Truecaller Denies Breach and Data Leak Despite Evidence
- Cyble discovered a dump of 2019 Truecaller user data being offered for sale on the dark web.
- Truecaller denies any security incident and says the data was labeled to appear as theirs.
- A potential explanation could be that hackers exploited a vulnerability in the API of the service, scraping user data en masse.
Truecaller, the spam-call blocking app used by 250 million people (mostly in India), has issued a media statement regarding recent stories about their user records being on sale on the dark web. The company flat out denied the allegations, saying that there was no breach in its systems and that what was discovered is probably a compilation of phone numbers leaked elsewhere, with the Truecaller stamp put on it. As a company’s spokesperson mentioned in their statement, the actors would do that because it adds credibility and value to the data, making the listing easier to sell.
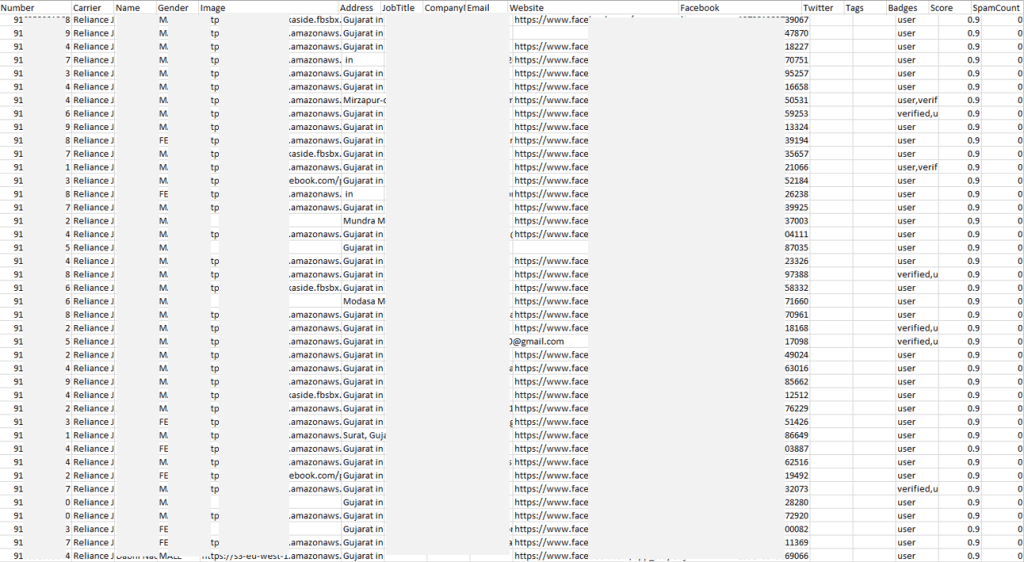
The revelation of the sale came from the American cybersecurity firm “Cyble,” who specializes in the monitoring of the deep and dark web. As the firm reported a couple of days back, an actor with the nickname “TooGod” has put up 47.5 million Truecaller user records for sale on the dark web. These contain details such as full names, email addresses, mobile numbers, Facebook IDs, age, city, gender, telecom service provider, and more. The dump’s price was set at $1,000, and the first validation tests conducted by Cyble’s team proved that the information was real. In fact, it was even well organized, too, featuring separate folders for users that come from different India states.
Source: Cyble
Thus, Cyble has added the data dump on its “AmIBreached” search engine and informed the public of their find. Just yesterday, the same actor added another dozen of listings coming from breaches on other entities, totaling 600 million records. That said, it looks like the hacker or data broker is a reputed seller offering a respectable number of listings that have been verified and confirmed. So, the denial from Truecaller may come either as a way to play down the event or because they honestly haven’t sustained a data breach.
Source: Cyble
One possible explanation about what may have happened could be that a vulnerability on a third-party API allowed hackers to scrape Truecaller data in the massive numbers that we now see. In this case, the app’s team wouldn’t notice anything weird going on, so a denial of any security issues would come naturally. That said, it is worth mentioning that Truecaller had security issues with its own API before. As an Indian security researcher discovered back in November 2019, it would be possible to inject a malicious link as a profile URL on the app by exploiting a flaw in its API.