The “Turla” Group Has Updated Its ComRAT Backdoor to Work Smart Through Gmail
- ComRAT version 4 is engaging in an unusual play with the Gmail web interface.
- The malware is checking the inbox on an arbitrary address to fetch new commands through attachments.
- There’s a high level of detection evasion, persistence, and data exfiltration encryption, so this threat is hard to uproot.
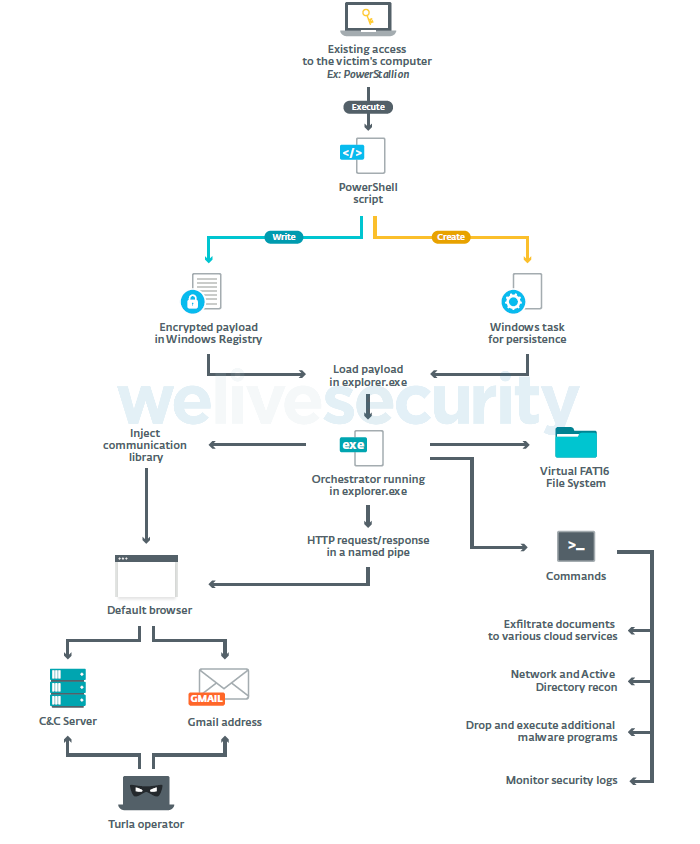
ESET researchers are reporting about an important update that they noticed on recent variants of the ComRAT backdoor (remote access tool), used by the “Turla” group. The particular team of cyber-espionage threat actors is well known for their skills, while their success in creating custom malware has been repeatedly documented. ComRAT itself first appeared three years ago and was upgraded several times until the most recent update that happened in January. Then, the actors pushed a new version that was almost entirely rewritten from scratch to incorporate new features. This version seems to have been authored years ago, but it was only recently spotted.
ESET knows that this latest version is the work of Turla. It uses the same internal name, same custom C&C protocol as in the previous version, and because parts of the infrastructure overlap with the Mosquito malware also attributed to the particular group of actors. Moreover, the distribution occurs through the PowerStallion backdoor and a customized PowerShell loader. They both are something that has been connected with Turla operations again in the past.
Source: We Live Security (ESET)
One notable thing that appears in this new ComRAT variant is the utilization of the Gmail web interface. ComRAT is using cookies that are hardcoded in its configuration for this Gmail connection to happen. It’s doing this as a method of communication with the C2 server, connecting with the Gmail web interface to check the inbox for any mail attachments of interest. These would be files that contain encrypted commands for the malware to use on the infected system and are sent from the operators using an anonymous email address of a free email provider. This is a very interesting feature that we don’t see very often in malware, showcasing Turla's skill level once again.
Apart from that, ComRAT uses a set of commands like “systeminfo” and “nbstat” to collect details, encrypts everything via RSA and AES, and uses ports 80 and 443 to exfiltrate the stolen information on cloud storage. The data is neatly bundled in a RAR archive, which is encrypted and password-protected, so the user cannot open it to inspect the contents. As for the detection, ComRAT evades it by storing its orchestrator in an encrypted form in the Registry, injecting the communication DLL into the default browser, and only decrypting what’s needed each time during execution.