“Tropic Trooper” Is Finding Ways to Hack Into Air-Gapped Military Systems
- A known and skillful threat actors group is now targeting networks in the Philippines and Taiwan.
- The hackers are engaging in cyber-espionage by dropping their malware payload on USB drives.
- The way the actors move, it is particularly hard to detect the infections and their network activity.
Finding your way inside military networks and systems that are shielded from the outside world isn’t easy. That doesn’t stop threat actors from trying, though, and for the most sophisticated ones, trying equals succeeding. According to a recent report from Trend Micro, the threat group known as “Tropic Trooper” is currently infiltrating the physically isolated networks of the Philippine and Taiwanese armies, as well as many government institutions, military hospitals, and national banks in these countries. “Tropic Trooper” has been active since 2011, engaging in information theft and cyber-espionage, and they are continuously improving their methods and arsenal.
Source: Trend Micro
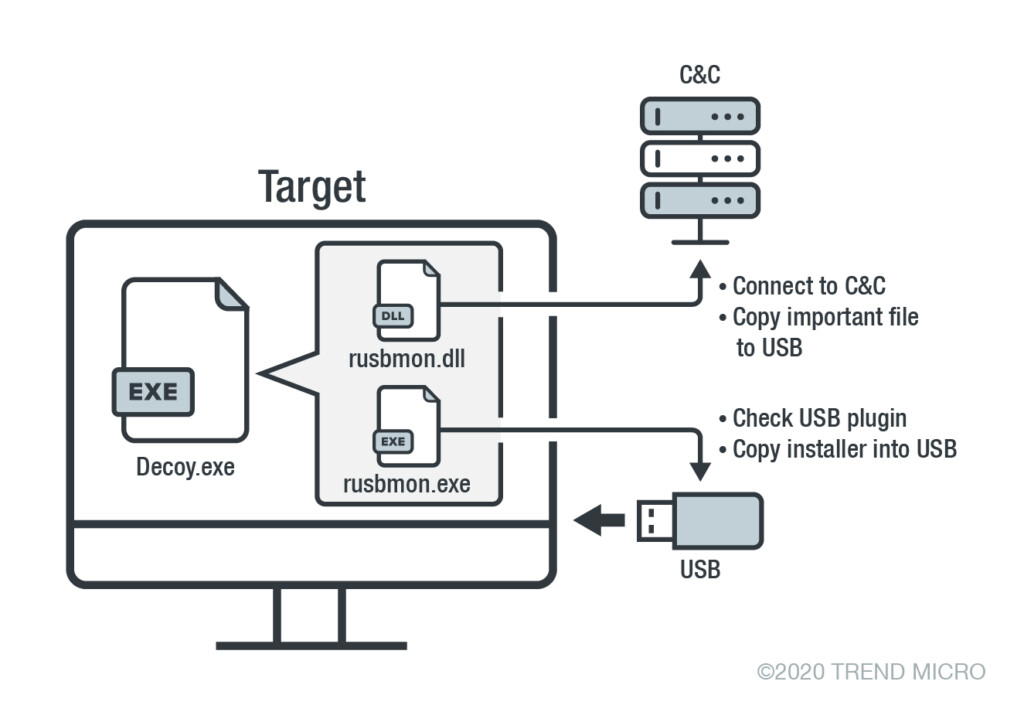
The way that the hackers are moving right now is through potentially exploitable points from where they can jump onto the military networks. The main method of infiltration is through a USB malware called “USBferry,” of which the Trend Micro team sampled three different versions for analysis. This is another indication that the actors are actively working on the improvement of the malware. USBferry needs a USB pen drive to be connected on the target machine, as this is where it drops the payload to. Moreover, this is a very reliable way to establish a presence and hope to infect even more systems in networks of the same organization and/or level.
Source: Trend Micro
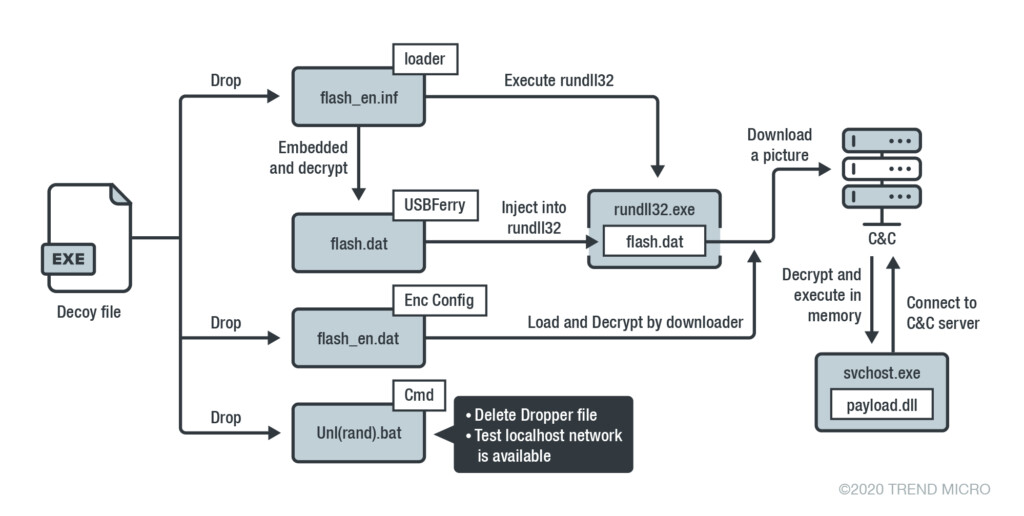
The Tropic Trooper malware is acting like a worm, infecting air-gapped machines by ferrying a malware installer on the network. The loader is a DLL file that is dropped from a decoy “.exe” file, following an infection procedure, as shown in the below diagram. The “USBferry” malware is checking the network for other connected machines to jump to, while at the same time, it collects information from the infected system and stores than right on the USB drive. Then, this information is bundled and exfiltrated to the C&C server.
Source: Trend Micro
The hackers are also using several backdoors that are hiding their routings through steganography to avoid detection from AV solutions. Other tools that are used by Tropic Trooper include a Command-line remote control listener/port relay utility, various backdoor execution loaders, port scanning tools, self-deletion tools, and more. Finally, the researchers have noticed the use of invisible web shells that would make the realization of the infiltration very hard, if not impossible, while also hiding the C&C server location. Surely, the Tropic Trooper actors haven’t stayed in the shadows for nine years thanks to luck.