UNC6032 Uses Fake ‘AI Video Generator’ Ads on Facebook and LinkedIn to Spread Infostealers and Backdoors
- Threat actor UNC6032 leverages the popularity of AI video-generation tools Luma, Canva, and Kling.
- Whatever the prompt, the user receives an archive containing malware, ultimately installing XWorm and more.
- An analysis of Facebook’s Ad Library revealed more than 30 unique malicious domains.
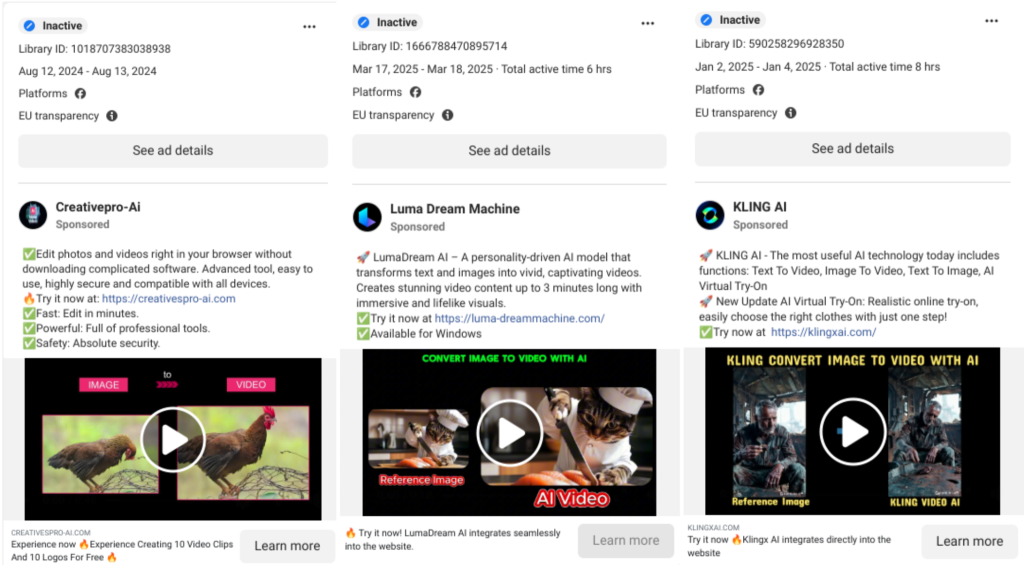
Active since mid-2024, this UNC6032 campaign uses deceptive social media ads to direct users toward fake AI tool websites, such as bogus versions of “Luma AI,” “Canva Dream Lab,” and “Kling AI.”
These ads, reaching millions of users, predominantly appear on Facebook and LinkedIn, but analysts believe similar campaigns are underway on other social and ad platforms, a Mandiant Threat Defense cybersecurity report says.
Google Threat Intelligence Group (GTIG) assesses UNC6032 to have a Vietnam nexus.
Attackers construct these fraudulent sites to closely mimic legitimate AI tools. Victims are encouraged to upload a prompt to generate a video, but regardless of their input, the site delivers a ZIP archive containing malware.
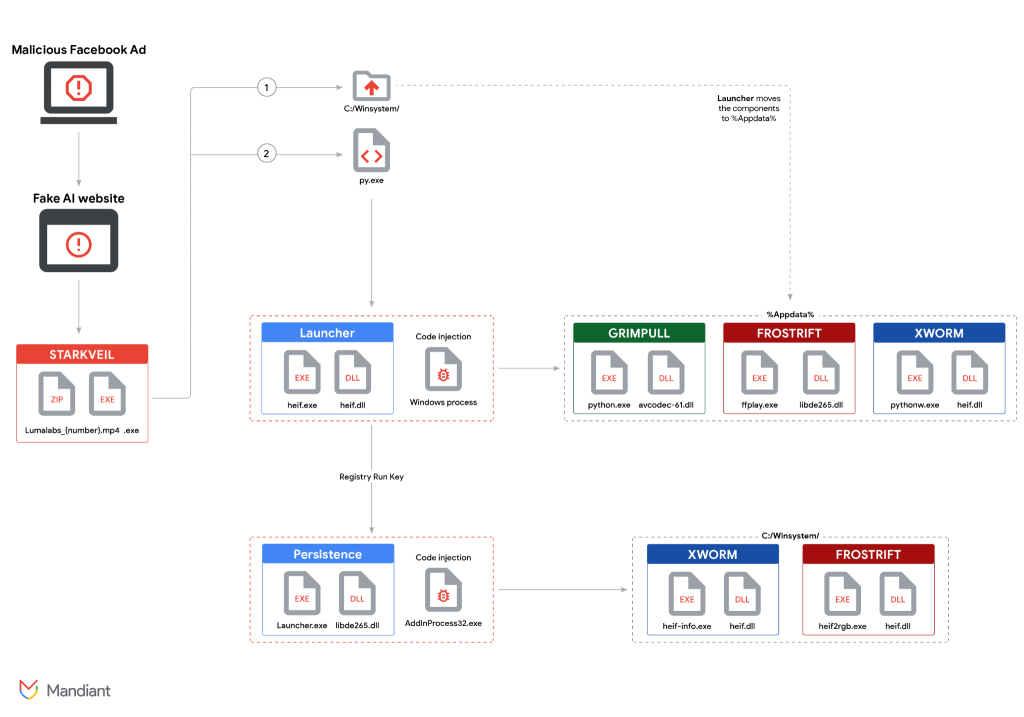
The primary malware, identified as STARKVEIL, is crafted in Rust and functions as a dropper for additional payloads, notably the XWORM and FROSTRIFT backdoors and the GRIMPULL downloader.
The campaign’s technical sophistication includes DLL side-loading, in-memory droppers, and process injection, all designed to evade detection by security products. Persistence is achieved via AutoRun registry keys, while modules like XWORM incorporate keylogging, browser extension scanning, and host reconnaissance.
FROSTRIFT’s capabilities extend to exfiltrating sensitive data, such as login credentials, cookies, and even details from password managers and crypto wallets. Information stolen from the victim’s machine is transmitted through Telegram and Tor-based channels.
An analysis of Facebook’s Ad Library revealed more than 30 unique malicious domains, with certain ads reaching over 2.3 million users in the EU alone.
Attackers frequently rotate domains and create short-lived ad campaigns to avoid takedowns, using both newly created and compromised Facebook accounts. LinkedIn also hosted similar attacks, with one domain, klingxai.com, responsible for up to 250,000 ad impressions.
Mandiant credited Meta’s threat detection and response teams for proactively removing many malicious ads and domains, aided by transparency initiatives like the Digital Services Act’s Ad Library.