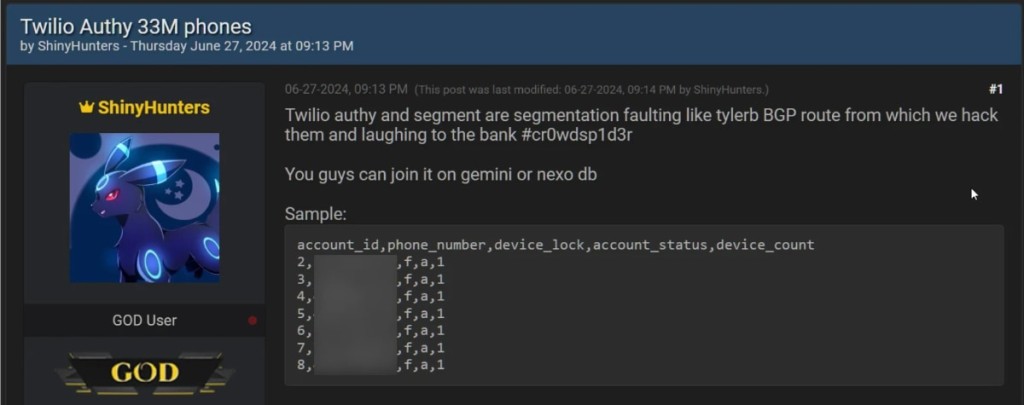
Twillio Confirms ShinyHunters Breach Exposing 33 Million Authy User Phone Numbers
- The infamous ShinyHunters cybercriminal group allegedly leaked 33 million phone numbers related to Twilio-owned Authy on a hacking forum.
- Twilio recently disclosed the data breach of the two-factor authentication app they own.
- Hackers were able to verify the phone numbers of two-factor app Authy users by exploiting an unsecured API endpoint.
U.S. messaging giant Twilio confirmed that cybercriminals were able to identify phone numbers of people who use the Twilio-owned two-factor authentication (2FA) app Authy via an unsecured API endpoint. The acknowledgment comes after the ShinyHunters hacker group took to the relaunched BreachForums website to boast leaking 33 million Authy user phone numbers in late June.
Twilio’s Authy is a code-generating mobile app for platforms that require multi-factor authentication (MFA). Twilio confirmed that threat actors managed to compile a list of millions of Authy user phone numbers using an unauthenticated API endpoint to verify the said numbers.
The leaked data also included Authy users' account IDs and some other non-personal details like account ID, phone number, account status, and device count, and the messaging company said Twilio’s systems or other sensitive data have not been impacted.
The ShinyHunters hacker group leaked a CSV text file with over 33 million rows, reportedly containing some 33 million phone numbers of people using Authy.
Twilio said they request all Authy users to update their Android and iOS apps (Android v25.1.0 and iOS App v26.1.0) to get the latest security updates as a precaution. Needless to say, Authy users are now potential victims of future phishing and smishing attacks, so their vigilance is also required.
In 2022, Twilio was hit by two attacks that were allegedly carried out by the same threat actors. At the time, Twilio said hackers successfully targeted over 90 individual Authy users and managed to steal real 2FA codes by registering additional devices on those victims’ Authy accounts.