Türkiye-Linked Hackers Target Kurdish Servers via Output Messenger Zero-Day Flaw Exploit
- A Türkiye-affiliated espionage actor has been exploiting an Output Messenger zero-day for more than one year.
- Attackers abused a directory traversal vulnerability in version 2.0.62 of the messaging app.
- They deployed advanced backdoors, accessed sensitive communications, and exfiltrated data.
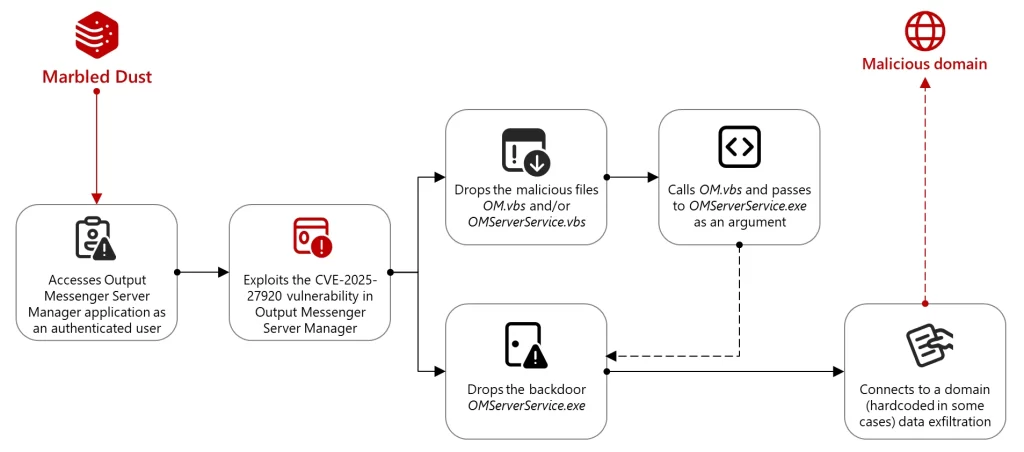
Türkiye-affiliated threat group Marbled Dust has been exploiting a severe zero-day vulnerability (CVE-2025-27920) in the messaging platform Output Messenger since April 2024. The attacks targeted Kurdish military servers in Iraq.
The attackers leveraged the vulnerability to deploy advanced Golang-based backdoors, intercept sensitive communications, and conduct widespread data exfiltration, according to a recent Microsoft security report.
The exploited vulnerability is a directory traversal flaw in the Output Messenger Server Manager that allowed authenticated users to upload malicious files to the server’s startup directory.
The attackers used these files, including a Golang backdoor masquerading as legitimate software, to gain persistent access to servers and exfiltrate data to a command-and-control domain.
They also employed DNS hijacking and typographical domains to intercept and reuse credentials, enabling further exploitation.
Upon detecting the vulnerability, Microsoft notified Output Messenger's developers, Srimax, who promptly issued patches to address CVE-2025-27920 and a secondary vulnerability, CVE-2025-27921. Organizations utilizing the platform are urged to immediately update to the latest versions (2.0.63 for Windows and 2.0.62 for Servers).
Marbled Dust utilized the vulnerability to infiltrate the server's architecture, exfiltrate data, and impersonate users. Malicious bash scripts and backdoor executables ensured control over compromised servers.
Communications were established with a hardcoded domain for data exfiltration and execution of remote commands.
Previously tied to DNS-based attacks, Marbled Dust’s use of a sophisticated zero-day exploit suggests an elevation in their technical capabilities, signaling a new operational urgency. Their activity, aligned with Türkiye's regional interests, targets government and military institutions across the Middle East.
Organizations are encouraged to examine their systems for signs of compromise using advanced hunting tools provided by security vendors like Microsoft and ensure compliance with vulnerability management best practices.