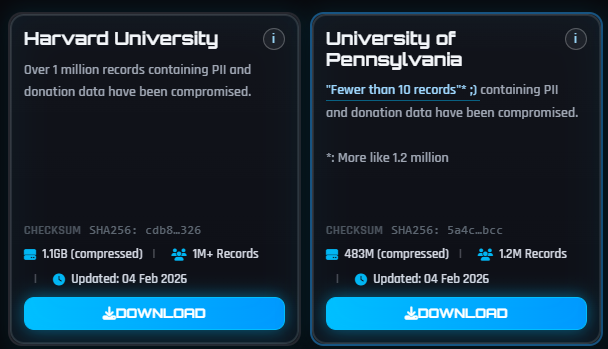
The University of Pennsylvania data breach was added to the Have I Been Pwned (HIBP) breach notification service on February 16, 2026, revealing that nearly 624,000 unique email addresses were compromised, along with their associated sensitive data. The cyberattack, which occurred in October 2025, targeted the university's donor database infrastructure.
While the breach was identified in Q4 2025, the incident escalated significantly in February 2026, when over 3.5 gigabytes of exfiltrated data were published on cybercriminal forums after a hacker affiliated with ShinyHunters claimed responsibility for this attack and a Harvard compromise.
Donor Database Compromised
The UPenn data breach contains 623,800 unique email addresses, along with complete personal identifiers and residential addresses. For a substantial subset of donor records, the exposure encompasses additional sensitive personal identifiers.
The leaked data includes:
- Charitable donations
- Dates of birth
- Email addresses
- Genders
- Income levels
- Job titles
- Names
- Physical addresses
- Religions
- Salutations
- Spouses names
Mass spam emails were sent from multiple Penn-affiliated email addresses in October, criticizing the University’s security measures and admissions practices, according to reports. Attackers demanded a $1 million ransom, which the university reportedly failed to pay.
“Penn’s cybersecurity in terms of resistance to our specific types of attacks was average compared to that of peer institutions – maybe slightly below average,” ShinyHunters reportedly told The DP.
Cybersecurity for Educational Institutions Under Scrutiny
Academic institutions maintain extensive repositories of high-value data assets. This data profile provides malicious actors with comprehensive intelligence for advanced social engineering operations and identity compromise scenarios.
“We attacked Penn and other Ivy Leagues in hopes of getting a settlement payment from them because they store highly sensitive data in CRM apps like Salesforce and in the cloud,” the hackers stated, according to The DP.
In November, UPenn announced investigating an intrusion linked to the Oracle EBS vulnerability. Mandiant this month reported on the ShinyHunters extortion tactics, vishing, and SSO compromise of cloud environments.