Ukraine Targeted in SVG Phishing Campaign Leveraging CountLoader to Deliver Amatera Stealer and PureMiner Miner
- Novel attack vector: A phishing campaign is using malicious SVG files disguised as mailsv from the Ukraine Police to initiate a complex attack chain.
- Dual-payload delivery: The attack ultimately deploys Amatera Stealer for data harvesting and PureMiner for cryptocurrency mining.
- HTA loader: The CountLoader remote HTML Application is used, which was previously employed in campaigns with similar lures.
A sophisticated SVG phishing campaign is targeting Ukrainian entities with emails impersonating law enforcement officials. The attack delivers a dual payload of Amatera Stealer malware and the PureMiner cryptominer, enabling threat actors to conduct both data theft and resource hijacking on compromised systems.
Analysis of the Attack Chain
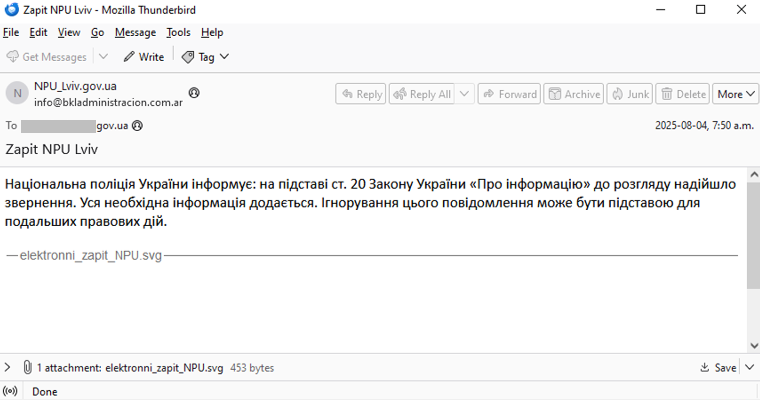
FortiGuard Labs discovered that attackers send emails impersonating the National Police of Ukraine, using a legal notice lure and an urgent tone to pressure the recipient into taking the bait.
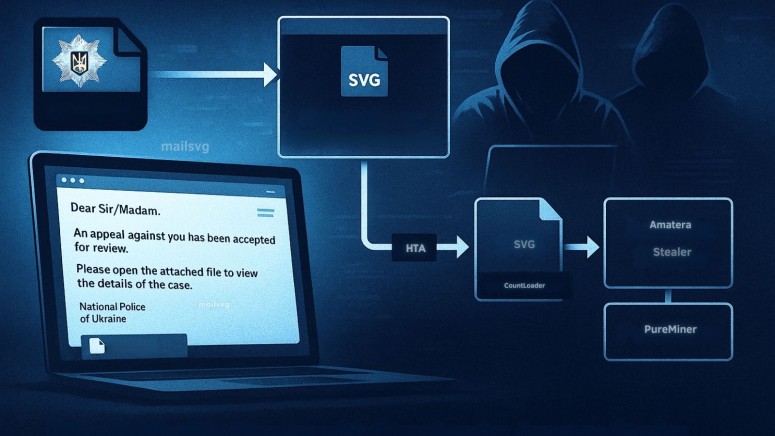
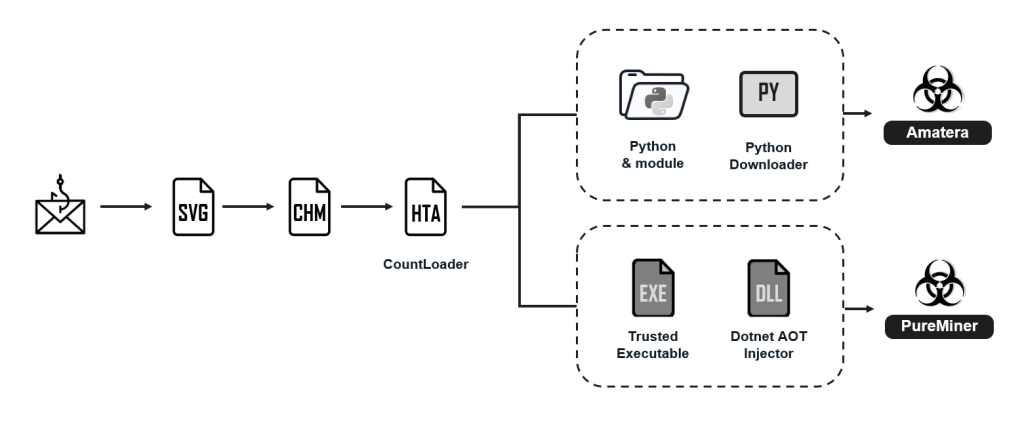
The attack begins when a recipient opens a malicious SVG file attached to the phishing email. This file contains embedded HTML that leads to a spoofed Adobe Reader interface that redirects the user to download a password-protected archive containing a Compiled HTML Help (CHM) file.
Executing the CHM file triggers a remote HTML Application (HTA), referred to as CountLoader, which establishes a connection with a command-and-control (C2) server to receive further instructions.
The novel CountLoader malware has been recently linked by SilentPush to major ransomware threat actors, including LockBit, BlackBasta, and Qilin, in a comprehensive analysis.
This loader is responsible for downloading the final malware payloads. The campaign uses fileless execution techniques to remain stealthy.
PureMiner is injected into a legitimate .NET Framework process using process hollowing, while Amatera Stealer is loaded directly into memory using the PythonMemoryModule library, avoiding writing the primary payload to disk.
Malware Payload Functions
Once deployed, the two malware variants perform distinct malicious activities. Amatera Stealer is a comprehensive information stealer designed to harvest a wide range of sensitive data.
It targets:
- system information,
- browser credentials from both Gecko- and Chromium-based browsers,
- application data from Steam and Telegram,
- cryptocurrency information from numerous desktop wallets.
Concurrently, PureMiner profiles the victim's hardware, specifically GPU specifications, to efficiently hijack system resources for cryptocurrency mining. This dual-threat approach allows attackers to maximize their monetization from a single intrusion, combining immediate data exfiltration with long-term resource exploitation.
This campaign is another example of the continuing cyberattacks in Ukraine that leverage multi-stage, evasive techniques.
Cybersecurity Experts Recommendations
Handling SVGs as either an image or a document depends on the context, according to Lionel Litty, Chief Security Architect at Menlo Security, who notes that this ambiguity can create confusion and a false sense of security. To stay on the safe side, it is best to treat SVGs as active content that is similar to HTML rather than as an image format,” said Litty.
“When interpreted as images, they are relatively safe. However, when interpreted as documents, they can contain JavaScript and can perform many of the same actions as an HTML document,” added Litty. “This includes making network requests, accepting user input, loading additional content via foreignObject, and triggering file downloads, as we see here.”
Attackers are using SVG or IMG formats to embed scripts or redirects that lead victims directly to adversary-in-the-middle websites and steal credentials and tokens in a single step, according to Rhys Downing, Threat Researcher at Ontinue.
“Security teams should prioritize the detection of dynamic script activity in non-traditional file types and review their controls for email-based file delivery,” said Downing. “Email defenses must be tuned to inspect emerging file types, and user education must reflect the reality that attackers will continue to innovate in how they package lures.”
“Loaders like CountLoader can swap payloads on the fly, such as stealers, miners, or even worse. Defenses need to key in on behaviors and move away from static signatures,” says advice from Certis Foster, Senior Threat Hunter Lead at Deepwatch.