Twenty Malware Apps Managed to Infiltrate the Apple App Store
- Zimperium discovered twenty Trojans in the Apple App Store and helped with their removal.
- The apps featured an in-built system to help them detect when they were being reviewed.
- Once they were free to act, they downloaded porn players and engage in loading hundreds of private iOS frameworks.
Thanks to Apple’s rigorous checking procedures, the discovery of malicious apps that managed to infiltrate the App Store is a rare occurrence. Still, this doesn’t mean that crooks are giving up or don’t try new methods to circumvent the App Store reviewing process. Zimperium’s zLabs unveiled that they have discovered twenty malicious apps that were uploaded by different developers, but were using similar discovery evasion techniques. The main trick in their sleeve was to hide malicious code in their core and to keep it dormant until the reviewing process is over.
The mobile security firm has only revealed the IDs of five of the apps, but they assure that Apple has been informed of the full list and removed all twenty of the apps by September 2019. The five apps that were published are the following:
- com.cxq.shijiemingzhu – id1227696557
- com.huatec.Bungee – id1471964427
- HAN.Handwriting – id1472712181
- com.huangqin.drink – id1475262538
- com.lifeline.HeYiJiaYong – id1475305024
The functionality and user interface of these apps are pretty simplistic, and their main goal isn’t to provide many features to the user anyway. Using timestamp verifications, hardcoded date checking and IP checks, the applications are capable of detecting when they’re under review, triggering a special "safe mode".
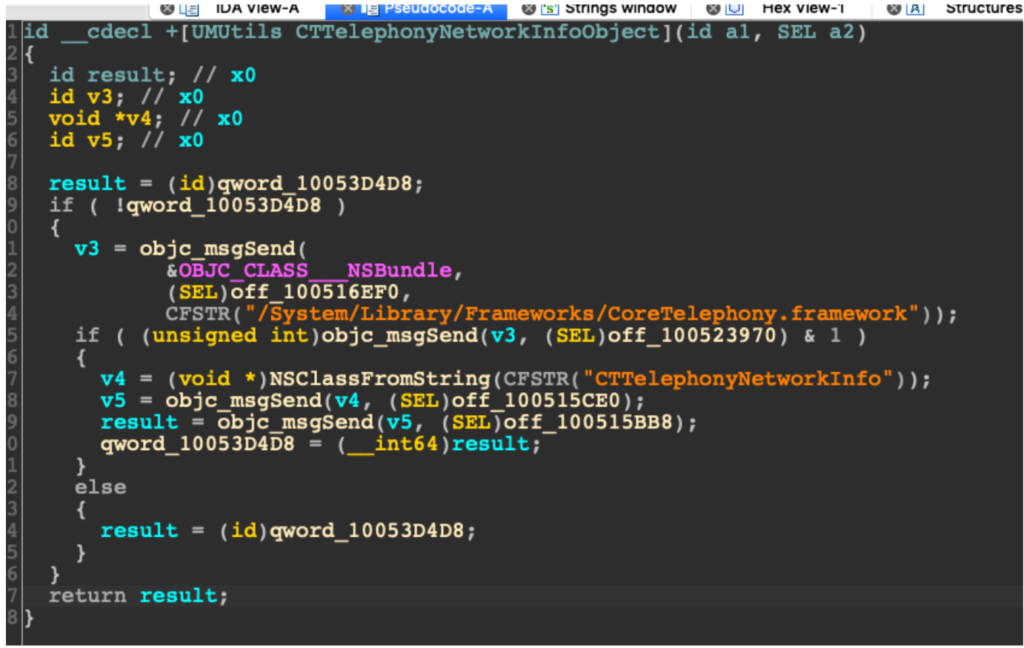
Once the reviewing process is over, the C2 server sends additional resources to the app, enabling it to run on “extended” capabilities. The zip files that are downloaded are giving extra functionality to the apps, with the most notable example being pornographic content players. This ensures that the app will stay on the device for longer, at least in most cases. In the background however, the app is loading the “CoreLocation” framework which is basically helping in the tracking of the user. In addition to this, the malware apps also initialize the CoreMotion framework and use the accelerometer to profile the user.
Source: Zimperium Blog
From then on, the apps dynamically load more than 400 private iOS frameworks, acting as full-fledged Trojans. Their action includes the spying of accounts, biometric data, cellular information, and even the backups of the user. This goes to show how important it is to use a mobile security application on your device. Apps can potentially transform fundamentally after they have been reviewed, so monitoring their activity at all times is crucially important if you want to stay safe.